- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Sounds like you are going
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
How to add attribute to ISE 1.2
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-14-2015 10:07 PM - edited 03-10-2019 10:38 PM
The authentication details page shows under "Other Attributes" an attribute called SelectedAuthenticationIdentityStores
Is there a way I can create rules based on this attribute? I can't find it anywhere in the policy conditions options.
Thanks in advance!
- Labels:
-
AAA
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-15-2015 04:04 AM
this is where you select identity store
If you are looking to use identity store or group for authorization you can user following
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-15-2015 09:58 AM
I need to create an authorization condition that includes an external identity source. That does not appear to be an option so I want to add the SelectedAuthenticationIdentityStores attribute so I can create authorization conditions based on which identity store is used.
This would be very simple if ISE would let you choose an external identity source in your second screenshot, but unfortunately it only allows you to select internal identity groups.
Unless I'm missing something? Thank you for the help.
EDIT:
I actually need to create a authorization policy based on the "Identity Store" attribute, see picture. Is there a way to add this to the dictionary?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-16-2015 05:21 AM
You can do this.
First, you need to create the Authorization profiles to allow the permissions you want in your Authorization Policies.
Go to Policy > Policy Elements > Results, then from the Left Menu, choose Authorization > Authorization Profiles. Click the +Add button and create your profile. Choose the VLAN, dACL and any other attributes you want for this specific group and click Submit at the bottom of the page.
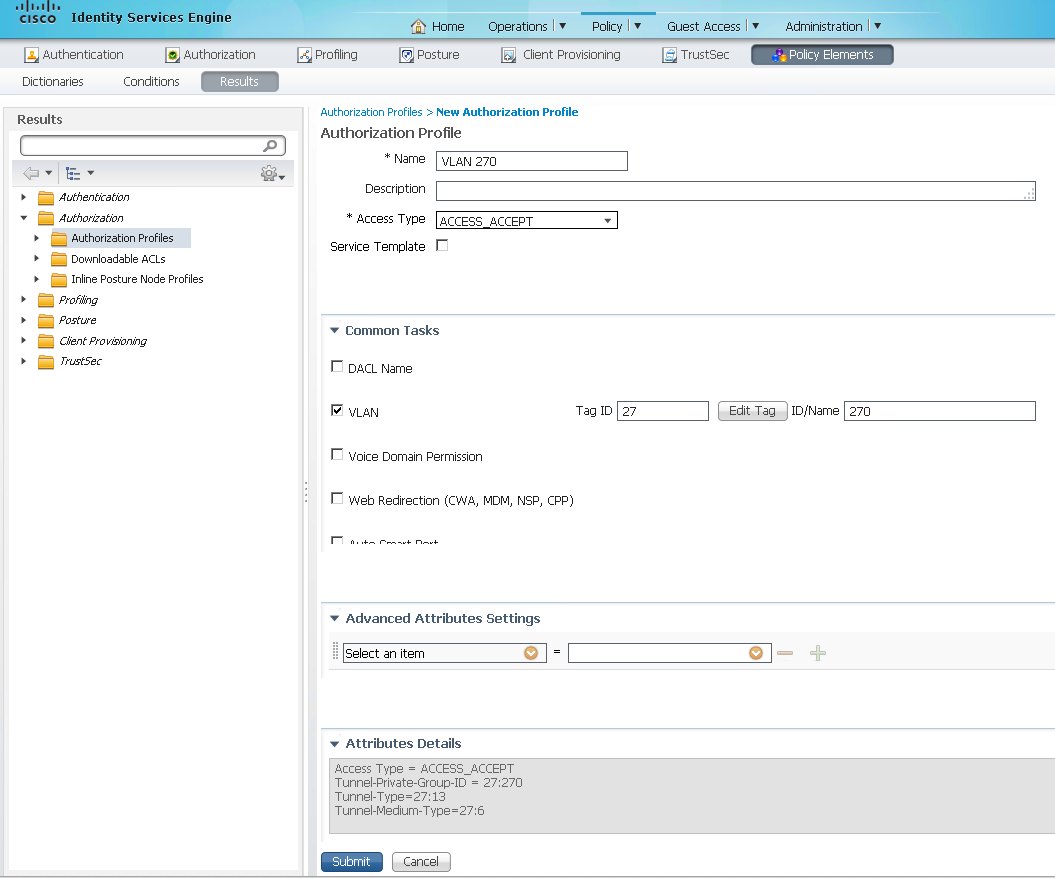
Then you can build your Authorization Policy. From the screenshots above it looks like you know how to get there (Policy > Authorization). Insert a new rule and Create New Condition.
In the Select Attribute dropbox, select your Identity Store
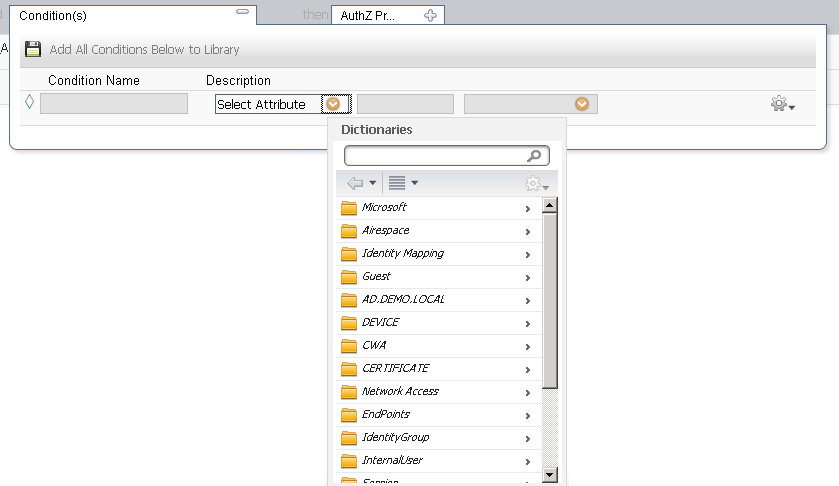
Then Choose ExternalGroups
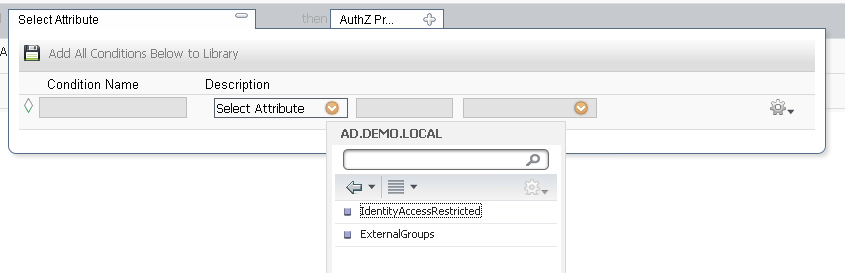
Finally, choose your group in the third dropbox. The middle defaults to Equals, but you can change it if you need to.
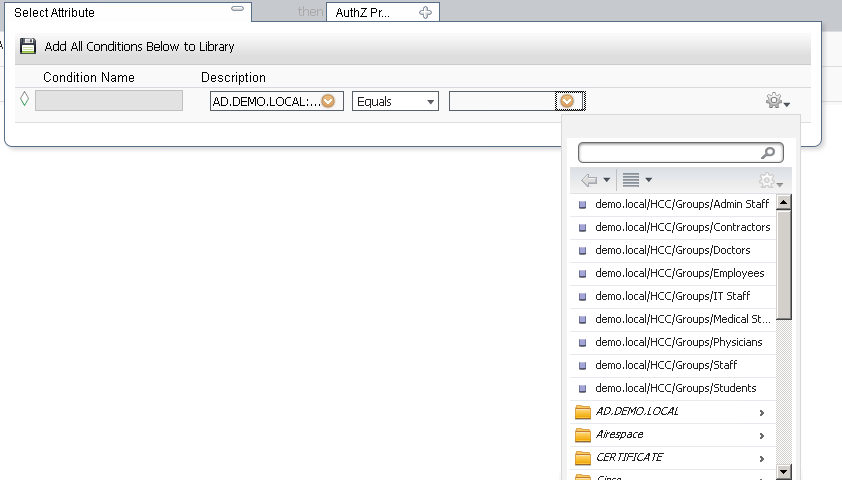
Then, in the Permissions field, choose Standard Authorization Profile

Choose the Authorization Profile you created for this specific group

Click Done and then Save

Your new rule is in place.
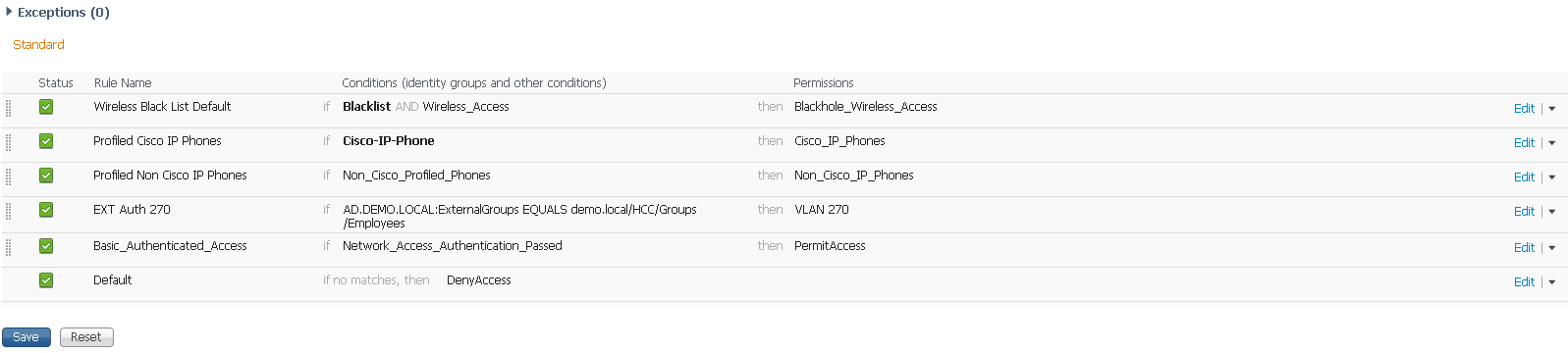
The Identity Source that you select in this process becomes the Identity Store from which you authenticate.
Please Rate Helpful posts and mark this question as answered if, in fact, this does answer your question. Otherwise, feel free to post follow-up questions.
Charles Moreton
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-20-2015 03:37 PM
Thank you for the response.
In my case I am dealing with two external identity sources (AD and RSA SecurID) to which some users can authenticate to both. I need to force certain AD groups to authenticate ONLY to the RSA SecurID identity source and disallow access via their AD credentials.
Your response and screenshots are what we already do for access based on AD groups.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-22-2015 05:04 PM
Sounds like you are going about this the wrong way, creating an authorization rule with some identitystore condtions, won't make the user authenticate to that store, it will only be used to lookup the user, for group matching, but for that to happen, they already have to be authenticated. Maybe you could explain what it is exactly your scenario is ?
- are those radius requests it coming from the same radius client ?
- what is it used for ?
- How does the user select to use rsa and not ad, or vice-versa ?
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide