- Cisco Community
- Technology and Support
- Security
- Network Access Control
- ISE detecting common ports under nmap
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-05-2020 06:43 PM
I am trying to use create a profile using ISE 2.7 Patch 1, to use common ports that are scanned through NMAP. The devices are linux devices and I want to detect port 22 (SSH). When ISE does the scan, on the device I get all of the attributes with the exception of the NMAP scans for the port. I do have NMAP configured as part of profiling, so the issue is not there.
When I run an NMAP scan from my computer, I can detect the ports fine. I'm at a lost to see what I can do to get ISE to detect the common ports and profile them under the endpoint attribute.
Paul
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-23-2020 06:50 PM - edited 08-23-2020 06:51 PM
Found the issue. It turns out that the 'Endpoint Attribute Filter' was checked under Administration-> System->Settings-> Profiling. Once I unchecked it and cleared the auth sessions on the switch I was unable to retrieve all of the in NMAP information.
Thanks Greg for your help!
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-05-2020 08:50 PM
There are a lot of moving parts behind how the NMAP Profiling Probe works, so please review the steps in the ISE Profiling Design Guide if you haven't done so already.
Some of the typical reasons for the NMAP triggered scans not working:
- Either a network or host firewall is blocking the scan. The triggered scans are initiated by the PSNs, so make sure you have full access between the PSN and the client endpoint.
- ISE has not learned the IP address of the endpoint from either DHCP 'ip-helper' or Device Sensor.
- The NMAP scan action has not been configured for the Profiling Policy that the endpoint is hitting. For example, if the endpoint is getting profiled as Dell Device based on the MAC address, you need to enable the NMAP Scan Action for that Policy and either create your new Linux profile as a child policy or as a new root parent policy with a higher certainty factor.
You should note that all of the built-in Linux profiling policies in the Workstation parent policy are based on User-Agent strings. If you are not redirecting traffic to the PSNs (for flows like Guest, BYOD, etc), ISE will never see HTTP traffic from these endpoints. As such, it will never get the User-Agent string to match that policy.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-10-2020 07:48 AM
All listed were checked and verified. I am seeing UDP-port 161 coming across, but I am not specifically seeing SSH-port 22 even though it's a console device. Prior to the 2.7 upgrade this was coming across.
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-10-2020 04:08 PM
I tested an NMAP Common Ports scan with a Linux VM in my lab with ISE 2.7 p2 and it worked as expected. My 2.7 instance is a fresh install, but you might need to take a packet capture on ISE and the PC to see whether ISE is triggering the scan and if the PC is seeing the traffic.
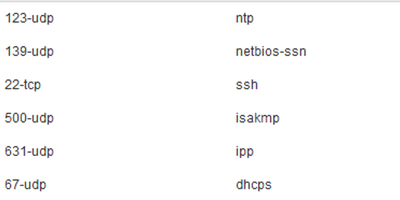
Example attributes from Context Visibility:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-23-2020 06:50 PM - edited 08-23-2020 06:51 PM
Found the issue. It turns out that the 'Endpoint Attribute Filter' was checked under Administration-> System->Settings-> Profiling. Once I unchecked it and cleared the auth sessions on the switch I was unable to retrieve all of the in NMAP information.
Thanks Greg for your help!
Paul
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide