- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: Cisco ISE (user certificate ambiguity error)
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-26-2020 04:04 AM
Hi All,
Receiving an authentication error in ISE (2.x) relating to user certificate ambiguity.
Setup - AD Join connector configured for user and machine in several domains.
Clients - Win 10 - EAP-TLS for machine and user network access.
Issue:
Single domain user account in DomainA or DomainB works fine, but when trying to auth a client with identical user accounts in DomainA&DomainB authentication is rejected due to multiple matching records "resolve certificate identity ambiguity using certificates match".
Question - How to accommodate a user in multiple domains for authentication?
Cheers,
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-26-2020 07:03 PM
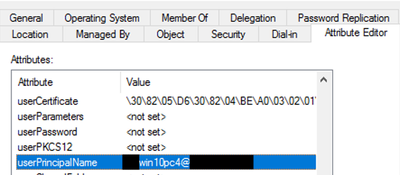
In addition to @Cristian Matei's comments, another way to resolve ambiguity issues when your have a user that exists in multiple domains would be to ensure you are using an identity value in your Certificate Authentication Profile that includes the domain name.
Typically, the CN would include just the computer or user name but options like UPN or Email would include the domain.
You would need to ensure, however, that the separate certificate templates in ADCS used to enrol both Computers and Users includes the value specified in the Cert Auth Profile.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-26-2020 06:10 AM - edited 03-26-2020 06:13 AM
Hi,
1. The simplest solution would be to create some conditions in your authentication policy, thus based on the attributes of the incoming RADIUS request, you know to which domain the user belongs to, and configure ISE to look for a specific join point.
2. Have you set the "Match Client Certificate against Certificate in Identity Store" to "Only to resolve Identity Ambiguity" or to "Always perform binary comparison"?
Also, take a look at this bug and upgrade to a proper version and patch level of ISE.
Regards,
Cristian Matei.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-26-2020 07:03 PM
In addition to @Cristian Matei's comments, another way to resolve ambiguity issues when your have a user that exists in multiple domains would be to ensure you are using an identity value in your Certificate Authentication Profile that includes the domain name.
Typically, the CN would include just the computer or user name but options like UPN or Email would include the domain.
You would need to ensure, however, that the separate certificate templates in ADCS used to enrol both Computers and Users includes the value specified in the Cert Auth Profile.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-27-2020 03:33 AM
Is the below necessary?
Use Explicit UPN
To reduce ambiguity when matching user information against Active Directory's User-Principal-Name (UPN) attributes, you must configure Active Directory to use Explicit UPN. Using Implicit UPN can produce ambiguous results if two users have the same value for sAMAccountName.
To set Explicit UPN in Active Directory, open the Advanced Tuning page, and set the attribute REGISTRY.Services\lsass\Parameters\Providers\ActiveDirectory\UseExplicitUPN to 1.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-29-2020 03:58 PM
I'm no AD expert but, as I understand it, the advanced tuning for the Explicit UPN would be more for solving ambiguity issues within a single domain. I don't believe this would be required with your use case for multiple domains.
See the following link for more information about iUPN versus eUPN:
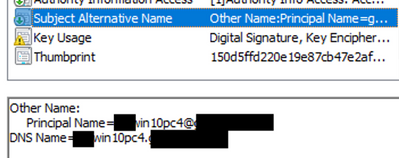
AFAIK, however, the UPN is not automatically generated for a computer account by default. If you intend to use the UPN value in the certificate for both Computers and Users, you will likely need to make sure the UPN attribute is set for the computer account during or after the domain join and before the certificate is enrolled so the value is populated in the certificate SAN.
Example:
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide