- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: Integrating ISE with Azure Intune as MDM
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-05-2021 05:57 AM - edited 10-05-2021 05:59 AM
Hello,
I'm trying to use Computer authentication with Azure AD.
As Azure AD only works with SAML, and ROPC only allows EAP-TTLS ie user authentication , I'm looking into Intune as a MDM server.
I've followed all the procedure here :
The certificates are trusted both sides, but when I test the connection I get the following error :
Connection to server failed with:
Unrecognized field "requestId" (Class com.cisco.cpm.mdm.auto.discovery.MdmAzureDirectoryServiceErrorOdata), not marked as ignorable at [Source: java.io.StringReader@20d9ea84; line: 1, column: 152] (through reference chain: com.cisco.cpm.mdm.auto.discovery.MdmAzureDirectoryServiceErrorResponse["odata.error"]->com.cisco.cpm.mdm.auto.discovery.MdmAzureDirectoryServiceErrorOdata["requestId"])
Please try with different settings.
Packet capture shows one connection to the token URL, so I guess the token retrieval is ok, then another connection to the discovery URL https://graph.windows.net/<Tenant ID>.
We are running version 3.0 Patch 4.
Does anyone knows how to resolve this ?
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-11-2021 02:15 AM
Hello All,
I made it up last week with the help of Cisco TAC, so I confirm I'm now able to reach Intune as external MDM server with ISE 3.0.
We indeed added extra permissions on Intune's side. Cisco tech confirmed the pemissions are intended to be deprecated by Intune, but they don't have anything to replace it, and the deprecation is not effective currently. So we have no choice but to use these deprecated permission.
=> "Azure Active Directory Graph"
==> Delegated : Directory- Read ALL
==> Delegated : User - Read ALL
==> Application : read All
We did also ensure the public CAs in the Trusted store have the "Trust Cisco Services" checked. It concerns for example :
- Baltimore CA
- DigiCert SHA2
- DigiCert Global Root CA
- DigiCert Global Root G2
- Microsoft Azure TLS Issuing CA 01
- Microsoft Azure TLS Issuing CA 02
-... and more
Also, these changes in Intune took a couple of minutes to be effective.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-05-2021 04:34 PM
I've also just run into this issue today with ISE 3.1 <no patch>. Will advise if I make any progress...
My error for ref:
Connection to server failed with:
Unrecognized field "requestId" (Class com.cisco.cpm.mdm.auto.discovery.MdmAzureDirectoryServiceErrorOdata), not marked as ignorable at [Source: java.io.StringReader@21e0ae84; line: 1, column: 152] (through reference chain: com.cisco.cpm.mdm.auto.discovery.MdmAzureDirectoryServiceErrorResponse["odata.error"]-
>com.cisco.cpm.mdm.auto.discovery.MdmAzureDirectoryServiceErrorOdata["requestId"])
Please try with different settings.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-05-2021 06:20 PM
The Cisco documentation (link from OP) indicates a different Auto Discovery URL than my Azure tenancy...
Azure: 'Azure AD > ISE_Intune > Overview > Endpoints' = https://graph.microsoft.com
From Cisco Doco: “https://graph.windows.net/<Directory (tenant) ID>”
When I update to 'graph.microsoft.com/<tenant_id>', it still fails, but gives a different error:
Unrecognized field "error" (Class com.cisco.cpm.mdm.auto.discovery.MdmAzureDirectoryServiceErrorResponse), not marked as ignorable at [Source: java.io.StringReader@820198b; line: 1, column: 11] (through reference chain: com.cisco.cpm.mdm.auto.discovery.MdmAzureDirectoryServiceErrorResponse["error"])
I also find I cant add permissions for 'Azure Active Directory Graph' as it has been deprecated. (My Azure instance is a brand new lab env, though Cisco Docs still indicate this is needed...)
Have deleted the Azure App, and re-added - still no luck...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-05-2021 10:53 PM
I got my integration working. I had to use the Auto Discovery URL from the Cisco guide, NOT the one from the Azure portal Endpoints page. I used: “https://graph.windows.net/<Directory (tenant) ID>”, which is the same as you have....
I think my main issue was that I hadn't enabled ISE ERS; so try doing that 'Administration > System > Settings > API Settings'. I initially enabled both ERS and OpenAPI; I'm not certain which is required, but think probably ERS.
I had also found a way to add the Permissions for the deprecated 'Azure Active Directory Graph' API; I had to do this by manually updating the Manifest - you can't do it in GUI any more. Not sure if this is actually required, however if you want/need to try it, add the following in the "requiredResourceAccess" section near the end.
Hope that helps you with your issue...
Tim
{
"resourceAppId": "00000002-0000-0000-c000-000000000000",
"resourceAccess": [
{
"id": "c582532d-9d9e-43bd-a97c-2667a28ce295",
"type": "Scope"
},
{
"id": "5778995a-e1bf-45b8-affa-663a9f3f4d04",
"type": "Scope"
},
{
"id": "5778995a-e1bf-45b8-affa-663a9f3f4d04",
"type": "Role"
}
]
},
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-11-2021 01:17 AM
Hello @Tim Fairclough
I've checked that ESR API is enabled, and I've added the deprecated privileges in the manifest.xml.
Without success...
I've even tried to use the token issuing URL v1 instead of v2 but I've still have the error : Unrecognized field "requestId".
I'll open a case to require asssistance on this feature, I'll let you know if we found something.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-11-2021 06:28 PM - edited 10-11-2021 08:40 PM
Good luck with TAC, I'm sure they'll get you past this hurdle.
Now that my Intune integration is working, will summarise my findings for you as I expect we have similar goals / hopes, and this might save you some time...
I have Intune deploying SCEP User and Computer certs to my test device, as well as an EAP-TLS WiFi profile. While I can write policy in ISE to authorise the EAP-TLS machine auth, I haven't found a way to actually authorise the machine account against AAD. I have Authz rule checking MDM:DeviceRegisterStatus and MDM:DeviceComplianceStatus working, but if I disable the 'device' in AAD>Devices, it can still connect - I expected this would also disable the device in Intune, but it doesn't seem to...
Additionally, it isn't possible to do EAP-TLS User authz against Azure natively either; so no way to check if the account is still active or what group memberships it has (though you could put some of this info into a Cert SAN field).
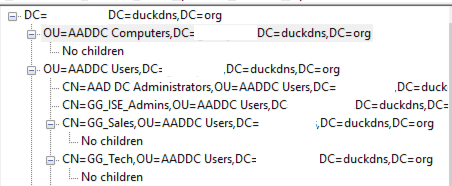
I installed Azure AD Directory Services in my tenancy, and have configured an LDAPS connection in ISE. I can now use that to authorise EAP-TLS User auth's, but do not see any LDAP groups that contain my AAD joined computer. I had setup my AADDS 'Forest Type' as 'User' rather than 'Resource'; so perhaps things might have been different if I had selected Resource Forest... Note, I COULD see
At this point, my 'AAD Computer' authz policy will need to rely on devices actually being deleted from AAD and Intune, rather than simply disabling the 'AAD Device' as I have tried.
Using PDP.Exe, I cant see my AzureAD Joined computer...:
Please post if you manage to get Computer Authentication working against AAD / AADDS, or some other 'cloud native' way!
Tim
Create AADDS instance:
https://docs.microsoft.com/en-us/azure/active-directory-domain-services/tutorial-create-instance
Enable LDAPS in AADDS:
https://docs.microsoft.com/en-us/azure/active-directory-domain-services/tutorial-configure-ldaps
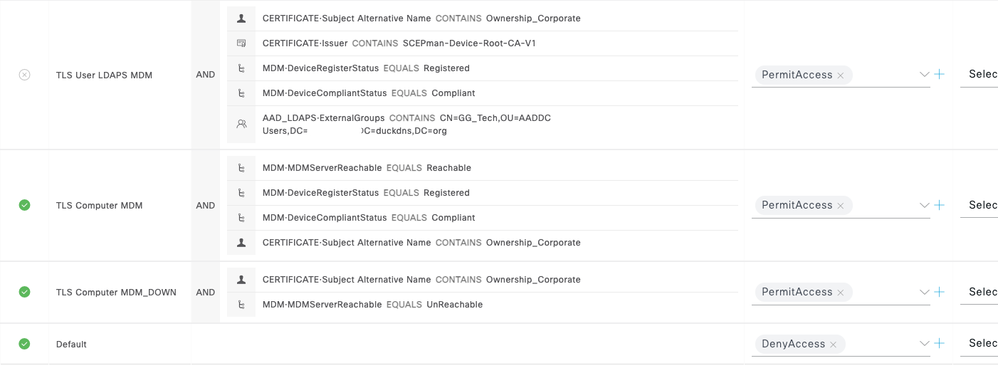
AuthZ policy:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-11-2021 12:53 AM
Hi Marie,
This is likely a Azure permissions issue.
I guess you should check out Cisco bug ID CSCvz85536 which describes how these Azure Active Directory Graph permissions can be set despite the fact that they are greyed out by default and will become deprecated in june 2022.
I don't know about any initiatives by Cisco to properly fix this issue, instead of continuing to leverage soon-deprecated/legacy Azure permissions. Can't find anything in Cisco documentation or online.
Any Cisco employees in the community have any thoughts on this issue or bug ID (CSCvz85536)?
Thanks!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-11-2021 02:15 AM
Hello All,
I made it up last week with the help of Cisco TAC, so I confirm I'm now able to reach Intune as external MDM server with ISE 3.0.
We indeed added extra permissions on Intune's side. Cisco tech confirmed the pemissions are intended to be deprecated by Intune, but they don't have anything to replace it, and the deprecation is not effective currently. So we have no choice but to use these deprecated permission.
=> "Azure Active Directory Graph"
==> Delegated : Directory- Read ALL
==> Delegated : User - Read ALL
==> Application : read All
We did also ensure the public CAs in the Trusted store have the "Trust Cisco Services" checked. It concerns for example :
- Baltimore CA
- DigiCert SHA2
- DigiCert Global Root CA
- DigiCert Global Root G2
- Microsoft Azure TLS Issuing CA 01
- Microsoft Azure TLS Issuing CA 02
-... and more
Also, these changes in Intune took a couple of minutes to be effective.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-06-2022 06:41 AM
Hi, is there any new update from Cisco? Or should we still keeping using old Azure Active Directory Graph permissions? Thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-06-2022 04:26 PM
The requirements and permissions required for integrating ISE with Intune MDM via the Microsoft Graph API are documented here:
Note that you will need ISE version 3.1+ to leverage the MDM APIv3 and GUID based lookups against Intune.
You may also want to be aware of this Field Notice related to MS deprecating the API that supports MAC Address lookups for MDM compliance.
https://www.cisco.com/c/en/us/support/docs/field-notices/724/fn72427.html
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-07-2022 07:13 AM
Thank you for your reply, so we are still forced to use Azure Active Directory Graph which is going to be deprecated by Microsoft on 31st of March 2023.
Does Cisco have any plan what to do after Azure Active Directory Graph will be no more available ?
"Update 7/29/2022: We have updated the retirement date of the Azure AD Graph and MSOnline PowerShell licensing assignment APIs and PowerShell cmdlets for existing tenants to March 31, 2023. APIs and Cmdlets will not work for new tenants created after November 1, 2022. Customers may notice performance delays as we approach the retirement deadline, so we recommend prioritizing migration to MS Graph following the guidance below and in Find Azure AD and MSOnline cmdlets in Microsoft Graph PowerShell | Microsoft Docs."
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-07-2022 03:11 PM
I'm not sure I understand your comment "so we are still forced to use Azure Active Directory Graph". The document I shared discusses the steps to migrate from the legacy Azure AD Graph to the newer Microsoft Graph API. With the MS Graph API, any lookups against Intune for MDM Compliance must use the GUID.
After MS retires the legacy Azure AD Graph API, Cisco ISE will have no way to do MDM Compliance lookups against Intune with any non-GUID methods (including MAC Address). This is a MS decision that Cisco has no control over.
I'm not aware of any plans to update the MDM API in older ISE versions, so Intune integration using the MS Graph API and GUID will require customers to upgrade to ISE version 3.1 or newer.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-07-2022 04:57 PM
You might also want to have a look at the ISE webinar I delivered last month for ISE Integration with Intune MDM.
I discuss some of the flows related to the Intune MDM Compliance Checks using ISE 3.1 as well as the feature enhancement in ISE 3.2 (recently released) for EAP-TLS User auth against Azure AD + Intune MDM Compliance check using the GUID.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-09-2022 02:03 AM
When integrating Intune with Cisco ISE, we used the API permission from https://community.cisco.com/t5/security-knowledge-base/how-to-integrate-cisco-ise-mdm-with-microsoft-intune/ta-p/4187375 and Auto Discovery URL: https://graph.windows.net/< Directory (tenant) ID> instead of these latest settings. Cisco ISE connects to Azure but we can't get the mobile devices to connect to the WLAN. Can changing the settings to those of https://www.cisco.com/c/en/us/td/docs/security/ise/UEM-MDM-Server-Integration/b_MDM_UEM_Servers_CiscoISE/chapter.html help?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-13-2022 01:35 AM
I will use guide https://www.cisco.com/c/en/us/td/docs/security/ise/UEM-MDM-Server-Integration/b_MDM_UEM_Servers_CiscoISE/chapter.html as a reference. In the guide it says:
"After you update Cisco ISE to one of the supported versions, in each Microsoft Intune server integration in Cisco ISE, manually update the Auto Discovery URL field (Step 32).
Replace https://graph.windows.net<Directory (tenant) ID> with https://graph.microsoft.com."
but then later on it says that we should use old connector:
"The following fields require the information from the Microsoft Intune application in the Microsoft Azure Active Directory:
In the Auto Discovery URL field, enter https://graph.windows.net/<Directory (tenant) ID>"
When use Auto Discovery URL with the old connector (https://graph.windows.net/<Directory (tenant)ID>), connection to MDM server works, but when I try to use new connector (https://graph.microsoft.com/<Directory (tenant)ID>) ; Test Connection is giving me following error:
"Connection to server failed with:
Unrecognized field "error" (Class com.cisco.cpm.mdm.auto.discovery.MdmAzureDi
rectoryServiceErrorResponse), not marked as ignorable at [Source: java.io.StringReader@714fbb3c; line: 1, column: 11] (through reference chain: com.cisco.cpm.mdm.auto.discovery.MdmAzureDi
rectoryServiceErrorResponse["error"])
Please try with different settings."
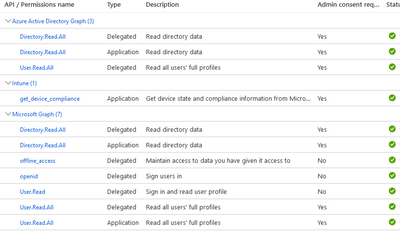
The API permissions which we are using are the same as API permissions mentioned in the guide, our API permissions:
So my statement that "we are still forced to use Azure Active Directory Graph" was basically reflecting that connection to Intune MDM doesn't work with new https://graph.microsoft.com auto discovery url.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide