- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: ISE should not use default policy set for dot1x auth!
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-03-2017 02:31 AM
Hello together,
I have configured a wired LAN authentication and I have fully configured the switches, the policies are according to documentations and everything I could think of seems to be set correctly.
Now the issue is, when I connect my devices (using LAN cables) to the switches, the default policy is being selected (see Screenshot -> Authentication Policy), even though "Radius NAS-PORT-TYPE = Ethernet & Device Type = Device Group Switches (my radius switches)!

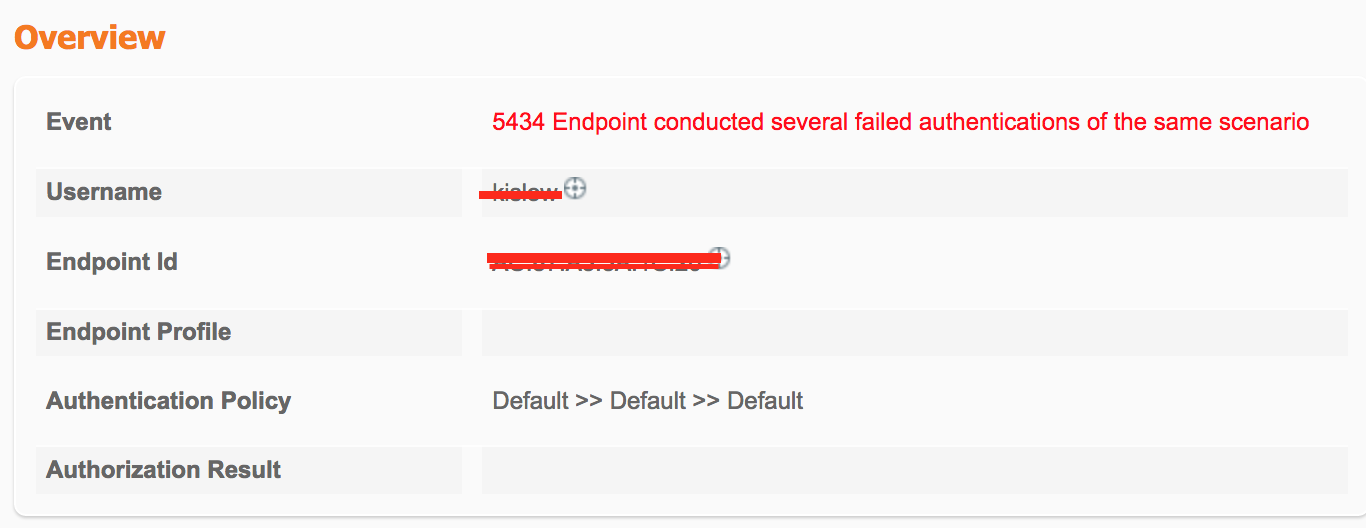
Question: How do I disable the default policy or how to ensure that my wired policy is always used for wired dot1x?
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-03-2017 06:28 AM
I suggest the following configuration :
- The SSP Access wired must have as condition: Network Access: Protocol EQUALS RADIUS
- Create a new compound condition like New_Created_Compound_Condition with: Network Access: EapAuthentication Equals EAP-TLS and Certificate: SibjectAlternativeName – DNS Contains your_domain_name
- In your Authentication Policy AD_Cert choose as condition (If): New_Created_Compound_Condition ==> Use AD_Cert_User
- I suppose that the Certificate Authentication Profile AD_Cert_User is configured like that: Identity Store: [Not applicable] and Certificate Attribute: Subject Alternative Name
Also:
Configure the Authorization Plicy like that: AthZ_Policy_Name if Any and
CERTIFICAT: Subject Alternative Name – DNS contains “your_domain”
Network Access: AuthenticationMethod Equals X509_PKI
RADIUS: NAS-Poirt-Type Equals ETHERNET
Then: Admin_Wired
I hope that will help.
Best regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-03-2017 05:27 AM
Hi Kadir
The Policy Sets in ISE are like the Service Selection Policy on ACS. The order is very important.
Please place you Policy Set "Access Wired" before the Default Policy Set.
Best regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-03-2017 05:41 AM
Hello Abdollah,
I have moved around the policy set from top to bottom...technically the "Access Wired" Policy set is at the very top, whereas the default policy set is at the bottom (not moveable anyway)...do you have another sugestions?
Kind regards,
Kadir
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-03-2017 05:47 AM
Hi Kadir
Please upload a screenshot of your Policy Sets on ISE. I can help based on what you have in your configuration.
Best regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-03-2017 05:51 AM
I hope this helps...let me know if required more...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-03-2017 06:28 AM
I suggest the following configuration :
- The SSP Access wired must have as condition: Network Access: Protocol EQUALS RADIUS
- Create a new compound condition like New_Created_Compound_Condition with: Network Access: EapAuthentication Equals EAP-TLS and Certificate: SibjectAlternativeName – DNS Contains your_domain_name
- In your Authentication Policy AD_Cert choose as condition (If): New_Created_Compound_Condition ==> Use AD_Cert_User
- I suppose that the Certificate Authentication Profile AD_Cert_User is configured like that: Identity Store: [Not applicable] and Certificate Attribute: Subject Alternative Name
Also:
Configure the Authorization Plicy like that: AthZ_Policy_Name if Any and
CERTIFICAT: Subject Alternative Name – DNS contains “your_domain”
Network Access: AuthenticationMethod Equals X509_PKI
RADIUS: NAS-Poirt-Type Equals ETHERNET
Then: Admin_Wired
I hope that will help.
Best regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-03-2017 06:46 AM
The Admin_Wired must be configured like that :
Access Type = ACCESS_ACCEPT
VLAN Tag ID 1 and Name: YOUR_VLAN_NAME
You can also enable the rethentication after 1h (as an example):
Reauthentication Timer: 3600
Maintain Connectivity During Reauthentication RADIUS-Request
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-03-2017 07:57 AM
This was the right answer!
Thank you, it now does work after creating a new Policy Set and by using some of your suggested method.
However after removing the (Device Type = Device Group Switches) and only setting it to Network Access = Radius & Nas-Port-Type = Ethernet...it started Running again!
Thanks you all for the professional help!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-03-2017 08:56 AM
Hi Kadir
I'm happy to know that you are able know to authenticate the users!
Best regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-03-2017 05:51 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-03-2017 06:05 AM
Hello Danny,
even when I add the Service-Type = Framed it uses the default policy...I have multiple Policy sets however it's only the "Access Wired" which is not being recognized for some reason...(see screenshot)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-03-2017 06:12 AM
I would remove radius attributes first and try to match based on your device type only, perhaps even narrow it down to a specific device your endpoint is hanging off of , keep it to a minimum and simple just to make sure you hit the policy set at first.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide
