- Cisco Community
- Technology and Support
- Security
- Network Access Control
- ISE IOS CLI Authentication Quandry
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-28-2015 07:35 AM - edited 03-10-2019 10:41 PM
Im trying to push the limits of ISE, since tacacs+ isnt supported yet. The goal is to authenticate switches and routers using radius against ISE. I think I am on the right track, since I can login against ISE. However, when I login to enable the ISE Authorizations log shows Radius status fail, with a failed attempt from user $enabl15$.
I have my device added to ISE. An authorization profile has been created for each privilege level, I am using policy sets and have the correct authz and autht policies. Below are the examples of my ISE configuration and router configuration. Hopefully it helps fix my problem, or it may help the next troller with success of their own configuration.
Auth Profile: When choosing priv-lvl=15 after hitting save, web auth is automatically selected.

Policy Set:
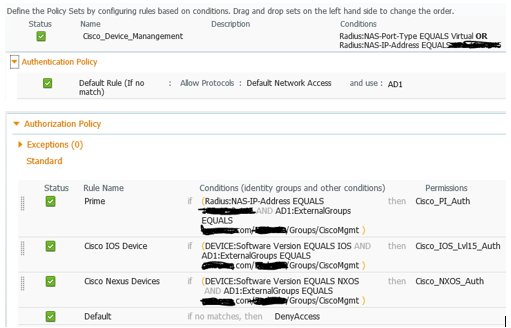
router configuration
aaa group server radius Rad_AUTH1
server name Rad_Auth
!
aaa authentication login CONSOLE local
aaa authentication login Rad_Auth group Rad_AUTH1 local none
aaa authentication enable default group Rad_AUTH1 enable none
aaa authorization exec default none
aaa authorization exec Rad_Auth group Rad_AUTH1 if-authenticated
aaa accounting exec default start-stop group radius
!
radius server Rad_Auth
address ipv4 x.x.x.x auth-port 1645 acct-port 1646
timeout 3
key 7 052F302B3B7E491B41
line vty 0 4
session-timeout 30
exec-timeout 30 0
authorization exec Rad_Auth
login authentication Rad_Auth
transport input ssh
Solved! Go to Solution.
- Labels:
-
AAA
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-03-2015 10:56 PM
Glad you got your own issue resolved! Also, thank you for taking the time to come back and post the solution here! (+5 from me).
Since the issue is resolved you should mark the thread as "answered" :)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-28-2015 03:17 PM
Hmm, I don't see anything wrong from the surface...the only thing I have not done in comparison to your config is returning the Advanced Radius Attribute of "Service-Type = Login" Can you try removing it and see if makes a difference?
Also, have you done any debugs? If not perhaps you can debug aaa authorization and debug radius and then post the results here.
Thank you for rating helpful posts!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-29-2015 04:04 AM
Thanks for the reply Neno. I got it worked out and will be submitting a new document for future trollers. There were a couple things I had to change in both ISE and in IOS.
In IOS
aaa authentication login default group radius local none
aaa authentication login CONSOLE local
aaa authentication enable default group radius enable none
aaa authorization exec default group radius local
In ISE the AuthZ and AuthT policies worked, but didnt give the results I wanted. For example, since radius uses the $enabl$ as a username for the privilege level I had to put a deny at the end of each policy. Without it, enable would go to the next default rule, it also allowed a priv 5 to type in enable and get priv 15 access.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-03-2015 10:56 PM
Glad you got your own issue resolved! Also, thank you for taking the time to come back and post the solution here! (+5 from me).
Since the issue is resolved you should mark the thread as "answered" :)
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide