- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: Find a condition to authenticate to the correct domain with TEAP
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-25-2021 06:05 AM - edited 11-25-2021 06:19 AM
Hi,
I have several AD domains on my ISE deployment
Depending on the AD domain, the Authentication Policy to access the network may change
- For some domains, we use EAP TLS only (machine Authentication only)
- And for 1 domain we use TEAP (machine certificate + username/pwd for user)
In the Authentication Policy, I can make a condition to match the Certificate Issuer and then check in the right Certificate Profile for Authentication
Is it possible for TEAP authentication to find a condition that would authenicate to the specified Joint Point and not asking to all the joint points? (we can not use network device as a differenciator)
Actually my concern is to send the Authentication to the correct Authentication server, without the need to go through each Join Point.
Thanks for any idea
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-25-2021 11:52 AM
Hello @REJR77
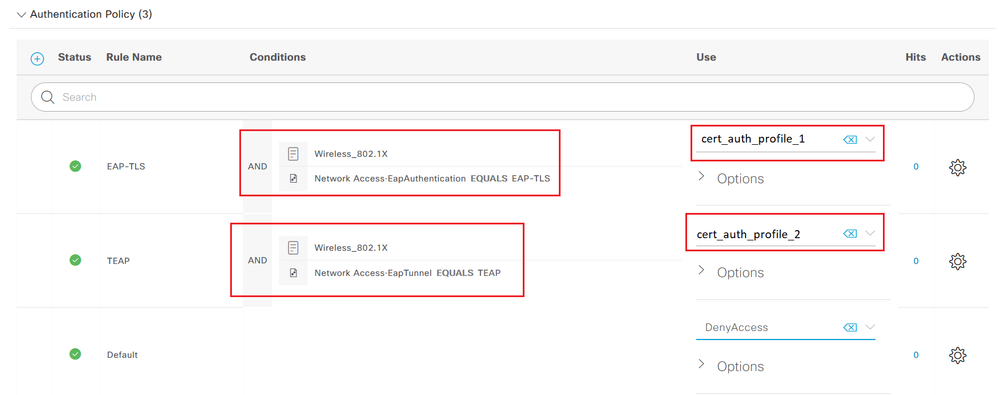
I do this all the time. In the Authentication section select the Certificate Authentication Profile depending on the EAP Method/Tunnel.
The Name of the AD Join Point is set in the Certificate Authentication Profile.
Example below
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-25-2021 11:52 AM
Hello @REJR77
I do this all the time. In the Authentication section select the Certificate Authentication Profile depending on the EAP Method/Tunnel.
The Name of the AD Join Point is set in the Certificate Authentication Profile.
Example below
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-25-2021 11:30 PM - edited 11-25-2021 11:41 PM
Hello @Arne Bier ,
Thank you for the message. This is what I need.
In our case we have Machine Certifcate Authentication AND Username/Password for user (I think I have to use a sequence for that purpose)
If you have 2 different AD domains that run TEAP, can you specify 2 different Cert_Profiles so that it can speed up searches in directories?
Something like:
If Network Access-EAPAuthentication EQUALS TEAP AND DomainA then SEQUENCE_A
If Network Access-EAPAuthentication EQUALS TEAP AND DomainB then SEQUENCE_B
I am not sure the Domain can be a condition at that moment of authentication
Thanks
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-29-2021 03:08 AM
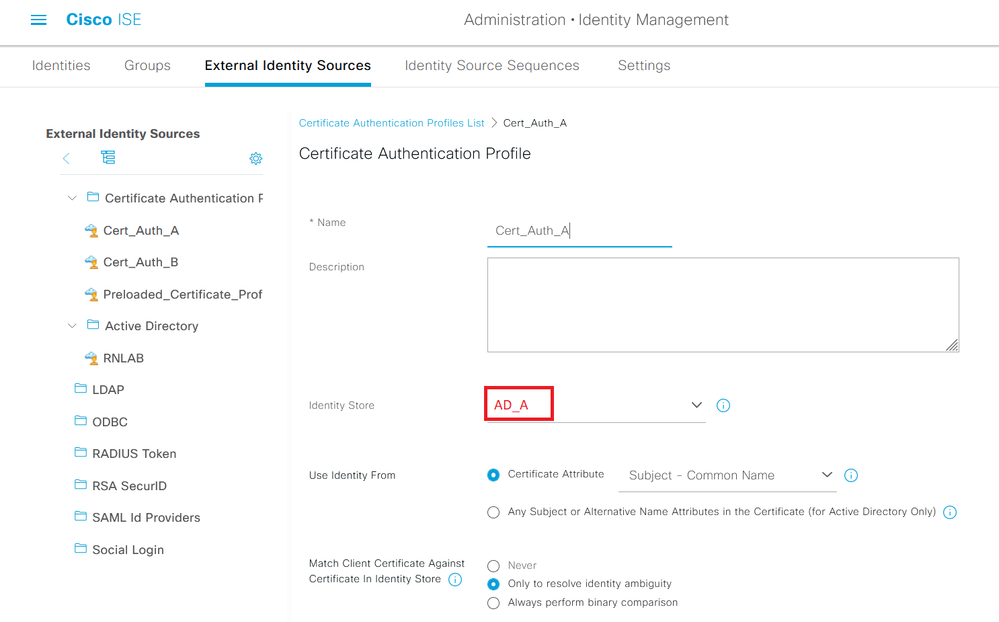
Hello @REJR77
You could put the AD domain into the Certificate Authentication Profile as shown below. Would that work for you?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-29-2021 04:22 AM
Hi @Arne Bier
I've made these 2 rules.
The first one, should match User Authentication sent with MSCHAPv2 in the TEAP Tunnel
The second one, should match the machine certificate sent in EAP-TLS on the TEAP Tunnel
I hope when adding another domain I will be able to duplicate these rules, and therefore asking only the corresponding Active Directory server. (From what I've seen, the order seems to be important (User then Machine)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-08-2021 06:21 PM
@REJR77 - how did your changes go? Did your config work?
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide