- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: EAP-TLS - Client still not trust ISE PSN certificate
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-15-2023 01:33 AM
hello Guys,
I want to ask you if you meet similar problem to my. I have implemented EAP-TLS for wireless clients. Simple topology:
Client -> WLC -> ISE - implemented 802.1x EAP-TLS
My problem is that when client click connect to SSID, he always receive warning that certificate which is sent by PSN is not trusted, but it is not possible. I have all certificate chain in my Trusted Store Certificate (Root, SubCA, Intermediate CA) in client machine.
I also tried to add PSN certificate to Trusted Store but it not help.
PSN certificate has Client and Server Authentication atrribute in Enhance Key Usage
Also in SAN field we have DNS and IP entries.
I don't have any idea why client still not trust PSN certificate. Any suggestion ?
Solved! Go to Solution.
- Labels:
-
AAA
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-17-2023 08:28 AM - edited 11-17-2023 08:29 AM
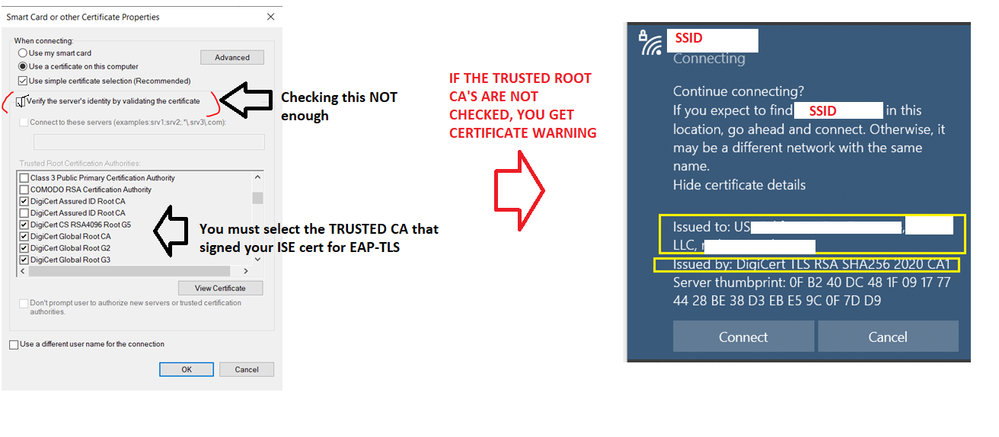
Microsoft implemented security changes on Windows 10 and 11 where you MUST checked the TRUSTED ROOT CERTIFICATE CA's in your wireless profile (manually created of distributed via GPO) and not just check the "validate server certificate" box. Without that, no matter you have the Trusted CA Root listed by default in your computer the certificate warning would appear. I had a conversation with a Microsoft support tech about it because our Win 11 laptops were giving us those certificate warnings. See attached pictures about it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-15-2023 09:43 AM
This is 100% a client problem. What are the clients? How are you trusting these certificates on the client? Who issues the ISE EAP certificate? Internal PKI our public.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-15-2023 10:37 PM
Is this an Apple iOS device, or Windows? I could be wrong, but with Apple iOS, you will always get the cert warning even if you have manually added the ISE CA chain into the device (through something like Apple Configurator). I have not done this in a while, but I also believe that if Apple devices are MDM managed, then this phenomenon doesn't happen.
With Windows clients this is never an issue, if the supplicant is configured correctly - you have a lot of control and visibility over this, as compared to Apple.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-16-2023 03:06 AM
Thanks for your reply.
Problem solved. We have Windows machine, and we don't know why but supplicant wifi (build-in) can't verify certiface even if it has all root CA in Trusted Store.
We solved this problem by creating WLAN Profile on GPO and set by mark which certificate need be trusted.
After pushing policy to PC, we not observe aby info that client can't verify PSN cert
We assume that native supplicant has a problem to find right CA in Trusted Store
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-17-2023 08:28 AM - edited 11-17-2023 08:29 AM
Microsoft implemented security changes on Windows 10 and 11 where you MUST checked the TRUSTED ROOT CERTIFICATE CA's in your wireless profile (manually created of distributed via GPO) and not just check the "validate server certificate" box. Without that, no matter you have the Trusted CA Root listed by default in your computer the certificate warning would appear. I had a conversation with a Microsoft support tech about it because our Win 11 laptops were giving us those certificate warnings. See attached pictures about it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-20-2023 02:53 AM
ajc - thanks for your explanation! One more question: you said "I had a conversation with a Microsoft support tech" - when you spoke with Microsoft ? And what they said ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-17-2023 08:32 AM
BTW, we had a SIMILAR issue with our MDM managed IPADs where we HAD to add the intermediate trusted CA to the profile used for EAP-TLS, otherwise we got a certificate warning no matter we had the ROOT Trusted CA in those IPADs.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide