- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: iPSK Manager and ISE 2.6 Problems
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-13-2020 01:00 PM - edited 02-13-2020 01:06 PM
Hello,
I've been working on setting up the iPSK Manager as described in the following link, written by @howon:
I work for a large enterprise ISP with fantastic support contracts with TAC, but TAC seems like they are unable to assist with this tool, hence why I am turning to the community forum for support. At least, the TAC engineer I received when I opened a case on iPSK issues has never heard of this tool, and they have not yet asked to look into it together.
My instance of ISE is a standalone node running 2.6.0.156 and it is NOT in production (yet). Eventually I will be migrating my older ISE to this one, but until then, I wanted to explore iPSK.
While the guide covers a few different iPSK use-cases, I have not been able to get ANY of them to work.
BYOD Self-Registration Portal
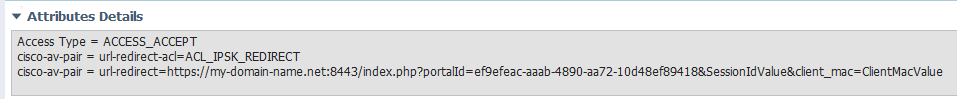
The BYOD self-registration portal is most appealing to me, so I will start here. The problem I encountered during the setup of the BYOD portal is during the ISE configurtation of the Authorization Profile. The table listed under this section specifies than an av-pair attribute is needed with a value that points to the URL of the portal, along with some other parameters, ie:
url-redirect=https://portal.authc.net:8443/index.php?portalId=b3a8fd37-eddb-4a2f-bf75-af255340c8fb&SessionIdValue&client_mac=ClientMacValue
However, when I enter the av-pair in my authorization profile following the same convention, ISE complains that it is in an invalid format and does not allow me to continue. Example:
url-redirect=https://my-domain-name.net:8443/index.php?portalId=ef9efeac-aaab-4890-aa72-10d48ef89418&SessionIdValue&client_mac=ClientMacValue
ISE complains with a message: Unable to edit Authorization Profile (iPSK) : Format for url redirect : <url> isn't valid.
Here are the Attributes Details:
(Obviously, my-domain-name is replaced with my actual domain name).
And before the suggestion arise to use the ERS API to create the authorization profile automatically, that isn't working for me either. I've enabled the ERS API, created the ers-operator and ers-admin users, and configured the iPSK Manager to use the ERS. The iPSK Manager guide does not specify the format of the ERS API URL, so I have tried the following variants, for both the ers-admin and ers-operator user accounts:
- https://<ise-url>
- https://<ise-url>:9060
- https://<ise-url>:9060/ers
With each URL, I've tried to create a new portal, view the portal, and click the "Create ISE Authoriztation Profile" button. I fill out the profile name and description, hit validate, and then click "Create Authorization Profile". The profile never gets created in ISE, hence why I tried to do it manually. I have verified that communication over port from the IPSK Manager to ISE on port 9060 works (telnet to ISE on 9060 from the iPSK manager host successfully connects).
Manual Creation via "IT Staff" portal
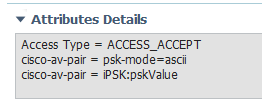
The problem I run into with this method is that the client device reports incorrect password. ISE returns AUTH_SUCCESS, but the client still cannot join. My WLC is a 8510 running 8.5.151.0. Here are the av-pairs that the authorization profile is configured to use:
I am attempting to authenticate my client using the password that the iPSK Manager automatically generated for this client when I manually added the client via the iPSK Manager portal. Here is the ISE log from the authentication attempt:

I would greatly appreciate any input or suggestions of things to try to get this working!
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-13-2020 04:23 PM
For the advanced attribute "iPSK:pskValue", "iPSK" portion is the name of ODBC identity source name that I gave in the example. If you are using different ODBC source name like "ipsk_manager" then it should read "ipsk_manager:pskValue". In fact, instead of copy and pasting the value, I suggest using the attribute navigator to select the field within the advanced attribute.
If you want to test assisted flow, you will need to use ISE 2.4 for now. As you found out, the defect also does not allow creation of proper authorization profile using the API. I've noted the shortcoming at the end of the document.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-13-2020 02:34 PM - edited 02-13-2020 02:45 PM
David, thanks for trying out the iPSK Manager. There is an open defect in regards to Authorization profile starting with ISE 2.6 where it does not allow custom redirect URL, this also affects ISE 2.7. Since you have a TAC SR open, ask the engineer to reference CSCvs46399. This defect is currently not visible to the public but TAC should be able to handle it.
As noted in the main document, iPSK Manager is provided as sample code and we do not provide any official support. It was meant for customers and partners like you where you can leverage the code to customize it to your requirement. However, I can still help you with the second problem you noted regarding the 'IT Staff' Portal. On the same detailed report, there should be a section called 'Result'. This section should include the PSK value ISE is sending back to the WLC. Can you confirm that it shows the correct PSK for corresponding client? Also, are you using FlexConnect AP or local mode AP?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-13-2020 04:06 PM
Howon, thank you for all your effort and hard work towards the project! And thank you for the bug ID. I will inform the TAC engineer I'm working with, although the TAC case was primarily created because ISE is returning "Access-Accept" but the client cannot join the network.
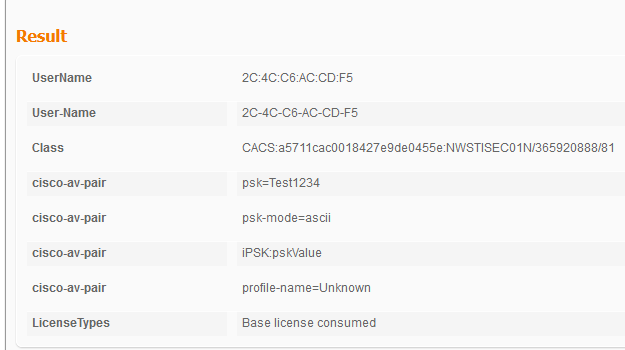
Looking in the Result section on the RADIUS log, I see the following av-pairs:
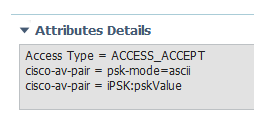
The above Result log is an attempt from the client that could not connect to the WLAN despite ISE returning access-accept. Looking at the result above, the "psk=Test1234" av-pair should not be there. The TAC engineer asked me to add that av-pair, but I've since removed it and it is not currently listed in the profile:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-13-2020 04:23 PM
For the advanced attribute "iPSK:pskValue", "iPSK" portion is the name of ODBC identity source name that I gave in the example. If you are using different ODBC source name like "ipsk_manager" then it should read "ipsk_manager:pskValue". In fact, instead of copy and pasting the value, I suggest using the attribute navigator to select the field within the advanced attribute.
If you want to test assisted flow, you will need to use ISE 2.4 for now. As you found out, the defect also does not allow creation of proper authorization profile using the API. I've noted the shortcoming at the end of the document.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-13-2020 04:55 PM
I've updated the av-pair using the attribute selector (I was using ipsk_manager as the ODBC source name). The passphrase in iPSK Manager for my client now works! Thanks a lot!
Now I can experiment with assigning different IPSK groups to different VLANs. Thank you!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-22-2020 07:37 AM
By the way, if the goal is to segment users based on iPSK values, then you don't need to assign dynamic VLANs in addition to IPSK. If using AireOS 8.8+, there is IPSK grouping feature where WLC can segment based on IPSK values. With this feature, when endpoints share same IPSK, they can form a private network and communicate among themselves while endpoints with different IPSK cannot. With this you don't have to burdened with design requirement that comes with additional VLANs. See following section on how to configure the feature:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-22-2020 12:12 PM
Thank you for the info, howon - that is exactly the goal. Unfortunately, we're using 8510s right now so we're limited to 8.5. We will likely be getting the newer 9k WLCs sometime this year, though, so I will keep this in mind! Until then, I'll have to rely on policy mapping within ISE.
I'm planning to dive deeper into iPSK using the new iPSK Manager tool this coming week. I informed my TAC engineer about the bug ID you had previously shared, and they said they can make the bug public so I can sign up for alerts regarding it. Would you happen to know if a fix for the bug is in the works for ISE 2.6? Or, do you think it's a long term/low priority issue and I would be better off setting up ISE 2.4 instead of waiting?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-25-2020 02:23 PM
Yes, we are looking to fix it on the 2.6 but no ETA.
By the way, 9800 version 17.1 was released earlier this week and it supports IPSK p2p blocking.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-28-2020 02:14 PM
On another note, I deployed ISE 2.4 so I could experiment with the captive portal URL in the authorization policy. When I try to create the authorization profile through the iPSK Manager, the iPSK Manager becomes unresponsive after clicking "Create Authorization Profile". I can't even get to the tool if I refresh the page or try to access the the page in a new tab. I have to use a different browser (aka, a completely new session?) to get back into the iPSK Manager tool.
Also, can you clarify how the captive portal works? I don't quite understand and since I haven't been able to get it working by following the guide, I don't have any experience using it. My confusion is: If a client needs to enter a PSK to connect to the wireless network in the first place, how are they supposed to get to the captive portal?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-02-2020 09:32 AM
I suggest manually creating the authorization profile for the captive portal instead of using API as it has more dependency. It is fairly easy to create even done manually.
Also, I suggest going through the assisted onboarding section of the document:
Above link has a ladder diagram and also a video of end user experience. The video example I am showing is using single-SSID where you connect with default PSK and get individual PSK after the flow. You can also use two SSID where you initially connect to open SSID and then move to PSK SSID after individual PSK has been assigned.
If you still have issues, you can reach out to me at howon@cisco.com and we can walk through the setup.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-06-2020 02:03 PM
Thanks Howon. I was out of the office for most of this week. I will continue looking at iPSK next week and reach out to you if I continue to have problems. Thank you for offering your assistance!
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide