- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: client cannot use MAC authentication with ISE
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-02-2018 08:52 PM
Hi , PC want to use MAC authentication with ISE but fail , i made the document for detail process and result (as attachment) , Could you help me to figure it out ? thx
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-07-2018 08:22 AM
Following NAD Profile settings should allow you to match against wired MAB. However, it does not have wired 802.1X, since I am not sure what attributes gets sent from D-Link during 802.1X. Contact me directly at howon@cisco.com and I can assist with creating the NAD profile that works with both MAB and 802.1X.
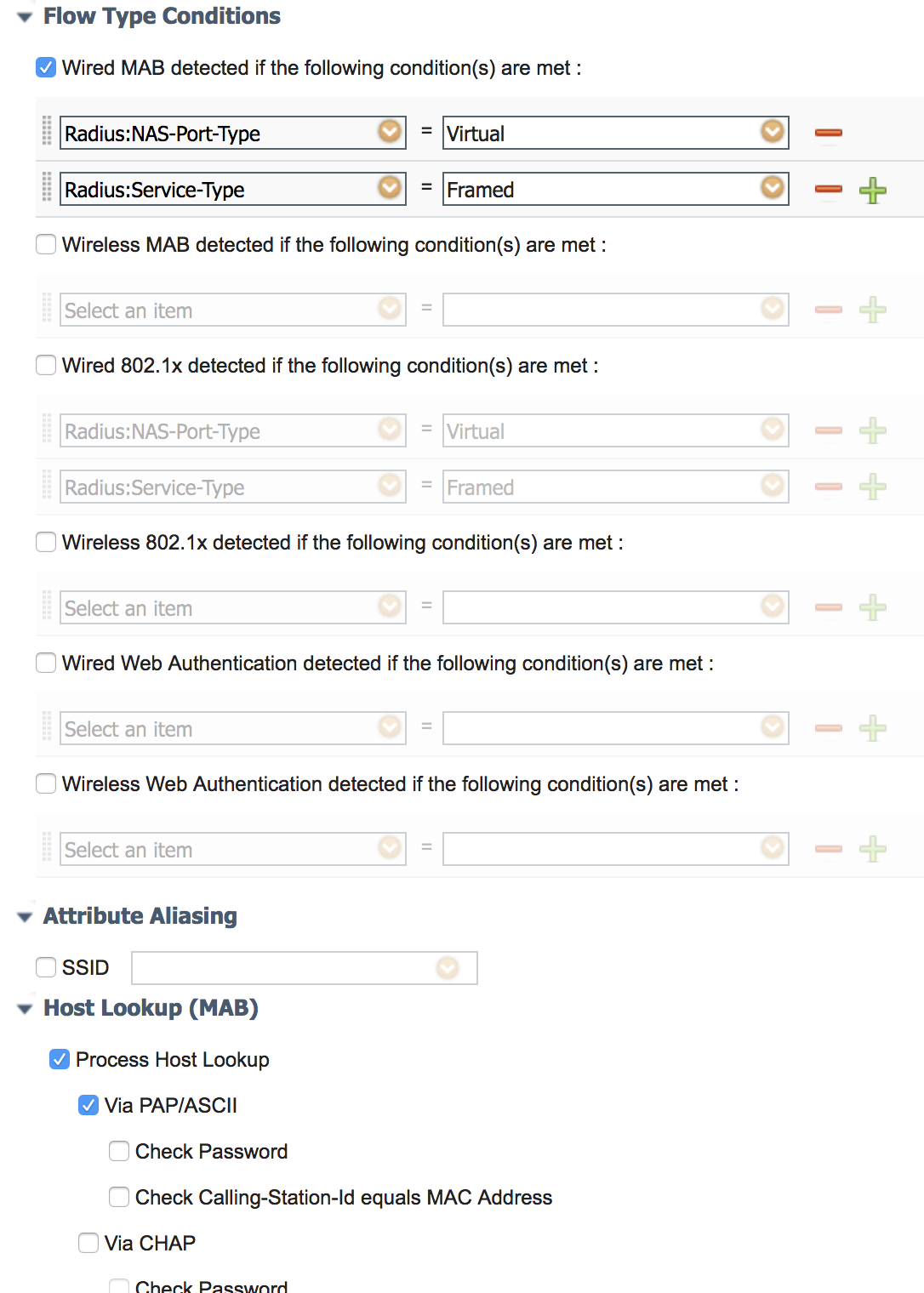
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-02-2018 10:48 PM
The trick here is on authentication rule for MAB change if user not found continue
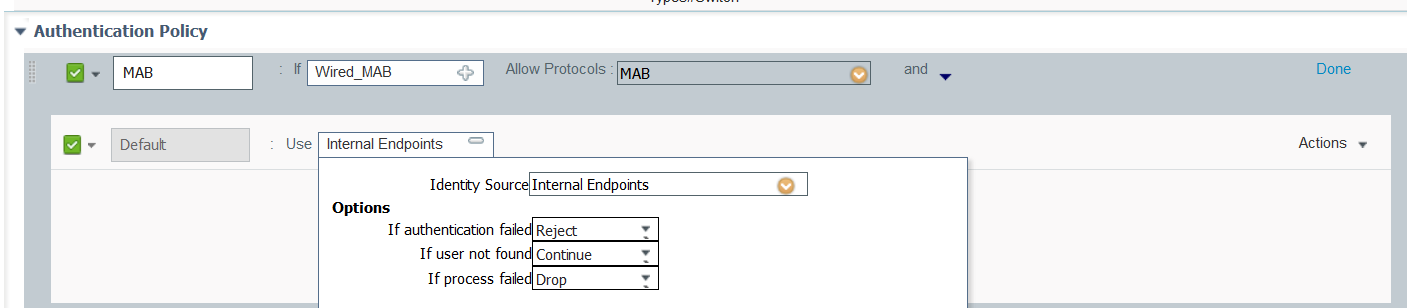
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-02-2018 11:25 PM
thanks for your reply , i adjust setting follow your suggestion :
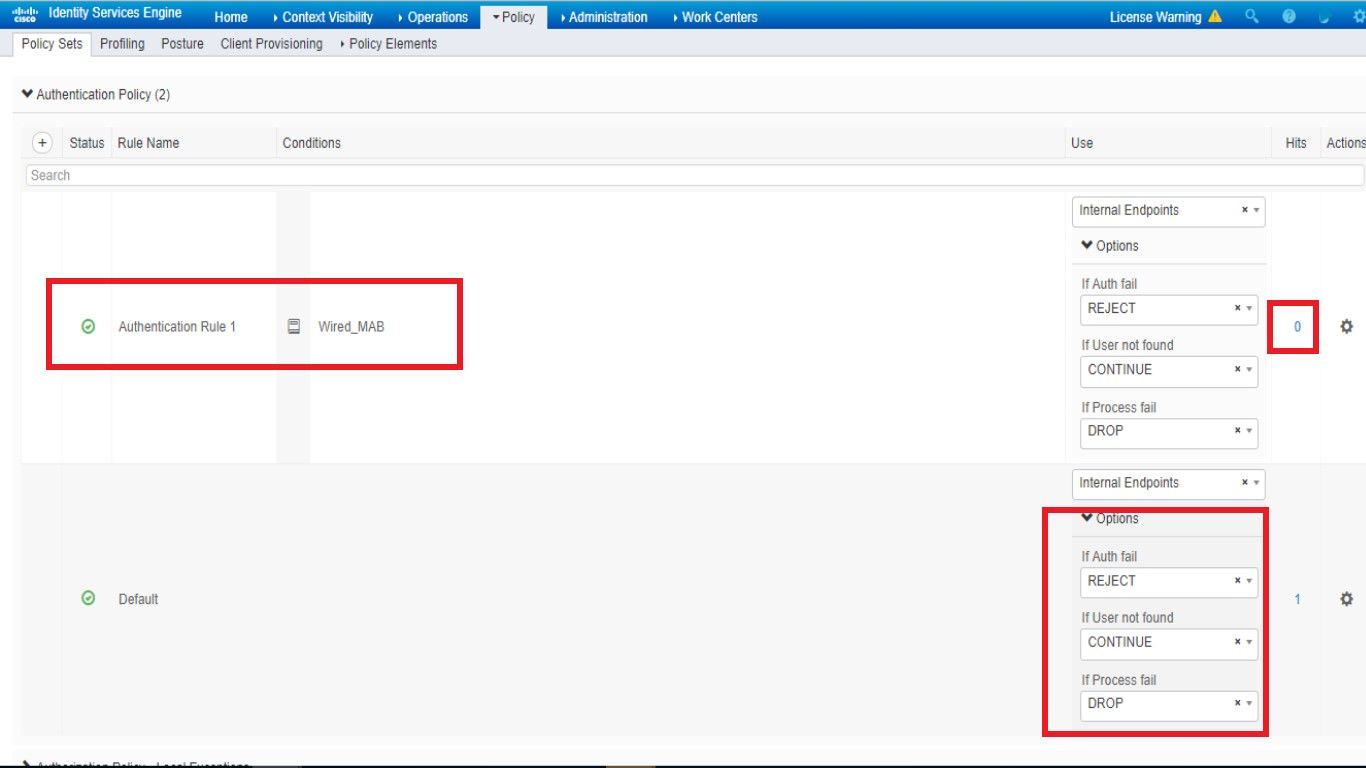
i add one more policy in authentication for "wired_MAB" but i got the same result , and i found the hits=0 , that is meaning this policy does not active when communicate period between switch & ISE , right ?
do i miss something to configure ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-03-2018 04:43 AM
Hi,
Please try attached NAD profile.
1. Import attached NAD profile into your ISE ( under Administration > network resources > network Device Profiles)
2. Configure the network device using this NAD profile in network devices page
3. Change in authentication policy options “If user not found > Continue”
4. Do MAB authentication
HTH,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-03-2018 03:08 PM
I think the profile that Salomon uploaded looks correct. In my quick analysis the Service-Type was originally not being matched. And also the hard coding of MAC addresses in profiles is a no no. With the new device profile attached, you can use a Normalised Smart Condition "Wired_MAB" which will now include the new DLINK Device Profile. Create a Policy Set Condition using Wired_MAB as your condition and that's that.
If the MAC address is in the Endpoint Identity Group then return access-accept (and remember that the Result Policy either has to be the same Vendor Type (i.e. DLINK) or vendor neutral (i.e. remove the vendor icon). The default PermitAccess should do the job (unless of course you need other attributes returned).
As for the Continue if not found - that is a logic trick that we use all the time in Guest redirection, where it is IMPERATIVE that every request passes, because you HAVE to force the user to a portal even if MAC address is unknown.
In your case I don't know if that logic applies, since I think you only want to send an access-accept back to your switch if, and only if, the MAC address is in ISE. Is that right?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-03-2018 08:01 PM
Thanks for your reply , as your mentioned "In your case I don't know if that logic applies, since I think you only want to send an access-accept back to your switch if, and only if, the MAC address is in ISE. Is that right? "
yes , and do you know where i can configure this MAC can accept in ISE side ?
thx
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-03-2018 10:09 PM
Here is how you load static MAC addresses into an Identity Group. Click on each image because of the resolution is reduced in this forum view.
You add the MAC addresses via Context visibility
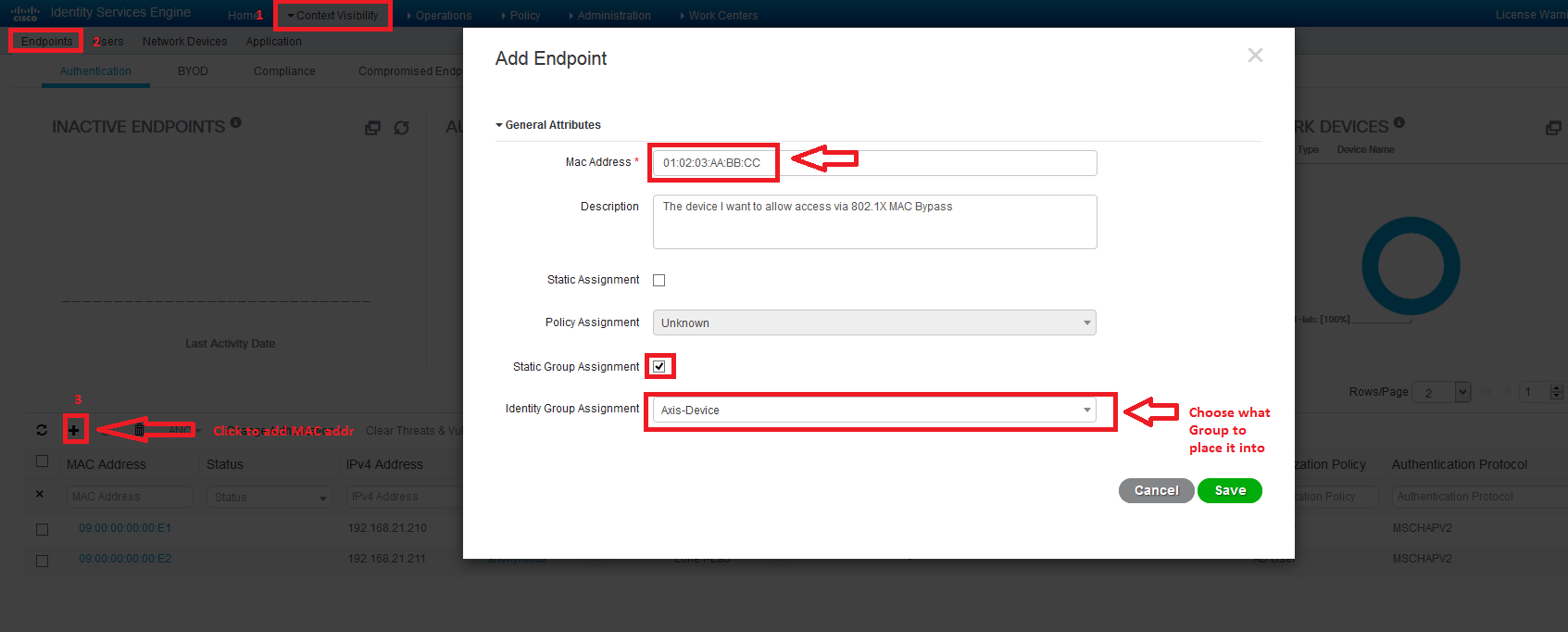
You can also verify that they are in the Endpoint identity Group that you have chosen. Please don't use my example of Profiled/Axis-Device. Choose something meaningful off the root Group, like, MAB-Printers or whatever.
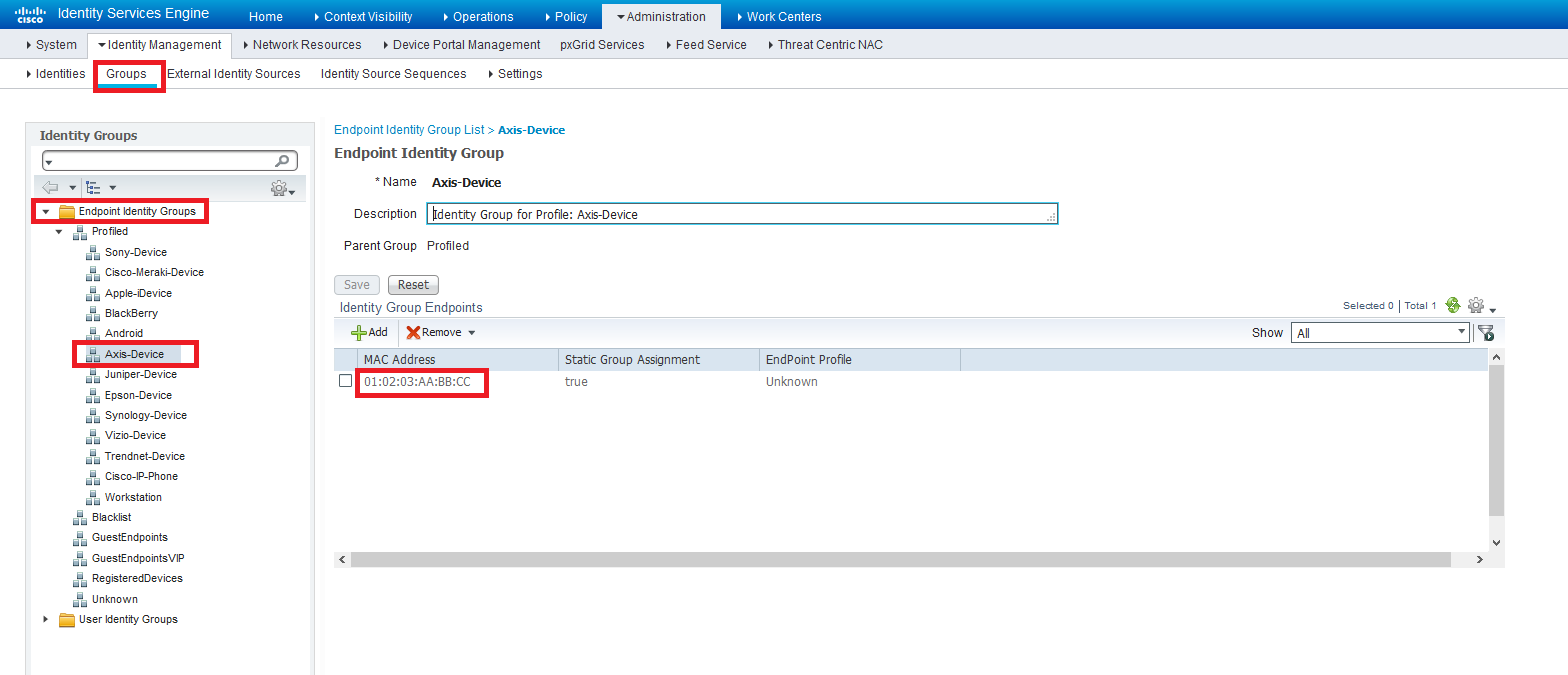
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-03-2018 11:54 PM
thanks for your reply , my PC MAC existed in Endpoint list :
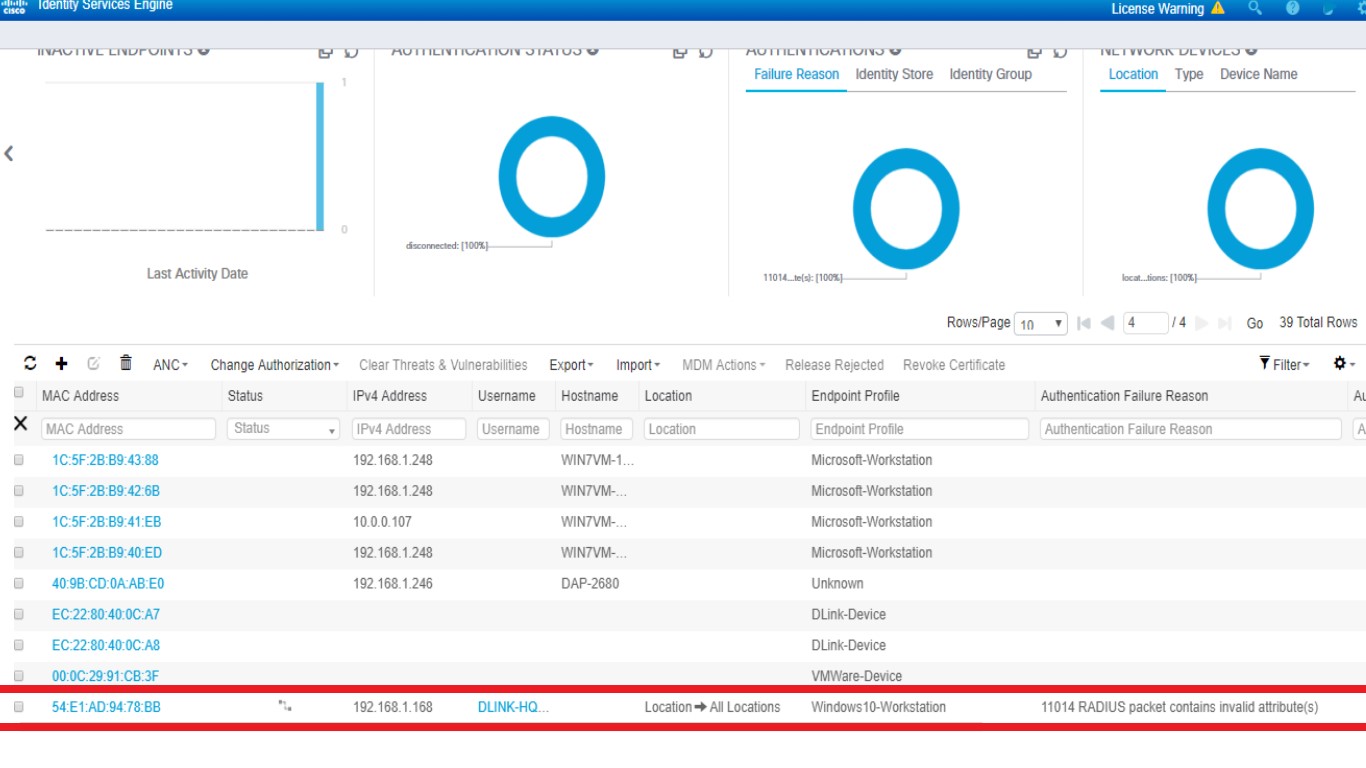
and existed in identity group :
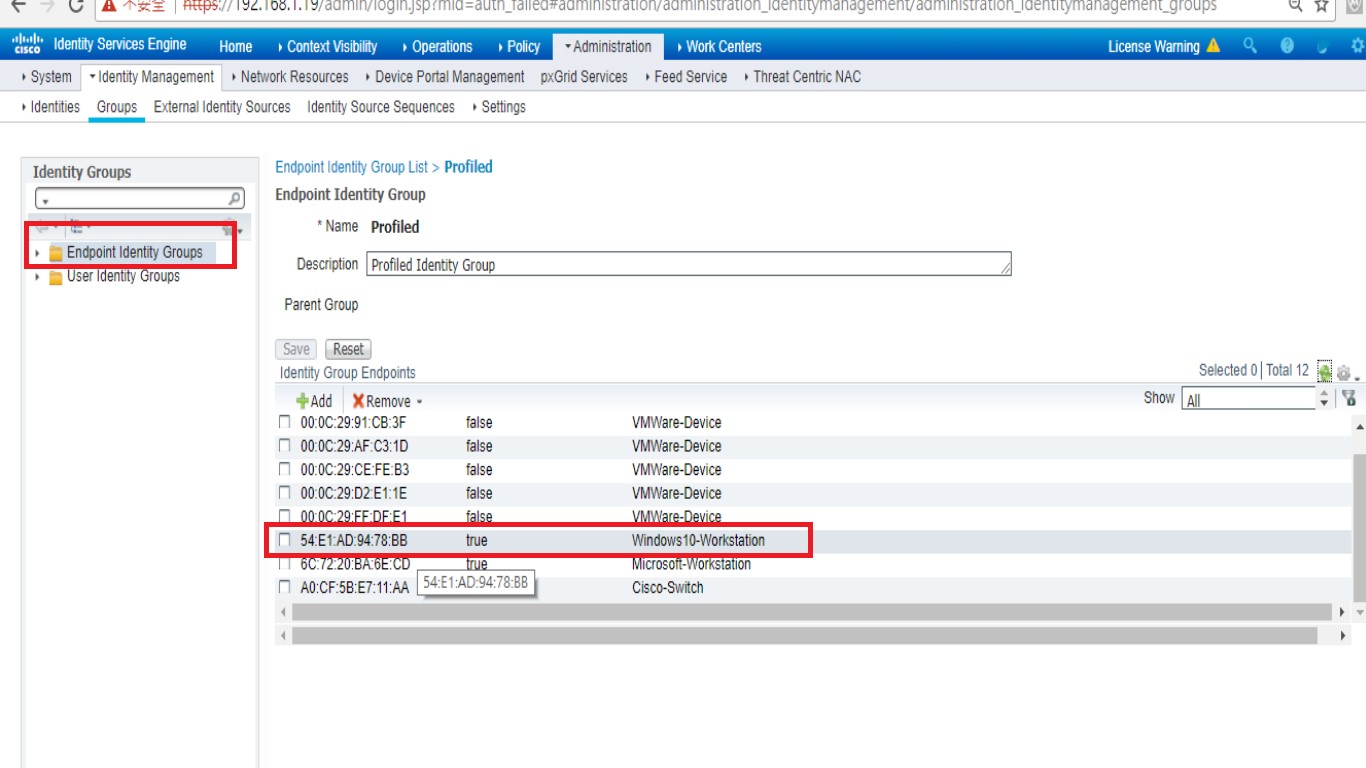
but testing result is still fail ,
above settings are meaning this MAC already be accept in ISE !? or any other configurations i need to adjust ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-03-2018 07:58 PM
thanks for your reply , but after i imported DlinkWired switch NAD profile , the testing result is still fail and got the same log :
verview
|
Authentication Details
|
Other Attributes
|
Result
|
i have some questions want to confirm :
a. i add one more authentication entry like this :
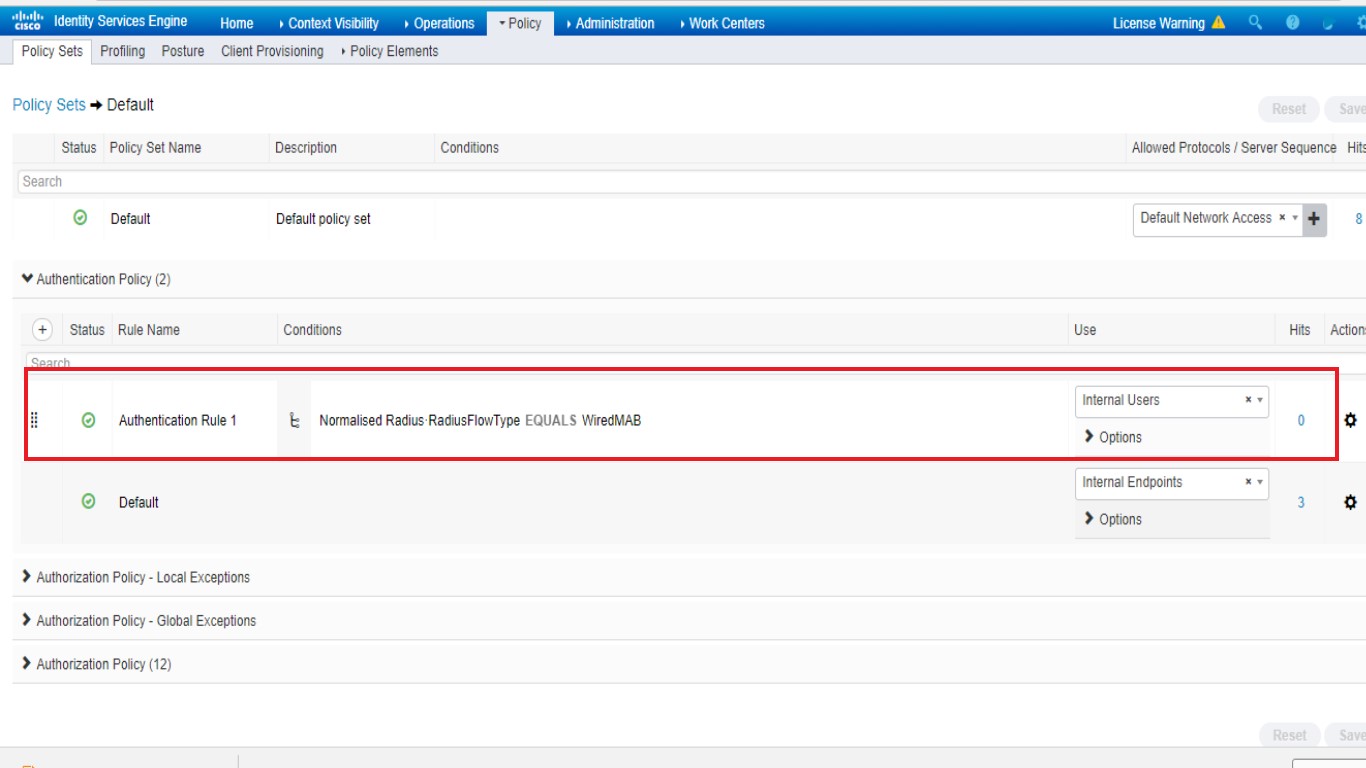
but the hits still display zero , do i need add this policy ?if yes , what is wrong with this setting ?
b. Where i can configure PC MAC can accept in ISE server ?
for example , if i testing this function between switch & ISE server , i should configure "54E1AD9478BB Auth-Type := Accept " in user file of freeRadius server , then it can work fine.
thx
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-03-2018 09:53 PM
It looks to me that the shared secret configured on the network access device is not matching with the NAD configuration on ISE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-04-2018 11:38 PM
The endpoint ID is empty so it seems the auth request does not have calling-station-id, which is likely why it not matching the Wired MAB condition.
Please try a wired capture to confirm what attributes are sent in the auth requests and then modify the NAD profile and the network access policy set accordingly.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-06-2018 06:49 PM
thanks for your reply .Yes, my original auth request does not have calling-station-id , and after i change another switch that has calling-station-id , it's work , so i have some questions like this :
1. When i want to run MAC aurh with ISE , it's only support that Pkts include ""calling-station-id" !?
2. Or it also support without "calling-station-id" ? if yes , what's configurations i should adjust ?
to modify NAD profile in wired MAB detected? or in wired 802.1x detected? and what's content i need to configure ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-06-2018 07:10 PM
ISE may authenticate without calling-station-id in the requests. However, ISE features, such as CWA or posture, would not work without calling-station-id. ISE session directory is keying off calling-station-ID in most cases.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-07-2018 08:22 AM
Following NAD Profile settings should allow you to match against wired MAB. However, it does not have wired 802.1X, since I am not sure what attributes gets sent from D-Link during 802.1X. Contact me directly at howon@cisco.com and I can assist with creating the NAD profile that works with both MAB and 802.1X.

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-11-2018 01:18 AM
it can work after follow your setting!! Thanks u very much!!
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide





