- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: ISE 2.4 Command set not working
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-15-2019 05:47 AM
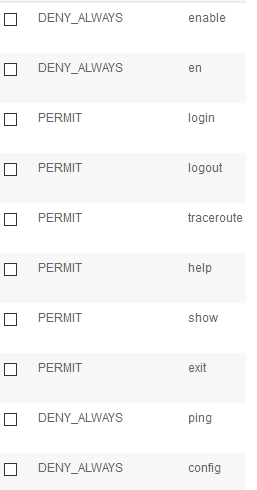
I want a simple command set, permit some commands (eg: show, dir, ping, traceroute ) but deny en or enable, intended that the user should never go to enable mode. My command set is as follows
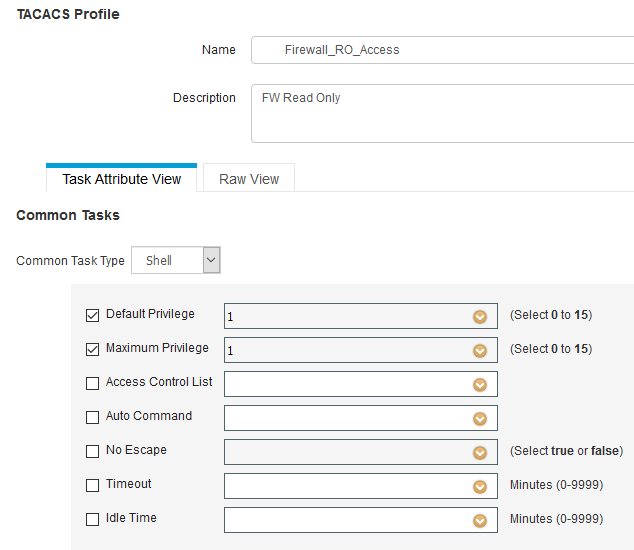
TACACS Profile
PS: Doesn't matter what priv level I use here.
Configuration on the ASA
aaa-server TACACS protocol tacacs+
aaa-server TACACS (inside) host x.x.x.x
aaa authentication ssh console TACACS LOCAL
aaa authentication http console TACACS LOCAL
aaa authentication serial console LOCAL
aaa authorization command TACACS LOCAL
aaa accounting ssh console TACACS
aaa authorization exec authentication-server
aaa authentication login-history
I read somewhere to enable 'aaa authorization config-commands' but I don't have that on my ASA (9.8)
What am I doing wrong?
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-15-2019 06:15 AM
In my opinion the concept of enable mode is a legacy concept that I haven't used in years with any of my customers. If you have command authorization enabled via TACACS it doesn't matter what mode you are in, you are authorizing and accounting for everything that is typed in. I have my customers send all users to the # prompt and then we authorize from there.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-15-2019 06:15 AM
In my opinion the concept of enable mode is a legacy concept that I haven't used in years with any of my customers. If you have command authorization enabled via TACACS it doesn't matter what mode you are in, you are authorizing and accounting for everything that is typed in. I have my customers send all users to the # prompt and then we authorize from there.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-15-2019 06:34 AM
Thank you, this is good.
I allowed priv users to enter exec mode on login and restricted commands, this works as expected. Do you know what the min / max priv level required for user to auto move to exec upon login? (1 didn't work, I moved to 5 and it worked, but that was random)
Btw, I am curious, why does the existing command set not work?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-15-2019 07:54 AM
aaa authorization exec authentication-server auto-enable
You had the command but didn't have the auto-enable key word at the end.
That will allow users directly into the # prompt. I am not sure why your command set didn't work. Would have to do further analysis on that.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-15-2019 08:39 AM
Thanks.
I meant to ask why the initial config for denying 'enable' after login doesn't work.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide