- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: ISE device authentication local and AD in one policy
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-13-2020 04:38 AM
Hello,
I have a little issue to configure policy to TACACS+ device authentication to authorize users from local and AD users on one policy.
In first policy when the user is not found in local store then the second option is not taken - AD Domain.
If user is not found in local policy then is found in domain store but do not place in proper authorization policy.
Is there any option to combine local and AD store in one policy?
Solved! Go to Solution.
- Labels:
-
Device Admin
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-14-2020 03:50 PM
Something I want to clarify about your Authentication Policy. The option for 'If user not found = CONTINUE' means that the session will continue to the Authorization Policy. It does not mean that the session will continue to the next Authentication Policy rule, so your second AuthC rule for 'AD' will never be hit.
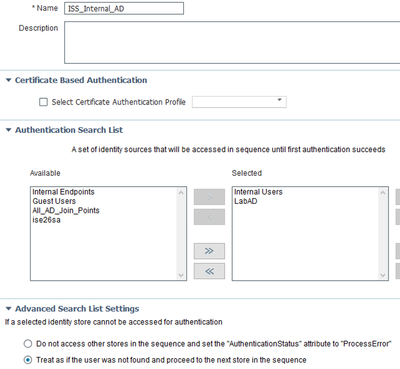
As @paul mentioned earlier, you need to use an Identity Source Sequence in your AuthC policy to achieve what you are trying to do and ensure the option for 'Treat as if the user was not found and proceed to the next store in the sequence' is ticked.
Example:
Secondly, I would suggest the following for the issue where the session is not hitting your AuthZ Policy Rule for the AD Group match.
- Use the Test User lookup tool in ISE (In the AD config section) and confirm that ISE sees the correct group membership for the AD user account.
- Ensure the user account used to join the domain as well as the machine account have the correct permissions as per the Active Directory Integration with Cisco ISE 2.x guide (especially the read tokenGroups permission)
If all else fails, you may need to open a TAC case to gather debugs and investigate further.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-13-2020 06:50 AM
You authentication policy is wrong. You almost never want to setup User Not found to Continue when you are using credential based authentication. You should be using a sequence which is the proper way to do this.
Setup an identity source sequence called AD_Local. Put AD first in the list then Internal Users. Just use the default authentication rule and tie it to the AD_Local sequence.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-13-2020 12:14 PM
Thanks for your replay.
The Internal user can login successful but the AD user is not. The AD user stay in authentication policy even if authentication passed.
Can you clarify me about attributes in line below 24100.
The AD user can log in when the policy is without internal store rule.
I have tested with group fetched from AD but the result is the same.
24420 User's Attributes retrieval from Active Directory succeeded
24100 Some of the expected attributes are not found on the subject record. The default values, if configured, will be used for these attributes
15048 Queried PIP - Poznan.zvni.com.ExternalGroups
13015 Returned TACACS+ Authentication Reply
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-13-2020 08:58 PM
Kindly refer below community link:
Also make sure that the AD user is a member of Netops identity group on AD as per the configured authorization rule.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-14-2020 05:21 AM
@poongargthanks for reply and attributes explanation.
I don't know what I'm going wrong but the tested user is a member of Netops group in AD but it cannot be authorized properly.
I was created simply rule but it's not work properly.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-14-2020 03:50 PM
Something I want to clarify about your Authentication Policy. The option for 'If user not found = CONTINUE' means that the session will continue to the Authorization Policy. It does not mean that the session will continue to the next Authentication Policy rule, so your second AuthC rule for 'AD' will never be hit.
As @paul mentioned earlier, you need to use an Identity Source Sequence in your AuthC policy to achieve what you are trying to do and ensure the option for 'Treat as if the user was not found and proceed to the next store in the sequence' is ticked.
Example:
Secondly, I would suggest the following for the issue where the session is not hitting your AuthZ Policy Rule for the AD Group match.
- Use the Test User lookup tool in ISE (In the AD config section) and confirm that ISE sees the correct group membership for the AD user account.
- Ensure the user account used to join the domain as well as the machine account have the correct permissions as per the Active Directory Integration with Cisco ISE 2.x guide (especially the read tokenGroups permission)
If all else fails, you may need to open a TAC case to gather debugs and investigate further.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-18-2020 11:49 AM
Thanks guys, all suggestions were helpful.
The issue resolved by rejoin to AD domain.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide