- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: ISE - EAP-FAST certificate for machine and MSCHAP for user authentication
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-09-2020 03:13 PM - edited 09-09-2020 03:14 PM
Hello,
Does anyone know what is the correct way to configure
Policy Set for EAP-FAST when NAM uses certificate machine authentication and MSCHAP user authentication ?
I have this policy but I doubt this is the correct one.
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-17-2020 01:29 PM - edited 09-17-2020 01:40 PM
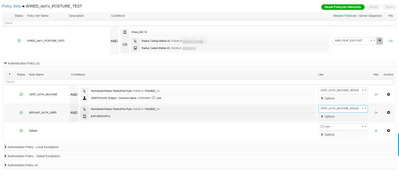
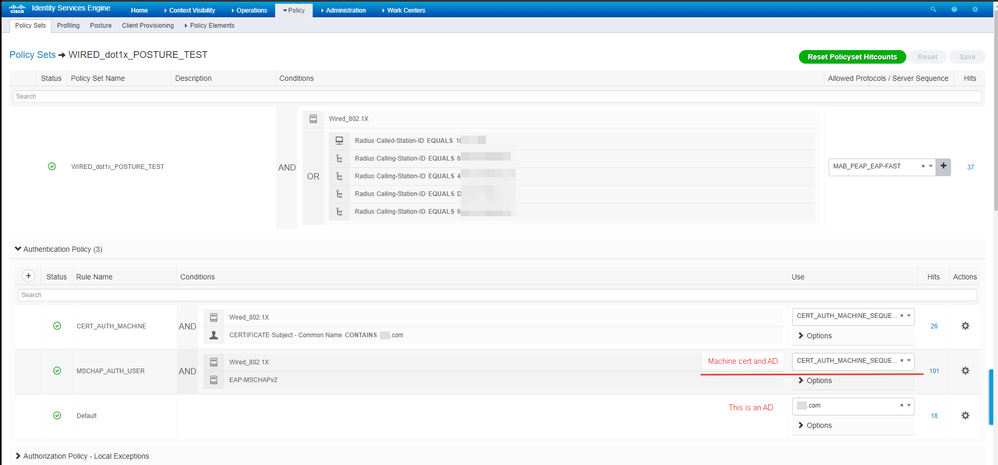
Let me share my masterpiece of Policy Set configuration and comments. I tested a lot and not it works.
Please correct this if there is something missing.
So we are doing EAP-FAST with machine certificate and user MSCHAP authentication.
Authentication should contain a cert verification for both MACHINE authentication and then for USER auth with MSCHAP otherwise the result for authz is always "user succeeded and machine failed".
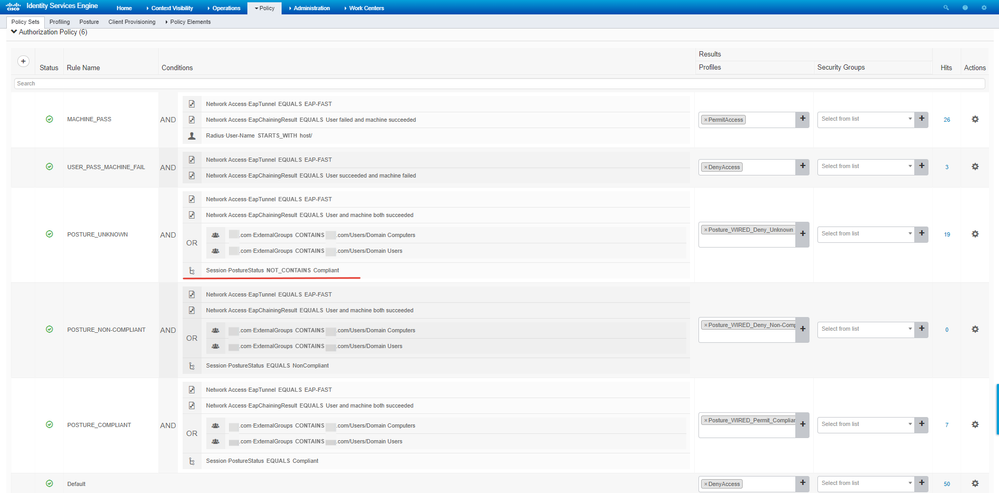
For my scenario POSTURE is verified.
So there should be some references to that in order to match the correct policy.
At the same time we don't need any non-domain PCs to be able to connect to the LAN.
For my test the first state for posture before assessment is Posture Status ==NotApplicable so we cannot use UNKNOWN to match the rule.
NOT_CONTAINS == Compliant or
NOT_ENDS_WITH == Compliant works to match the rule POSTURE_UNKNOWN for that state AND to skip it WHEN the status is changed to Non-Compliant or Compliant in order to match lower rules.
Other details are on the screenshots.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-09-2020 09:38 PM
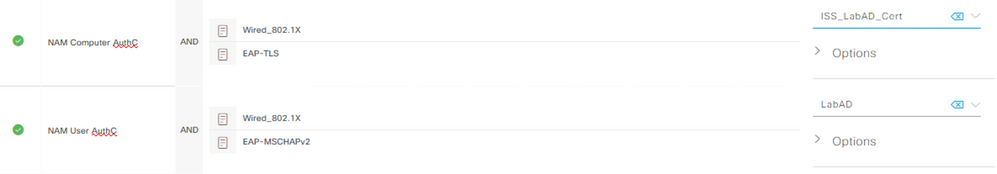
You don't want to use a Cert Auth Profile for EAP-MSCHAPv2 as the client does not present a certificate. For this scenario, I would create an Identity Source Sequence with the CAP and AD Join Point (ISS_LabAD_Cert) to use for the EAP-TLS (Computer) session and use just the AD Join Point (LabAD) for the EAP-MSCHAPv2 (User) session. I would then use the EAP method to differentiate between the two.
Example:
You can use additional checks against the certificate (CN, Issuer, etc) if you choose, but ISE will verify that the certificate is signed by a CA in its Trusted Store as part of the AuthC process.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-10-2020 09:28 AM - edited 09-10-2020 09:47 AM
Hello, Greg.
One concern:
On my screenshot if I disable the 2nd rule (MSCHAP_AUTH_USER) the "Default" one matches for user authentication.
In this case if a user enters wrong credentials, ISE shows an issue in logs:
22045 Identity policy result is configured for password based authentication methods but received certificate based authentication request.
Then if a user enters correct credentials ISE authenticates the PC only after 60 seconds (I can see that on ISE Radius logs).
However, if the 2nd rule is enabled nothing happen in logs if enter wrong credentials.
Correct me if I am wrong:
First a PC has machine authentication successful based on a certificate.
Then user logs in and enters credentials and the PC (using EAP-FAST) sends a machine certificate again along with user authentication.
For your example:
assuming I am using a non-domain PC without a trusted certificate for machine authentication ( so machine authentication will fail).
Will authentication with user AD credentials (only) successfully pass and let PC to the network even without successful machine authentication ?
The whole idea is to use a stronger certificate based verification for a machine and for a user, but because of limitations for NAM connections we cannot user certificate for user authentication:
( https://community.cisco.com/t5/vpn/anyconnect-nam-eap-fast-user-certificate-issue/td-p/4145877#M1879 ) .
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-10-2020 02:50 PM
Hello,Greg.
One concern:
For your example will this Policy with your rules authenticate users without machine certificate ?
Because it looks like if AD credentials are correct certificate will not be checked by ISE.
For EAP-FAST first authenticates with a machine certificate. Then user logs in by signing credentials. A PC sends both a machine certificate and user credentials. For that reason I used a profile with certificate. It should be only AD credentials checking ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-10-2020 03:46 PM
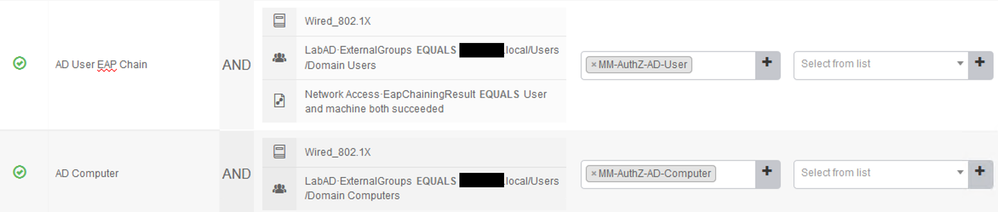
Yes, a user without a machine certificate will authenticate if MSCHAPv2 is configured, but EAP Chaining controls are done in the AuthZ Policy, not the AuthC Policy.
You would configure an AuthZ rule that uses the 'User and machine both succeeded' condition as per the below example. If you prefer, you could fine-tune the policy with matches on specific EAP protocols and/or create another rule below to redirect users that fail the EAP Chaining condition to a BYOD flow, etc. It all depends on your requirements.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-17-2020 01:28 PM
Hello, Greg.
Thank you for your answers.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-17-2020 01:29 PM - edited 09-17-2020 01:40 PM
Let me share my masterpiece of Policy Set configuration and comments. I tested a lot and not it works.
Please correct this if there is something missing.
So we are doing EAP-FAST with machine certificate and user MSCHAP authentication.
Authentication should contain a cert verification for both MACHINE authentication and then for USER auth with MSCHAP otherwise the result for authz is always "user succeeded and machine failed".
For my scenario POSTURE is verified.
So there should be some references to that in order to match the correct policy.
At the same time we don't need any non-domain PCs to be able to connect to the LAN.
For my test the first state for posture before assessment is Posture Status ==NotApplicable so we cannot use UNKNOWN to match the rule.
NOT_CONTAINS == Compliant or
NOT_ENDS_WITH == Compliant works to match the rule POSTURE_UNKNOWN for that state AND to skip it WHEN the status is changed to Non-Compliant or Compliant in order to match lower rules.
Other details are on the screenshots.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide