- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: Help with TACACS in ISE 3.00
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-16-2021 12:04 PM - edited 08-16-2021 10:51 PM
Can someone help me with this query.
I have read and seen videos on the Internet about how to enable TACACS+ in ISE.
I have followed all the steps as indicated, from the licensing to creating the authentication and authorisation rules but still doesn't work.
Every time I try to login to the switch, it denies access if I use the account in AD and jumps to use the local account. The sniffer shows there is some communication between ISE and the switch up to Authentication step when it denies access and then falls back to use the local account. I do not see any activity in the TACACS live logs that could help me.
Please note that a contractor installed ISE but we didn't have the license sorted before he left, so it is now up to me to make it work. So, he enabled device admin with RADIUS.
In the attached word document I pasted some screenshots of everything I have done.
Can someone please have a look and tell me what I am missing?
I have done all the pre-checks.
ISE is listening on port 49.
I can see the TCP handshake complets OK
This is the config in the switch:
aaa group server tacacs+ ISE-TACACS
server name NWGB-H2P-ISE01
server name NWGB-H2P-ISE02
server-private 10.0.8.61 key 7 1543394F3318221571
server-private 10.0.8.62 key 7 075E130F793B10344E
ip tacacs source-interface Vlan7
!
!
aaa new-model
!
aaa authentication login VTY group ISE-TACACS local
aaa authorization network VTY group ISE-TACACS local
aaa authorization exec VTY group ISE-TACACS local
aaa session-id common
!
!
ip tacacs source-interface Vlan7
tacacs-server host 10.0.8.61
tacacs-server host 10.0.8.62
tacacs-server key 7 06573D627B7C00285C
line vty 0 4
exec-timeout 0 0
logging synchronous
login authentication VTY
transport preferred none
transport input ssh
Solved! Go to Solution.
- Labels:
-
AAA
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-16-2021 11:24 PM
Hi @a.maldonado,
I believe you are missing AD-ISE integration part (at least I don't see it in your screenshots). You need to join ISE to AD (under Administration / Identity Management / External Identity Sources / Active Directory), followed by importing your prefered AD groups, which can then later be used in the authorization policies.
All_AD_Join_Points is predefined Identity Store Sequence, which probably has no ADs inside, untill you do AD join.
BR,
Milos
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-16-2021 12:23 PM
You are missing the "aaa authorisation commands......" and "aaa accounting commands....."
Example:-
aaa authorization exec ISE-MLIST group ISE-TACACS local if-authenticated
aaa authorization commands 1 ISE-MLIST group ISE-TACACS local if-authenticated
aaa authorization commands 15 ISE-MLIST group ISE-TACACS local if-authenticated
aaa accounting exec default start-stop group ISE-TACACS
aaa accounting commands 1 default start-stop group ISE-TACACS
aaa accounting commands 15 default start-stop group ISE-TACACS
Checkout the ISE Device Administration guide, this has more information to help you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-16-2021 10:48 PM
Hi Rob,
THank you for your message, my problem is that it does not pass authentication. I pasted the commands you sent me anyway but still doesn't work.
When I try to login, the switch denies access to the user account in the AD domain and jumps straight to the local account of the switch.
I do not see any activity in the TACACS live logs that could help me. Any other idea?
End of banner message from server
Keyboard-interactive authentication prompts from server:
End of keyboard-interactive prompts from server
Access denied
Keyboard-interactive authentication prompts from server:
| Password:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-20-2021 03:04 AM
Hi Rob,
Thank you for the aaa commands you pasted for me. I finally got the switches talking to ISE via TACACS. To cut a long story short, I rebooted the ISE boxes because after trying to time sync them with the AD domain box I lost access to the rest of the switches which were still using Radius. However, the clocks were back to being out of sync (a little more than an hour) .
My question for you is. I am simualting the ISE boxes are not reacheable and therefore, I need to use the local account. It is working but after typing the admin username and hitting enter, it sends me straight to priviliedge mode. It is not asking me for a password to authenticate. Do you know why? These are the commands currently in the switch.
I appreciate your help!
aaa new-model
aaa group server tacacs+ ISE-TACACS
aaa authentication login VTY group ISE-TACACS local
aaa authentication login CON none
aaa authentication enable default group ISE-TACACS enable
aaa authorization exec VTY group ISE-TACACS local
aaa authorization exec ISE-MLIST group ISE-TACACS local if-authenticated
aaa authorization commands 1 ISE-MLIST group ISE-TACACS local if-authenticated
aaa authorization commands 15 ISE-MLIST group ISE-TACACS local if-authenticated
aaa authorization network VTY group ISE-TACACS local
aaa accounting exec default start-stop group ISE-TACACS
aaa accounting commands 1 default start-stop group ISE-TACACS
aaa accounting commands 15 default start-stop group ISE-TACACS
aaa session-id common
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-16-2021 12:48 PM
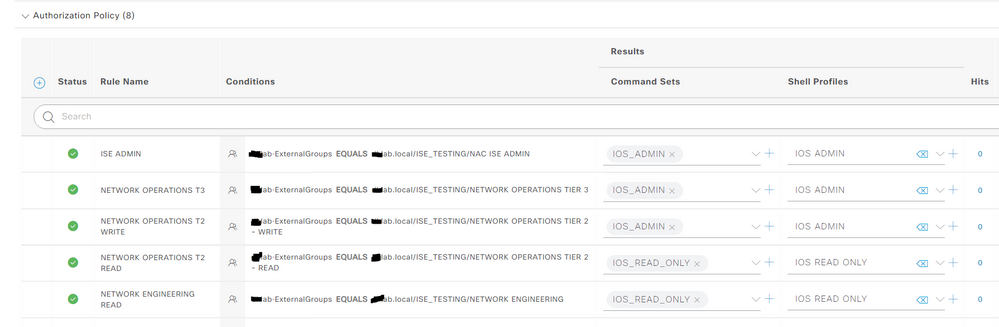
Inside ISE you're also missing solid Authorization Policies, as an example my Lab uses AD groups as shown below:
It looked like your screen shot was looking again for the Network Device again and not for a User or Group.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-16-2021 11:00 PM
Hi Mitch,
As stated above, my problem is that I do not even pass the authentication state. However, you gave me an idea and started messing around with the authentication rules, which now look like the attachment.
I did change the condition in the authorization rule to point to the AD group that will have full access to the IOS. However, none of this made any difference.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-16-2021 11:24 PM
Hi @a.maldonado,
I believe you are missing AD-ISE integration part (at least I don't see it in your screenshots). You need to join ISE to AD (under Administration / Identity Management / External Identity Sources / Active Directory), followed by importing your prefered AD groups, which can then later be used in the authorization policies.
All_AD_Join_Points is predefined Identity Store Sequence, which probably has no ADs inside, untill you do AD join.
BR,
Milos
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-18-2021 12:03 AM
Hi Milos,
Thank you for your comments.
I checked where you said and yes! there is an entry for the AD. Please see attachment. Please note that I removed the domain name from all screenshots but they are there.
I changed the authentication to usee that entry but still does not work. The switch returns the denied after trying to use the username that should work.
By the way, the contractor left our switches workinmgn with Radius which get our credentials from AD and so I know this is the username that should be working.
Any other ideas?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-18-2021 12:40 AM
Hi @a.maldonado,
Yes, your AD-ISE integration part looks fine.
Please run TACACS+ Live logs (as @hslai advised) or report, and get into detailed report and share that info. Based on detailed report, hopefully, we should be able to see at which point is failing.
BR,
Milos
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-18-2021 05:18 AM
I do not get anything in the TACACs live logs section, it is as if it never makes it to ISE but in wireshark I can see some packet excahnge.
Anyway, why should I be using the AD section to integrate the ISE with AD. Why not the LDAP section? that's what I have seen in most documentation. I just assume I could use AD because tha is what is was there.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-18-2021 06:22 AM
You would use AD section because ISE is capable of talking native language with AD. LDAP is also ok and you can make it working, but AD comes with more features and is more flexible. One of the things crosses my mind is usage of Global Catalog in AD, where you don't need to specify any specific AD server, you just use domain name, and AD would know how to talk to relevant servers. Another one is usage of Sites and Services, where you'll always communicate with 'closest' DC (depending on how your AD admin configured it), meaning that ISE in one datacenter can talk to closes one, while another in possibly different region would talk to different one. With LDAP you don't have such option.
Another thing that I noticed - what is the content of your condition in policy set, called 'Full device access'? I can't see it from the attached screenshots? Could you please try to go to deafult policy set and to configure default rule with permit statement? This way you can test it for sure if your TACACS+ is working properly, and then you are probably failing on some conditions.
In case your TACACS is licensed and enabled properly, you must always see some live logs and/or reports. They would state that authentication failed, but they must be there. I personally never seen working TACACS deployment in which there are no logs at all, which could be an indication that your service is not running properly.
BR,
Milos
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-20-2021 03:21 AM
Hi Milos,
Thank you very much for your assistance.
You were right, the problem must have been in the Authentication section of the Policy Set. I changed it to use the AD_server but still didn't work.
I then read that the time should be synced with the AD domain and tried to sync them but when I did that I lost access to the rest of the switches that were already using Radius for Device Admin. I had to reboot both ISE boxes and when they came back up the clocks were again out of sync with the AD domain but TACACs started working on the Test switch and could see activity in the TACACS live logs section. The otehr switches previously using Radisu were also reachable still using Radius.
Now, I am simulating the ISE being unreachable and using the local account to log in. The problem I have now is that after typing the admin username, it goes stright to privildege mode. It does not ask for password. Ideally, I would like it to prompt for a password. Do you know what I am missing from the configuration below?
Thank you again for your help.
aaa new-model
aaa group server tacacs+ ISE-TACACS
aaa authentication login VTY group ISE-TACACS local
aaa authentication login CON none
aaa authentication enable default group ISE-TACACS enable
aaa authorization exec VTY group ISE-TACACS local
aaa authorization exec ISE-MLIST group ISE-TACACS local if-authenticated
aaa authorization commands 1 ISE-MLIST group ISE-TACACS local if-authenticated
aaa authorization commands 15 ISE-MLIST group ISE-TACACS local if-authenticated
aaa authorization network VTY group ISE-TACACS local
aaa accounting exec default start-stop group ISE-TACACS
aaa accounting commands 1 default start-stop group ISE-TACACS
aaa accounting commands 15 default start-stop group ISE-TACACS
aaa session-id common
line vty 0 4
exec-timeout 0 0
authorization exec VTY
logging synchronous
login authentication VTY
transport preferred none
transport input ssh
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-20-2021 03:43 AM
Hi @a.maldonado,
I'm glad to hear that you managed to resolve this.
I don't see your configuration of the local user, but I'm assuming it contains 'privilege 15' along with username and password. Given that you are using AAA list called VTY under vty lines for exec authorization (command 'authorization exec VTY'), and on your list (command 'aaa authorization exec VTY group ISE-TACACS local'), you are asking AAA server for authorization firstly, and, if unavaliable like in your test, it falls back to local DB. This is an expected behavior.
If you want to be prompted for enable password you need to remove it from vty config. I would also advise to enable exec-timeout, for at least 30 mins (in order not to end up with no available vty lines at some point):
line vty 0 4
exec-timeout 30
no authorization exec VTY
Please note that this change will also prompt for enable password even if you are using TACACS+.
BR
Milos
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-20-2021 10:36 AM
Thank you Milos and to everyone who responded. You gave me some ideas.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-17-2021 10:48 PM
Please check ISE TACACS+ Live logs and run the detail reports.
As you already took some packet captures, K40341514: How to decrypt the encrypted portion of TACACS+ traffic (AskF5) to examine the T+ exchanges.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide