- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: ISE 2.7 - Console TACACS login being blocked after adding Network Condition
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
ISE 2.7 - Console TACACS login being blocked after adding Network Condition
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-26-2021 08:29 PM
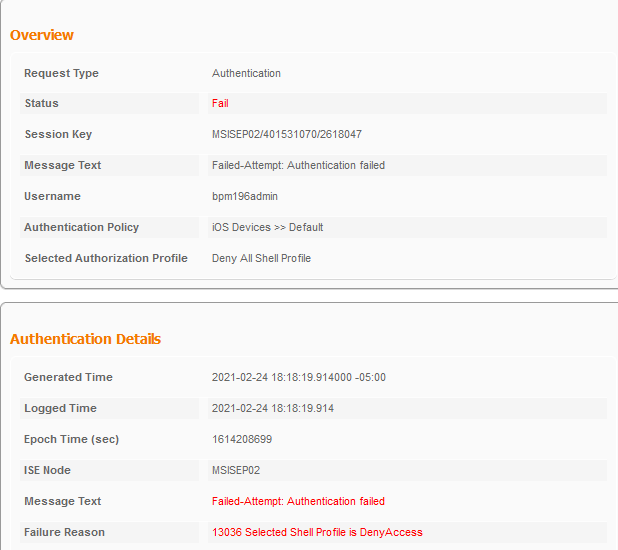
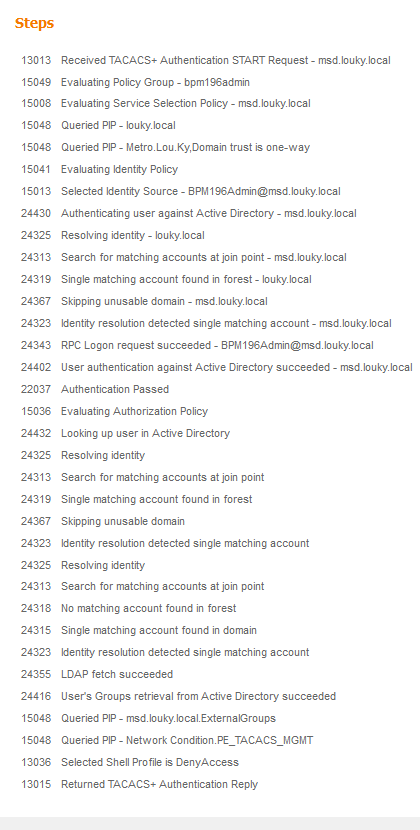
Hello. I recently added a Network Condition to my Device Admin Policy set. The idea is to only allow TACACS login from specific networks. This worked great, but now I cannot authenticate using Console (login authentication failed).
I feel like I could just add another condition in ISE for CONSOLE (because I would prefer to use TACACS for console authentication), but I cannot find the choice to add console
Please HALP
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-27-2021 11:29 AM
Are you able to share your AAA config, line con config, detailed t+ live log showing the failure, and your device admin policies so the community can better assist? Try taking a peek at the following to see if this will help: https://community.cisco.com/t5/security-documents/ise-device-administration-using-tacacs-and-radius/ta-p/3621655
HTH!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-27-2021 11:36 AM - edited 02-27-2021 11:38 AM
aaa new-model
aaa group server radius ISE
aaa group server tacacs+ ISE-TACACS
aaa authentication password-prompt **TACACS-DOWN_NON-TACACS-PASSWORD**
aaa authentication username-prompt **TACACS-DOWN_NON-TACACS-USERNAME**
aaa authentication login default group ISE-TACACS local
aaa authentication enable default group ISE-TACACS enable
aaa authentication dot1x default group radius
aaa authorization console
aaa authorization config-commands
aaa authorization exec default group ISE-TACACS if-authenticated
aaa authorization commands 0 default group ISE-TACACS if-authenticated
aaa authorization commands 1 default group ISE-TACACS if-authenticated
aaa authorization commands 15 default group ISE-TACACS if-authenticated
aaa authorization network default group radius
aaa accounting dot1x default start-stop group radius
aaa accounting exec default start-stop group ISE-TACACS
aaa accounting commands 0 default start-stop group ISE-TACACS
aaa accounting commands 1 default start-stop group ISE-TACACS
aaa accounting commands 7 default start-stop group ISE-TACACS
aaa accounting commands 15 default start-stop group ISE-TACACS
aaa session-id common
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-27-2021 03:29 PM
Hello Mike.
aaa new-model
aaa group server radius ISE
aaa group server tacacs+ ISE-TACACS
aaa authentication password-prompt **TACACS-DOWN_NON-TACACS-PASSWORD**
aaa authentication username-prompt **TACACS-DOWN_NON-TACACS-USERNAME**
aaa authentication login default group ISE-TACACS local
aaa authentication enable default group ISE-TACACS enable
aaa authentication dot1x default group radius
aaa authorization console
aaa authorization config-commands
aaa authorization exec default group ISE-TACACS if-authenticated
aaa authorization commands 0 default group ISE-TACACS if-authenticated
aaa authorization commands 1 default group ISE-TACACS if-authenticated
aaa authorization commands 15 default group ISE-TACACS if-authenticated
aaa authorization network default group radius
aaa accounting dot1x default start-stop group radius
aaa accounting exec default start-stop group ISE-TACACS
aaa accounting commands 0 default start-stop group ISE-TACACS
aaa accounting commands 1 default start-stop group ISE-TACACS
aaa accounting commands 7 default start-stop group ISE-TACACS
aaa accounting commands 15 default start-stop group ISE-TACACS
aaa session-id common
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-05-2021 05:23 AM
Since the selected profile is DenyAccess it seems that maybe you are not matching on the correct authz policy. Can you share how you have your authz policy configured so we can see the conditions being utilized?
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide