- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: ISE dacl differnet than what switch is applying
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-04-2024 05:24 AM
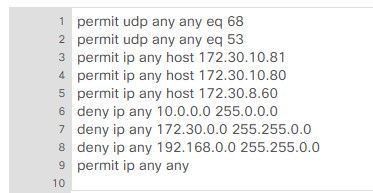
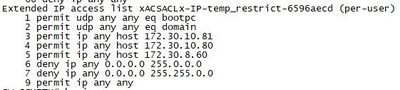
Deploying ISE and trying to finalize some restrictions. It seems the DACL defined in ISE is not what the switch is applying to the port. Any ideas why the switch is changing the deny statements?
- ISE 3.1 (patch
- C1000-8FP-E-2G-L
Here is what we have defined in ISE:
Here is what the switch is applying:
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-04-2024 05:32 AM - edited 01-04-2024 06:31 AM
@Chris S use the wildcard not the subnet mask when configuring the DACL.
Also you can use Check DACL Syntax to confirm the syntax is correct.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-04-2024 05:32 AM - edited 01-04-2024 06:31 AM
@Chris S use the wildcard not the subnet mask when configuring the DACL.
Also you can use Check DACL Syntax to confirm the syntax is correct.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-04-2024 09:20 AM
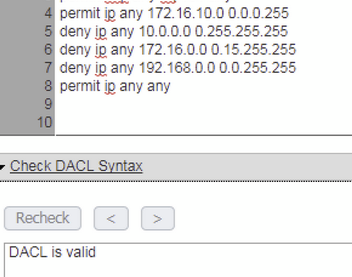
That was it - the syntax was valid against the ISE checker with a standard subnet.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-14-2025 09:56 AM
This is clear.
Based on this documentation:
https://www.cisco.com/c/en/us/td/docs/security/asa/asa-command-reference-convert/A-H/cmdref1/a2.html
Additional Guidelines
-
When you specify a network mask, the method is different from the Cisco IOS software access-list command. The ASA uses a network mask (for example, 255.255.255.0 for a Class C mask). The Cisco IOS mask uses wildcard bits (for example, 0.0.0.255).
So for switch/wlc you should write down dACL in ISE with wildcard on your mind, but what about ASA in this case ?
So am I right if I said it has different result when I use the same dACL in one case for:
- with switch/wlc
and
on another case for ASA/FTD ?
For example in case I need to allow comunication from any to X.Y.0.0/16.
I should solve it like this:
permit ip any X.Y.0.0 0.0.255.255 syntax for dacl used in authz prof for switch/wlc.
but I should use different dACL syntax for ASA/FTD:
permit ip any X.Y.0.0 255.255.0.0 syntax for dacl used in authz prof for asa/ftd.
or
I could use the same dACL for switch/wlc, but than I have to use acl-netmask-convert in AAA radius server group in ASA/FTD either with auto-detect or wildcard.
I assume using dACL with wildcard syntax needed for switch/wlc in case with ASA breaks thinks with error something like this.
ERROR: IP address,mask <X.Y.0.0,0.0.255.255> doesn't pair
Am I right ?
acl-netmask-convert
To specify how the ASA treats netmasks received in a downloadable ACL from a RADIUS server that is accessed by using the aaa-server host command, use the acl-netmask-convert command in aaa-server host configuration mode. To remove the specified behavior for the ASA, use the no form of this command.
acl-netmask-convert { auto-detect | standard | wildcard }
Syntax Description
Defaults
By default, no conversion from wildcard netmask expressions is performed.
Use the acl-netmask-convert command with the wildcard or auto-detect keywords when a RADIUS server provides downloadable ACLs that contain netmasks in wildcard format. The ASA expects downloadable ACLs to contain standard netmask expressions whereas Cisco VPN 3000 series concentrators expect downloadable ACLs to contain wildcard netmask expressions, which are the reverse of a standard netmas expression. A wildcard mask has ones in bit positions to ignore, zeros in bit positions to match.The acl-netmask-convert command helps minimize the effects of these differences upon how you configure downloadable ACLs on your RADIUS servers.
The auto-detect keyword is helpful when you are uncertain how the RADIUS server is configured; however, wildcard netmask expressions with “holes” in them cannot be unambiguously detected and converted. For example, the wildcard netmask 0.0.255.0 permits anything in the third octet and can be used validly on Cisco VPN 3000 series concentrators, but the ASA may not detect this expression as a wildcard netmask.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide