- Cisco Community
- Technology and Support
- Security
- Network Access Control
- EAP and iPhone
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
EAP and iPhone
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-11-2013 03:41 AM - edited 03-10-2019 08:17 PM
Hi,
I have a BYOD setup that is working well except one thing that is enoying, I cant get iOS device's to trust the ISE server certificate.
Tested on 2 iPads and 2 iPhones.
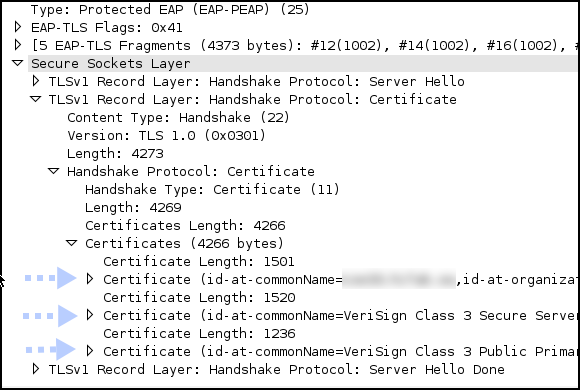
When runing Wireshark from a Mac I can see the certificate chain in the TLS packet coming from ISE and my Mac is accepting this with out problem, same for a Win 8 test machine.
In this document under The Trust Chain, Apple writes:
'The first time the user joins a device to an 802.1X-protected network, the device will prompt the user to trust the server’s certificate'
Could it be that iOS devices ignore the cert. chain in a EAP packet?
- Labels:
-
AAA
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-13-2013 03:38 PM
May be running into this
ISE-Apple iOS devices are asked to accept the "Not Verified" Certificate
Symptom: During self provisioning of iDevices, the user is asked to accept a "Not Verified" certificate from ISE. Conditions: Certificate is signed by a well-known CA. Workaround: None
Looking to have this fixed by 1.2
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-14-2013 03:57 AM
Yes, might be this bug. A bit hard to verify without an ISE v1.2.
For reference, if I use the dual SSID setup and have the iPhone do provisioning via Guest Flow and the portal page the certificate is trusted. Same certificate for HTTPS and EAP.
Amjad: Yes Verisign root is (should be) on iOS devices. List of iOS root certificates: iOS 5/6 iOS4.x
Regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-14-2013 08:17 AM
The trusted CAs only come into effect when navigating to web portals. Because the user is actually initiated a browser session to a secure site where the url is entered.
With eap authentication this behavior is different. When a user sends their credentials the supplicant on the iphone automatically prompts the client to validate the radius server identity. It will also show you that the identity is trusted, but it will still prompt the user by informing them that their credentials are being forwarded to a specific radius server.
You can also verify this by using a windows machine, if you set the supplicant to "validate the server certificate" but leave the certificate entries unchecked, you will still be prompted to validate the radius server's identity.
Thanks,
Tarik Admani
Sent from Cisco Technical Support iPad App
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-13-2013 09:47 PM
Hi,
I have found this to be common when authenticating to any dot1x network for the first time, and then again if you "forget the network". The apple devices and even some windows devices will almost always ask you to "validate the server certificate". The reason this is the case is that the user isnt browsing to the radius server, instead the wireless controller is performing the eap conversation and it's up to the client to know if they trust the radius server as the server on their network.
With windows in an enterprise the solution is easy, just write a group policy so that the server settings are built.
For BYOD deployments it is best to send all BYOD users an email walking them through the provisioning steps since this common for all peap handshakes.
Thanks,
Tarik Admani
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-13-2013 10:22 PM
Tarik: quick question.
Shouldn't those iOS devices have a list of trusted CAs? If Versign root CA cert is by default on the iOS device (since the server cert issuer is verisign as appear in the wireshark snapshot) then the iOS device should not complain.
If the cert verification message although the device has the CA root cert already then the bug Robert mentioned above makes more since to be the root cause of this issue.
Regards,
Amjad
Rating useful replies is more useful than saying "Thank you"
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide