- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: ISE 2.6 alarm "Queue Link Error"
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-29-2019 01:37 AM
Hi ,
ISE 2.6 gives the alarm "Queue Link Error"
Description says :
All nodes are Up and Completely synced and has been up and running for more than 2 months. We have not restarted or resynced any of the nodes recently
Any ideas why we see this error?
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-20-2019 02:34 AM
Hi,
Am I missing something?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-20-2019 03:10 AM
Hi @ferenc.vissers ,
Please check if the CA service is running. Sample output from my lab:
ise101/admin# show application status ise
ISE PROCESS NAME STATE PROCESS ID
--------------------------------------------------------------------
Database Listener running 2427
Database Server running 106 PROCESSES
Application Server running 50634
Profiler Database running 4738
ISE Indexing Engine running 52494
AD Connector running 13555
M&T Session Database running 4547
M&T Log Processor running 9849
Certificate Authority Service running 13302
You can also go to Certificates -> Certificate Authority -> Internal CA settings and check if it shows running.
Please 'RATE' and 'MARK ACCEPTED', if applicable.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-20-2019 03:48 AM
Hi,
No, it's not running:
Certificate Authority Service disabled
It was not before either. We do not have any problem with the Queue Link errors (we use ISE only for TACACS+), so I'll rather wait for Cisco to fix it. Thanks anyway!
Regards,
Ferenc
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-28-2019 09:19 AM
Just ran into this issue (four node deployment running 2.6 patch 3). ISE live log / session log / TACACS logs not showing. Resolved by doing the following:
1. Regenerate ISE Root CA (cert services must be running as mentioned in a previous post)
2. Regenerate ISE Messaging Service Cert
3. All nodes rebooted
Logs are now all visible
Regards,
Keith.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-09-2020 12:02 PM
You will need to expand Certificate Authority at the bottom left of the menu and be sure to enable the ISE CA to be able to generate a CSR for the ISE Root CA Chain.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-02-2020 08:16 AM
Hello,
first you should have in Internal CA Settings (Enabled) and then the option to generate ISE ROOT CA will appear.
I've face the same issue on the proccess.
Regards,
Gustavo Garcia
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-28-2020 12:44 AM
Hi Arne,
We unfortunately upgraded from 2.4 to 2.6 patch 3 and we are getting hammered with this alarm!
Is the below fix is used when ISE acts as a CA server?
Because we are not using the ISE as SCEP proxy.
Please advise
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-28-2020 07:44 AM
@bern81 wrote:
Hi Arne,
We unfortunately upgraded from 2.4 to 2.6 patch 3 and we are getting hammered with this alarm!
Is the below fix is used when ISE acts as a CA server?
Because we are not using the ISE as SCEP proxy.
Please advise
Please work with TAC to debug and understand why this is happening.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-28-2020 07:58 AM
Hi Jason,
We opened already a ticket with TAC and waiting for cisco reply.
Quick question: Do you suggest any link on how to rollback to 2.4 in case cisco are not able to find a solution.
Because currently all our Radius logs are gone!
thank you in advance
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-28-2020 08:30 AM
@bern81 wrote:
Hi Jason,
We opened already a ticket with TAC and waiting for cisco reply.
Quick question: Do you suggest any link on how to rollback to 2.4 in case cisco are not able to find a solution.
Because currently all our Radius logs are gone!
thank you in advance
apologies, you can't roll back. if you can build a system in the old setup you can restore your old backup
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-28-2020 08:48 AM
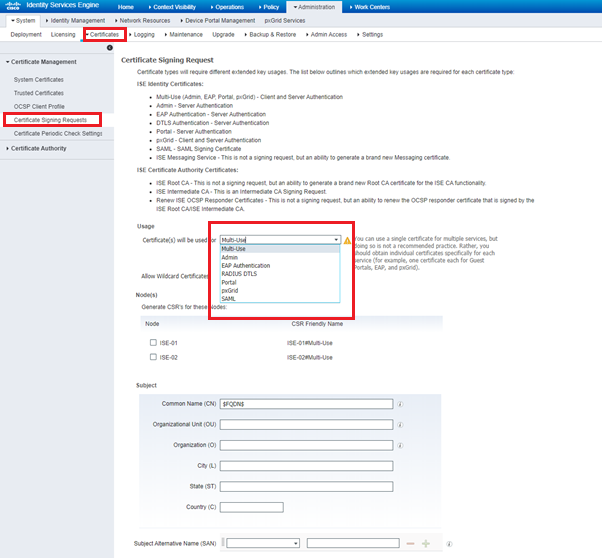
You likely need to regenerate your internal ISE CA chain if live logs are not working.
Administration > Certificates
Choose Certificate Signing Request on the left menu
Select to Generate a Certificate Signing Request
In the dialog, choose ISE Root CA from the dropdown list
Click Replace ISE Root CA Certificate chain
Short term you can also disable the ISE secure messaging service as well to rely on the legacy syslog communication.
Administration > Logging
Uncheck the option to use "ISE Messaging Service"
This will revert to using UDP 20514 to share information between ISE nodes
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-31-2020 05:40 AM
I was able to fix the Queue Link Error - cause unkonown CA with regenerating the root CA and messaging certificate.
Unfortunatly I hit another error after that which is also Queue Link Error but with the cause - basic-cancel.
I think I hit this Bug: https://bst.cloudapps.cisco.com/bugsearch/bug/CSCvs01949
Anyone knows a workarround to fix this?
Thanks
Matthias
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-17-2020 02:51 PM
How long did it take before you noticed it started working. The System Summary is still displaying the second server is still not there. Although, I just recently did it. Should I restart the servers or just let it go?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-25-2020 04:17 PM
I had the same issue on ISE 2.7 Patch 2, doing this resolved my issue. Thank you
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-05-2020 06:32 PM
Worked for me. Thanks @Dustin Anderson!
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide