- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: ISE 2.3 - AP Profiling issue
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
ISE 2.3 - AP Profiling issue
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-22-2017 01:42 AM - edited 02-21-2020 10:39 AM
Dear,
I am having a POC with Cisco ISE 2.3 and i have some issue with AP Profiling, it's always falling the CWA policy.
This is my policy about AP.
I have created a Logical policy - AP-GROUP, then i pointed it out in the condition with full access as result.
The result is always pointing to the CWA with the Endpoin Porife as "Cisco-Device" and after few seconds, mab will fail and will never reauthenticate again.
P.S.: I have done similar configuration with IP Phone with just pointing it to the logical profile of Phone and it works perfectly.
Any Suggestion please....
Thanks,
- Labels:
-
Other NAC
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-23-2017 12:54 PM
If ISE can only identify your access points as a "Cisco-device" this normally means ISE i basing its profiling "decision" on OUI only, or the default profling policies isn't sufficient enough. As I don't know which methods you are using when profiling devices (nmap, dhcp, device sensor .....) this will be hard to tell.
Assuming the issue is caused by lack of profiling information (only OUI) my suggestion would be either to enable device sensor (https://www.cisco.com/c/en/us/support/docs/security/identity-services-engine/200292-Configure-Device-Sensor-for-ISE-Profilin.html) or profile devices based on dhcp discover/requests as well (one of two ways to do this is to add ISE as a IP helper)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-24-2017 07:04 AM
I had the same issue once on ISE 2.0
Try first to enable device-sensor using cdp, lldp and dhcp probes if possible. This should increase the amont of information collected from the endpoint.
Then make sure that based on your profiling rules are acccurate enough to match the corresponding profile (See Policy - Profile - AP XXX)
B/R
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-26-2017 12:45 AM
Hi, Thank you folks,
I have enabled mostly the required probes, and even added the device sensor command in the switch, but i am still getting the same result.
I have attached some of the screenshot to understand the situation.
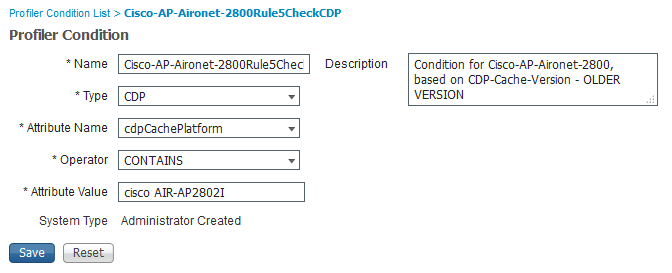
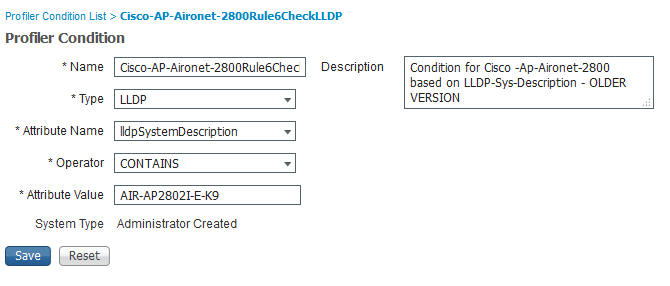
Kindly if anyone can suggest the profiling condition, i would appreciate it. I have even attached the profile condition for Access Point
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-26-2017 01:33 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-26-2017 01:33 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-26-2017 02:57 AM
Hi
please Attach screenshots from the endpoint DETAILS (context visibility >> endpoints then hit the Mac address of the APs’ Mac address). From that view you will be able to see everything ISE knows about or have letande about the endpoint. That’s the data you need to compare to the profiling policy in order to troubleshoot why there’s no 2700-AP policy match
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-26-2017 04:31 AM
Thansk man, appreciate your response...
As requested, kindly find attached complete screen shots from context visibility tab...
Please let me know if you found something new...
Regards,
Manny
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-27-2017 01:45 PM
Also remember, when a client hit a authZ rule which results in a redirect, ISE won't issue a CoA. This will prevent the AP from being authorized correctly even when the AP has been profiled properly. However, once you restart the AP and it has been profiled properly this shouldn't be an issue as it will hit the correct authZ rule straight away.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-26-2017 01:57 AM
If it's fine, can you share with the related screen shots of your profiling condition related to Access-Point and AP model 2700, I just to compare my configuration, maybe i missed something.
Appreciate your concern!
Thanks,
Manny
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-26-2017 11:04 PM
Hi,
Try to add this in you switch config :
device-sensor filter-list lldp list TLV-LLDP
tlv name system-name
tlv name system-description
!
device-sensor filter-list cdp list TLV-CDP
tlv name device-name
tlv name address-type
tlv name capabilities-type
tlv name platform-type
!
device-sensor filter-list dhcp list TLV-DHCP
option name host-name
option name requested-address
option name parameter-request-list
option name class-identifier
option name client-identifier
device-sensor filter-spec dhcp include list TLV-DHCP
device-sensor filter-spec lldp include list TLV-LLDP
device-sensor filter-spec cdp include list TLV-CDP
device-sensor accounting
device-sensor notify all-changes
Now take a look at all the attributes gathered by the device sensor and make rules accurate enough to profile your APs correctly. For instance this is what I had to add to the standard ruleset :
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide