- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: How to make redirection work for HP5130 switch
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-04-2018 12:08 AM
Hi Experts,
We are deploying ISE for our wired environment and we have a site that majorly has a mix of HP switches (Aruba and H3C).
The configuration and testing of the Aruba switches was seamless, now we are stuck with HP5130 switch, the redirection is not working.
What I see is when I use the attribute HPE-Captive-Portal-URL, I see that ISE pushes the URL, but the user is not able to open the page, he just get a blank page on the browser.
While looking for reference documents, I came across a document that talked about adding these two H3C specific attributes to NAD, attributes #210, H3C-AVPair and attribute #250, H3C-Web-URL.
If I use any of these attributes, attributes #210, H3C-AVPair and attribute #250, H3C-Web-URL, there is no redirection URL being sent by ISE in it.
As, you can see in the attached screenshots.
Has anyone successfully configured redirection on HP5130 switches?
Any pointers much appreciated.
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-25-2018 06:39 AM
See Hosuk's comment at your other discussion AnyConnect blank page when clicking dow...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-04-2018 05:26 AM
Hi Dinesh,
please refer the NAD profile here - https://communities.cisco.com/docs/DOC-70347
Also please refer the discussion - https://community.cisco.com/t5/identity-services-engine-ise/h3c-s5130-integration-with-ise-2-3/td-p/3600494
Meanwhile , Can you send me screenshot of default acl and dACL from ISE ?
you can send me the acl snapshot from the NAD port as well.
Thanks,
Nidhi
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-04-2018 06:05 AM
Hi Nidhi,
As off now we are not pushing any dACL to the endpoints, here is the ACL that I have configured on the switch for redirection;
[NAC-5130-2]display acl 3003
Advanced IPv4 ACL 3003, 29 rules,
ACL's step is 5, start ID is 0
rule 0 permit ip destination <ISE Server> 0
rule 5 permit udp destination-port eq dns
rule 10 permit udp source-port eq bootpc destination-port eq bootps
rule 15 permit udp source-port eq bootps destination-port eq bootpc
rule 20 permit tcp destination-port eq 2967
rule 25 permit tcp source-port eq 2967
rule 30 permit tcp destination-port eq 7070
rule 35 permit tcp source-port eq 7070
rule 40 permit ip destination <AV Server> 0
rule 45 permit tcp destination <AV Server> 0 destination-port eq 443
rule 50 permit tcp destination <AV Server> 0 destination-port eq www
rule 55 permit tcp destination <AV Server> 0 destination-port eq 443
rule 60 permit tcp destination <AV Server> 0 destination-port eq www
rule 65 permit tcp destination <AV Server> destination-port eq 443
rule 70 permit tcp destination <AV Server> destination-port eq www
rule 75 permit tcp destination <SCCM Server> 0 destination-port eq 443
rule 80 permit tcp destination <SCCM Server> 0 destination-port eq www
rule 85 permit tcp destination <SCCM Server> 0 destination-port eq 443
rule 90 permit tcp destination <SCCM Server> 0 destination-port eq www
rule 95 permit tcp destination <SCCM Server> 0 destination-port eq 443
rule 100 permit tcp destination <SCCM Server> 0 destination-port eq www
rule 105 permit tcp destination <SCCM Server> 0 destination-port eq 443
rule 110 permit tcp destination <SCCM Server> 0 destination-port eq www
rule 115 permit tcp destination <SCCM Server> 0 destination-port eq 443
rule 120 permit tcp destination <SCCM Server> 0 destination-port eq www
rule 125 permit tcp destination <SCCM Server> 0 destination-port eq 443
rule 130 permit tcp destination <SCCM Server> 0 destination-port eq www
rule 135 deny tcp destination-port eq www
rule 140 deny tcp destination-port eq 443
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-08-2018 03:36 AM
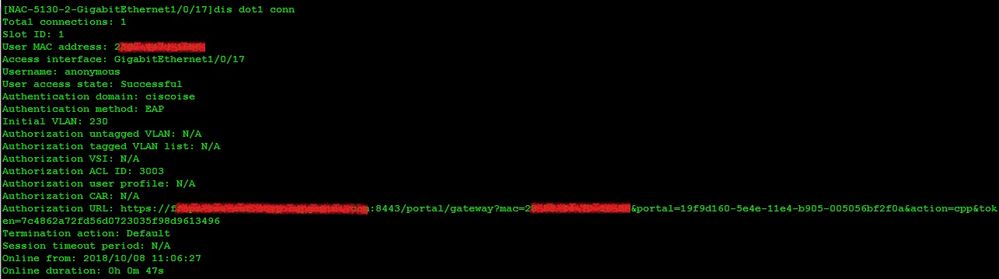
I had to edit the attribute H3C-Web-URL (removed allow tagging). After this change was able see the redirection URL being pushed just fine, as you can see below:
Now, even still if the user opens a browser and types any web-site, the user is still not getting redirected to the above URL on the switch?
Any insights if I am missing out any configuration on the switch?
I am using this little ACL to test out the above use case:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-24-2018 01:20 AM
Was able to get the redirection working using HP switch, it was finally the issue with the ACL that we were using.
The ACL had to be tweaked to specifically allow ports 443 and 80 towards and resolved issue.
Here is the ACL that I used for this purpose:
rule 0 permit tcp destination <ISE Server> 0 destination-port eq 443
rule 5 permit tcp destination <ISE Server> 0 destination-port eq www
rule 10 permit udp destination-port eq dns
rule 15 permit udp destination-port eq bootps
Now there is another issue that I am facing, when the user clicks on the download agent link, he directed towards a blank page and no download happens.
More details here
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-24-2018 02:33 AM
Hi Dinesh,
Make sure you have the Posture type set to 'Temporal agent' under Posture Policy.
Check this guide here - https://www.cisco.com/c/en/us/td/docs/security/ise/2-4/admin_guide/b_ise_admin_guide_24/b_ise_admin_guide_24_new_chapter_010111.html#Posture_Types
Thanks,
Nidhi
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-24-2018 05:14 AM
As per the requirement here with client they are not going for a temporal agent for this, since these are going to be corporate machine users.
So, need to make sure that AnyConnect agent is downloaded and posture checks are run
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-25-2018 06:39 AM
See Hosuk's comment at your other discussion AnyConnect blank page when clicking dow...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-26-2018 03:24 AM
Yes, need open up a TAC case for this one.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide