- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: Guest account expires after 2 hours and relogin
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-14-2021 07:39 AM
Hello Community! I'm trying to design a way for a Guest account with AD credentials as an employee to login and after 2 hours be purged and forced to sign back in to the captive portal. This needs to be automatic without a sponsor. I only see options for 1 day in purge settings.
Thank You,
Solved! Go to Solution.
- Labels:
-
AAA
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-14-2021 04:15 PM
The Endpoint Purge is mainly used as part of the Remember Me guest scenario. Without that configuration, a guest user would have to go through the WebAuth login every time the session timeout on the SSID was reached. I assume you want a longer session ID and Remember Me for your true Guest logins, so you could try the following for your Employee logins.
- Create a new Endpoint ID Group to separate the Employee endpoints from the Guest ones (e.g. Employee_Guest_2hours)
- Create a new Guest Type (e.g. Employee_2hours) that uses the new EIG for device registration
- Update your Guest Portal to use that Guest Type for the 'Employees using this portal as guests inherit login options from' setting
- Create a new AuthZ Profile (e.g. AuthZ-Wireless-Emp-Guest) and enable the Common Task for Reauthentication with a timer of 7200 seconds to override the SSID setting.
- Create a new AuthZ Policy rule above the others that matches on the employee AD Group (e.g. Domain Users, or something more specific if needed) and applies the new AuthZ Profile.
The user experience may be a bit clunky depending on the type of endpoint they are using, so they might get kicked off the SSID or lose connectivity and have to disconnect/reconnect to the SSID to get the webauth page again. Proper employee communication/training should be employed to set the right expectations.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-14-2021 04:15 PM
The Endpoint Purge is mainly used as part of the Remember Me guest scenario. Without that configuration, a guest user would have to go through the WebAuth login every time the session timeout on the SSID was reached. I assume you want a longer session ID and Remember Me for your true Guest logins, so you could try the following for your Employee logins.
- Create a new Endpoint ID Group to separate the Employee endpoints from the Guest ones (e.g. Employee_Guest_2hours)
- Create a new Guest Type (e.g. Employee_2hours) that uses the new EIG for device registration
- Update your Guest Portal to use that Guest Type for the 'Employees using this portal as guests inherit login options from' setting
- Create a new AuthZ Profile (e.g. AuthZ-Wireless-Emp-Guest) and enable the Common Task for Reauthentication with a timer of 7200 seconds to override the SSID setting.
- Create a new AuthZ Policy rule above the others that matches on the employee AD Group (e.g. Domain Users, or something more specific if needed) and applies the new AuthZ Profile.
The user experience may be a bit clunky depending on the type of endpoint they are using, so they might get kicked off the SSID or lose connectivity and have to disconnect/reconnect to the SSID to get the webauth page again. Proper employee communication/training should be employed to set the right expectations.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-15-2021 06:35 AM
Thank You so much, we will give it a shot on a test ssid. We are using Meraki as our wireless. Would it perform the same as a WLC?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-17-2021 02:37 PM
Meraki MR platforms do support CoA. The only other setting on the wireless side is the reauthentication pushed by ISE. I would be surprised if the MR does not support that AV pair, but you would need to test it out.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-18-2021 06:38 AM
Thank You, I do see another contrition called, EndPoints·LastAUPAcceptanceHours
If I set this above the normal authz access for employees for 2 hours to redirect to the CP. It should prompt them to log in? Do you know if this will generate another successful authentication? I ask because I have a syslog sender to my palo alto to parse successful auths and match a username to ip, and that is set to purge that match after 2 hours.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-18-2021 02:53 PM
Using that condition would require the AUP page to be presented every time the user is redirected to the portal. As per the steps I shared earlier, you should be able to do what you want without the added annoyance of constantly be prompted with an AUP.
Any time there is a reauthentication, it should generate a new session.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-18-2021 03:02 PM
Thank You it works both ways. The requirement from my customer is for it to be accepted every 2 hours. As for the staff communication and training, its on them. From an Engineering standpoint, the solution is performing.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-17-2023 03:46 AM
One doubt.
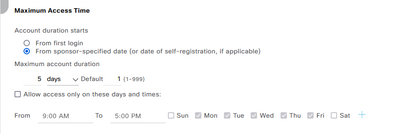
In the scenario that we have sponsor approval, after Reauthentication= 7200 expire, the user can authenticate with the current password or the sponsor should approve again??
I have a guest type with 5 days passoword valid.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide