- Cisco Community
- Technology and Support
- Security
- Network Access Control
- ISE: Reauthentication Timers
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
ISE: Reauthentication Timers
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-27-2019 01:07 AM
Good day all,
I'm having some trouble understanding the reauthentication timers or configuration on IOS and ISE.
We are using the "Closed Mode"-deployment, where we authenticate clients with certificates or mac address and security groups in Active Directory to tell the switchport which VLAN to use. That works fine with our current setup (but with some issues with PXE, where we have to set the tx-period differently on different switch models).
We've deployed IP-Phones (not Cisco) with integrated pass-through port for computers, which we have to keep in mind.
This is the default switchport configuration we deploy for all our switches since we migrated from ACS to ISE.
interface GigabitEthernet0/48
description Default
switchport access vlan XX
switchport mode access
switchport voice vlan XX
authentication control-direction in
authentication event server dead action authorize vlan XX
authentication event server dead action authorize voice
authentication event server alive action reinitialize
authentication host-mode multi-domain
authentication order dot1x mab
authentication priority dot1x mab
authentication port-control auto
authentication periodic
authentication timer reauthenticate server
authentication timer inactivity server dynamic
authentication violation restrict
mab
dot1x pae authenticator
dot1x timeout tx-period 5
dot1x max-reauth-req 3
spanning-tree portfast edge
spanning-tree bpduguard enable
spanning-tree guard root
!
Now the main issue is that the ISE live logs gets spammed with "Session is started" messages or reauthentications (sometimes simultaneously when the switch was rebooted and all devices authenticated at the same time). My understanding was that if we set "authentication timer reauthenticate server" the ISE dictates the timers, and if we don't set timers on the ISE the reauthentication is disabled. Well that was wrong...
So how can I do better on ISE and the switches to get the optimal results?
Thanks.
- Labels:
-
Identity Services Engine (ISE)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-27-2019 01:37 AM
Hello Maxee
The default configuration on your setup sets your endpoints to be re-authenticated every 1h hour. If you believe that's too often try changing you command manually
authentication timer <seconds> or change the Session-Timeout attribute on ISE. Otherwise, some devices for some reason keep reauthenticating which you need to dig in further.
Also, do you need multidomain authentication? Do you authenticate your IP phones as well?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-27-2019 02:01 AM
If I set the Reauthentication in ISE what is the recommended duration? Or should I remove the three reauthentication settings from the switchport completely? Does that make a difference?
And yes we need multi-domain as we authenticate our phones with MAB and only 1 phone and 1 host is allowed per switchport
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-27-2019 02:51 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-27-2019 03:32 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-27-2019 07:18 AM
Yes, with the config listed you have enabled re-auth, and told it to honor settings from AAA. It's subtle, but RFC-3580 gives guidance for when you send (for example) a session-timeout, but does not discuss when you do not send it ;-). Also, static re-auth on a port (with yes, a default timer of one hour) pre-dated bringing in support of this over RADIUS. Thus, to support backward compatibility, the switch treats whatever AAA to do with priority, else falls back to what's configured locally. Now, if you want to disable re-auth for groups (or some, most, etc.) of devices, then setting session-timeout to zero on ISE should give the session an otherwise infinite session-time (as if re-auth was not enabled for that session).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-27-2019 11:48 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-27-2019 09:57 AM
You can track this via "Active Endpoints" on your home Summary dashboard. These active endpoints are determined by the Radius accounting state. Another area that can assist with tracking active sessions is under Operations->Radius->Live Sessions
But if there is nothing important that speaks for re-authentication then we could probably disable it.
In my opinion this would be something that is determined by your requirements. I know that if you work in the DoD there is a STIG requirement that requires 8021x reauthentication every 60 minutes.
HTH!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-27-2019 11:47 AM
If devices reauthenticate every 18 hours we don't have to manually reauthenticate them with CoA to pull new configurations. Hm.. Difficult
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-27-2019 02:21 PM
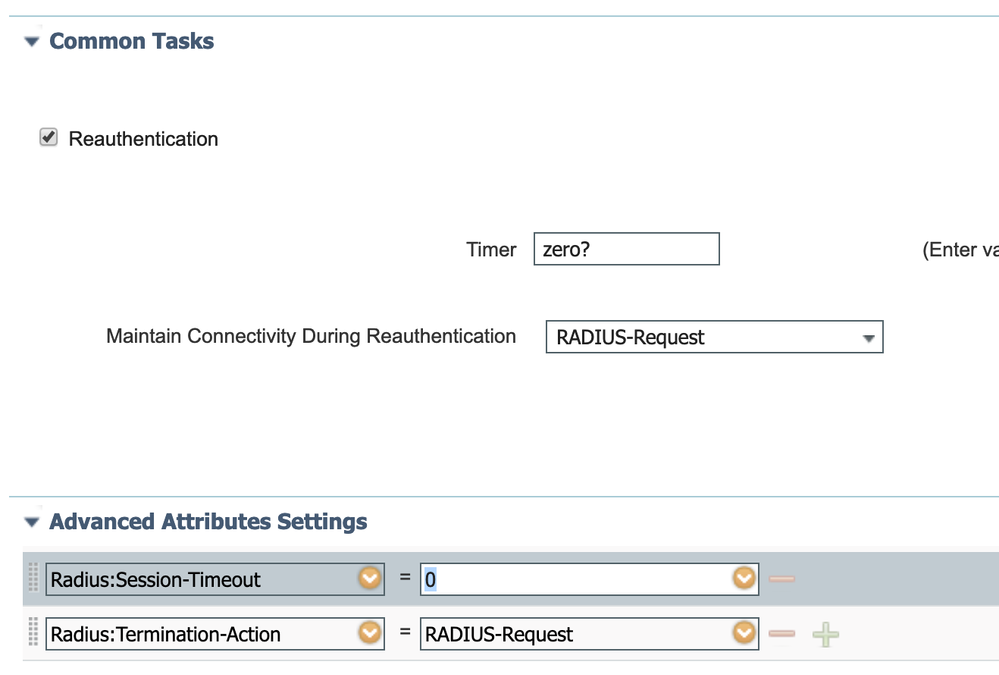
I am discussing this internally with jafrazie. Can you post result of 'show authentication session interface XXX' command for the interface? Also, can you post Catalyst platform and IOS version? I've tested this recently and when ISE doesn't send any value the result was that no reauthentication timer was applied to the session. Lastly if you want to provide '0' value then use Advanced Attributes Settings as shown below:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-28-2019 01:48 AM - edited 02-28-2019 01:49 AM
I have noticed that MAB seems to always have a reauthentication timer and 802.1X sometimes... That's also what I've noticed in the repeat count report on ISE that most devices with repeats are MAB-Devices and sometimes in between there are 802.1X-Devices.
That's on the same Switch (WS-C3560X-48P @ 15.2(4)E7)
All of these examples are without ISE sending timers, just VLAN-IDs
802.1x but somehow there is a reauthentication timer:
sh authentication sessions int g0/23 details
Interface: GigabitEthernet0/23
MAC Address: 90b1.xxxx.xxxx
IPv6 Address: Unknown
IPv4 Address: xx.xx.xx.xx
User-Name: dummy123.cisco.com
Status: Authorized
Domain: DATA
Oper host mode: multi-domain
Oper control dir: in
Session timeout: 3600s (server), Remaining: 2222s
Timeout action: Reauthenticate
Restart timeout: N/A
Periodic Acct timeout: 172800s (local), Remaining: 74118s
Common Session ID: 0A1001380000008C163C1C71
Acct Session ID: 0x0000008C
Handle: 0xE100003F
Current Policy: POLICY_Gi0/23
Local Policies:
Service Template: DEFAULT_LINKSEC_POLICY_SHOULD_SECURE (priority 150)
Server Policies:
Vlan Group: Vlan: 7
Method status list:
Method State
dot1x Authc Success
802.1x without session timers
sh authentication sessions int g0/34 details
Interface: GigabitEthernet0/34
MAC Address: 90b1.xxxx.xxx2
IPv6 Address: Unknown
IPv4 Address: xx.xx.xx.xx
User-Name: dummy1.cisco.com
Status: Authorized
Domain: DATA
Oper host mode: multi-domain
Oper control dir: in
Session timeout: N/A
Restart timeout: N/A
Periodic Acct timeout: 172800s (local), Remaining: 169100s
Common Session ID: 0A1001380000010E2650A11E
Acct Session ID: 0x00000127
Handle: 0x0200009A
Current Policy: POLICY_Gi0/34
Local Policies:
Service Template: DEFAULT_LINKSEC_POLICY_SHOULD_SECURE (priority 150)
Server Policies:
Vlan Group: Vlan: 401
Method status list:
Method State
dot1x Authc Success
MAB with session timers:
sh authentication sessions int g0/36 details
Interface: GigabitEthernet0/36
MAC Address: 0017.xxxx.xxxx
IPv6 Address: Unknown
IPv4 Address: 10.xx.xx.xx
User-Name: xx-xx-xx-xx-xx-xx
Status: Authorized
Domain: DATA
Oper host mode: multi-domain
Oper control dir: in
Session timeout: 3600s (server), Remaining: 2778s
Timeout action: Reauthenticate
Restart timeout: N/A
Periodic Acct timeout: 172800s (local), Remaining: 91247s
Common Session ID: 0A1001380000009F174172BC
Acct Session ID: 0x000000A0
Handle: 0xF500004F
Current Policy: POLICY_Gi0/36
Local Policies:
Service Template: DEFAULT_LINKSEC_POLICY_SHOULD_SECURE (priority 150)
Server Policies:
Vlan Group: Vlan: 118
Method status list:
Method State
dot1x Stopped
mab Authc Success
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-28-2019 04:34 AM
On the MAB example you have, it shows the the timer was from the server. Can you confirm that ISE is not sending the 3600 value? If ISE is sending without a authorization profile stating the timer, then that would be a defect on ISE. If ISE is not sending anything and the switch is applying it and indicating that it is from the server, then that would be a defect on the switch.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-28-2019 05:07 AM
On the ISE that attribute is not set. And on the switch It's also not configured (maybe a default setting?).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-28-2019 05:12 AM
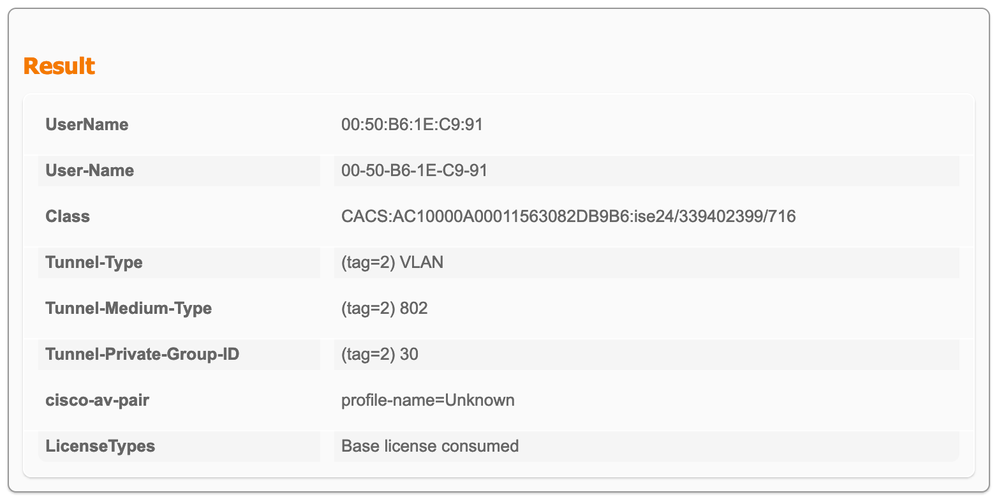
I wonder if there is ghost attributes being sent. Can you go to the details of the live log event for specific endpoint and look at the 'Result' section. You should see it at the bottom of the report. For my VLAN assignment I only see the 3 attributes. If you see additional attributes here for reauth then you may need to delete the authorization profile and recreate it. The other thing I would try is do a 'shut/no shut' in the interface to clear any previous settings (Although I doubt will make any difference would suggest to start cleanly).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-28-2019 05:36 AM
I disabled authentication periodic on another interface and then the timer was 3600s (local), even after port bounce... After I re-enabled server reauthentication timers the timer was set to 3600s (server). After a port bounce it was N/A.
That's pretty interesting...
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide