- Cisco Community
- Technology and Support
- Security
- Network Access Control
- ISE Authentication and Authorization help
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-11-2024 07:28 AM
Hi,
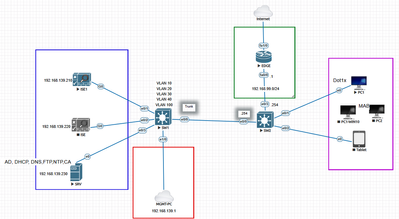
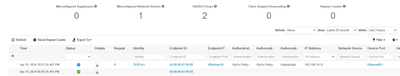
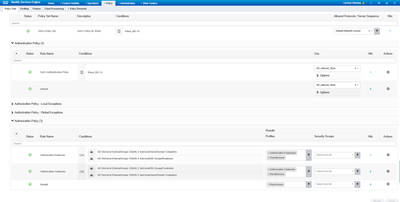
I'm working on a lab and have hit a brick wall. I've attached a screenshot of the lab top, ISE live log report, and policy set. If I remove the 802.1x config from the interface, the W10 host gets an address on the 192.168.20 VLAN. Thomas' How To Troubleshoot ISE Failed Authentications & Authorizations guide is great, but I still have issues. I would greatly appreciate any and all help.
Here's my switch configuration:
hostname SW2
!
boot-start-marker
boot-end-marker
!
!
!
aaa new-model
!
!
aaa group server radius ISE-GROUP
server name ISE1
server name ISE2
ip radius source-interface Vlan100
!
aaa authentication dot1x default group ISE-GROUP
aaa authorization network default group ISE-GROUP
aaa accounting update periodic 5
aaa accounting dot1x default start-stop group ISE-GROUP
!
!
!
!
!
aaa server radius dynamic-author
client 192.168.139.210 server-key 123Test
client 192.168.139.220 server-key 123Test
!
aaa session-id common
!
!
!
!
!
!
!
!
ip name-server 8.8.8.8
ip cef
no ipv6 cef
!
!
dot1x system-auth-control
!
spanning-tree mode pvst
spanning-tree extend system-id
!
no cdp run
!
!
!
!
!
!
!
!
!
!
!
!
!
!
interface Ethernet0/0
switchport trunk encapsulation dot1q
switchport trunk native vlan 100
switchport mode trunk
!
interface Ethernet0/1
description win10 node
switchport access vlan 20
switchport mode access
authentication event fail action next-method
authentication host-mode multi-auth
authentication order dot1x mab
authentication port-control auto
mab
dot1x pae authenticator
dot1x timeout tx-period 10
spanning-tree portfast edge
!
interface Ethernet0/2
description win10 node
switchport access vlan 20
switchport mode access
!
interface Ethernet0/3
description connected to Internet Router
no switchport
ip address 192.168.99.254 255.255.255.0
!
interface Ethernet1/0
!
interface Ethernet1/1
!
interface Ethernet1/2
!
interface Ethernet1/3
!
interface Vlan1
no ip address
!
interface Vlan10
ip address 192.168.10.1 255.255.255.0
ip helper-address 192.168.46.230
ip helper-address 192.168.139.230
!
interface Vlan20
ip address 192.168.20.1 255.255.255.0
ip helper-address 192.168.139.230
!
interface Vlan30
ip address 192.168.30.1 255.255.255.0
ip helper-address 192.168.46.230
ip helper-address 192.168.139.230
!
interface Vlan40
ip address 192.168.40.1 255.255.255.0
ip helper-address 192.168.46.230
ip helper-address 192.168.139.230
!
interface Vlan100
ip address 192.168.139.254 255.255.255.0
!
ip forward-protocol nd
!
ip http server
ip http secure-server
!
ip route 0.0.0.0 0.0.0.0 192.168.99.1
ip ssh server algorithm encryption aes128-ctr aes192-ctr aes256-ctr
ip ssh client algorithm encryption aes128-ctr aes192-ctr aes256-ctr
!
!
!
!
snmp-server community 123Test RO
!
radius-server attribute 6 on-for-login-auth
radius-server attribute 8 include-in-access-req
radius-server attribute 25 access-request include
radius-server dead-criteria time 30 tries 3
radius-server timeout 2
!
radius server ISE1
address ipv4 192.168.139.210 auth-port 1812 acct-port 1813
key 123Test
!
radius server ISE2
address ipv4 192.168.139.220 auth-port 1812 acct-port 1813
key 123Test
!
!
control-plane
!
!
line con 0
logging synchronous
line aux 0
line vty 0 4
!
!
!
radius server ISE1
address ipv4 192.168.100.210 auth-port 1812 acct-port 1813
key 123Test
radius server ISE2
address ipv4 192.168.100.220 auth-port 1812 acct-port 1813
key 123Test
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-11-2024 09:48 AM
ahollifield,
Things are working now. I wanted to dynamically assign an IP address to the host. That couldn't happen without an auth policy, so I assigned the 'Authorization Employees' profile, which assigns VLAN 10, to the 'Authorization Employee' policy. I think my other issue was having the wrong RADIUS address.
Thank you!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-11-2024 08:15 AM
Why are you sending two AuthZ results? Permit access and "Authorization Employee/Contractor". What do the logs on the switch show? What exactly is in those two authz profiles? Does it work if you put PermitAccess authz profile?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-11-2024 09:10 AM
Those two AuthProfiles were from another lab. To simplify things, I've removed them. Now, only PermitAccess is present. I've also fixed the IP address assigned to ISE1 and ISE2 in the Radius server configuration - they were 192,168.100 before. Now, they are 192.168.139.
I've bounced the switch port and Windows NIC, but it's still not pulling an IP address. More specifically, Windows reports "Unidentified Network" on the NIC. I'm missing something here. What might it be? The switch complained of the incorrect Radius addresses, but no longer. It also complained of authentication failure on eth0/1. That has stopped, too.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-11-2024 09:48 AM
ahollifield,
Things are working now. I wanted to dynamically assign an IP address to the host. That couldn't happen without an auth policy, so I assigned the 'Authorization Employees' profile, which assigns VLAN 10, to the 'Authorization Employee' policy. I think my other issue was having the wrong RADIUS address.
Thank you!
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide