- Cisco Community
- Technology and Support
- Security
- Network Access Control
- ISE RBAC for Policy Set so team can view but not edit
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-11-2021 11:34 AM
I'm running ISE 3.0 and and older version of ISE 2.2 which I have ran into some rbac issues. On ISE 3.0, is it possible to provide menu access to view the policy sets but not make any changes? I tried a few different ways, but seems to either allow changes or I see permission denied.
Thanks,
-Scott
*** Please rate helpful posts ***
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-04-2021 08:35 PM
Unfortunately, that is not currently supported.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-13-2021 06:09 PM
Need a separate user login as a "read-only" admin user, which is introduced in ISE 2.6.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-13-2021 08:10 PM
hslai,
Any way to allow access to some things like endpoints/endpoint groups but read-only with everything else? If not, might just have to create a separate user for them to modify their endpoint and groups.
*** Please rate helpful posts ***
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-04-2021 08:35 PM
Unfortunately, that is not currently supported.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-27-2021 04:25 PM
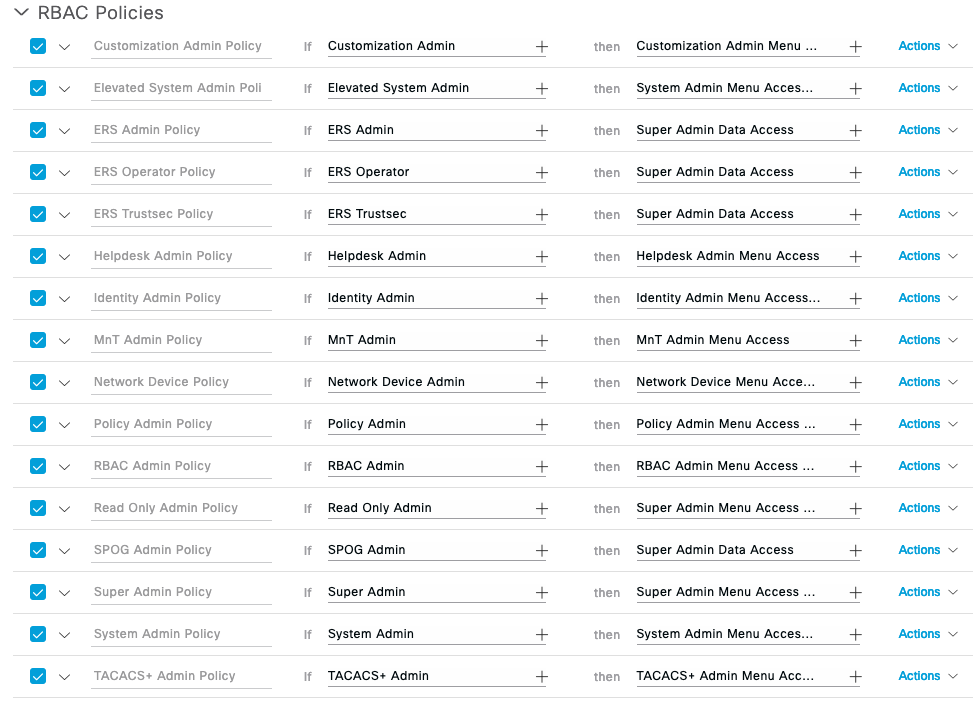
These are your ISE Admin Group options:
- Customization Admin: Access Permission to Guest Menu and Device Portal Management.
ERS Admin: Full access permission to External RESTful Services (ERS) APIs. Admins assigned to this admin group can perform CRUD (POST, PUT, DELETE, and GET) operations. - ERS Operator: Read-only access permission to the External RESTful Services (ERS) APIs. Admins assigned to this admin group can only perform GET operation.
- Elevated System Admin: Access permission for Operations tab. Includes System and data access permission for Admin Groups and Admin Users except Super Admin group and users.
- Helpdesk Admin: Access permission for Operations tab.
- Identity Admin: Access permission for Operations tab. Includes Identity Management and data access permission for User Identity Groups and Endpoint Identity Groups.
- MnT Admin: Access permission for Operations tab.
- Network Device Admin: Access permission for Operations tab. Includes Network Resources and data access permission for All Locations and All Device Types.
- Policy Admin: Access permission for Operations and Policy tabs. Includes System and Identity Management and data access permission for User Identity Groups and Endpoint Identity Groups.
- RBAC Admin: Access permission for Operations tab. Includes System and data access permission for Admin Groups.
- Read Only Admin: Access Permission for admin with read-only functionality
- SPOG Admin: This is the group for SPOG Admin to use the APIs for export and import
- Super Admin: Access permission for Operations, Policy and Administration tabs. Includes data access permission for Admin Groups, User Identity Groups, Endpoint Identity Groups, All Locations and All Device Types.
- System Admin: Access permission for Operations tab. Includes System and data access permission for Admin Groups.
You may also create your own useing the ISE RBAC Policy in ISE 2.6+:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-23-2022 01:53 AM
Hello! Is it possible to create a policy for read only access for every tabs except Operations Tab? I need to give a user an access to download logs and reports but the rest tabs must be the read only access.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-23-2022 02:12 AM
I think you need to try duplicate one of the available and try that options and test using user that belong to group.
never tried myself some read and some write access.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide

