- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: ISE Sonus device RADIUS integration
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-28-2018 05:41 AM
Hi All,
I am trying to integrate Sonus device with ISE. I have created profile in ISE with following attributes.
Access Type = ACCESS_ACCEPT
VendorSpecific = Vendor ID=2879
Sonus suggested that RADIUS Access-Accept packet should return the following:
RADIUS Protocol
Code: Access-Accept (2)
Packet identifier: 0x1 (1)
Length: 41
Authenticator: e5e3b89c308061b1237bf678be059cd1
[This is a response to a request in frame 1]
[Time from request: 0.000233000 seconds]
Attribute Value Pairs
AVP: t=Vendor-Specific(26) l=21 vnd=Sonus Networks, Inc.(2879)
Type: 26
Length: 21
Vendor ID: Sonus Networks, Inc. (2879)
VSA: t=Unknown-Attribute(1) l=15 val=41646d696e6973747261746f72
Type: 1
Length: 15
Unknown-Attribute: 41646d696e6973747261746f72
With above created profile I am getting error "15019 Could not find selected Authorization Profiles" as in attachment. How we can add above mentioned attributes in RADIUS response packet?
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-11-2019 03:03 AM
As far as I can see you have done everything correct. It smells like a bug to me. The issue is not with Sonus because ISE is not even getting as far as processing the Authorization Policy. The Attribute value=1 will be sent as a STRING - that all looks good to me.
I have seen a similar bug before in ISE 2.2 or 2.3 regarding TACACS policies - I was configuring Policy but ISE didn't seem to recognise it.
My IT help-desk answer would be: "Are you able to do an application ise stop/start?" ;-)
Failing that - delete the Authorization Policy and re-add it. That might re-program it.
If all else fails, TAC .... :-( - but either way, please let us know how you get on. This should not be tricky at all.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-09-2019 03:38 AM
@vaibhgupta157 - did you find an answer to this?
What does your Authorization Rule look like (can you screen capture it ?) - I am interested to see what you have defined as the Result Profile for that Rule. And then in another screenshot show the contents of that Results Profile please.
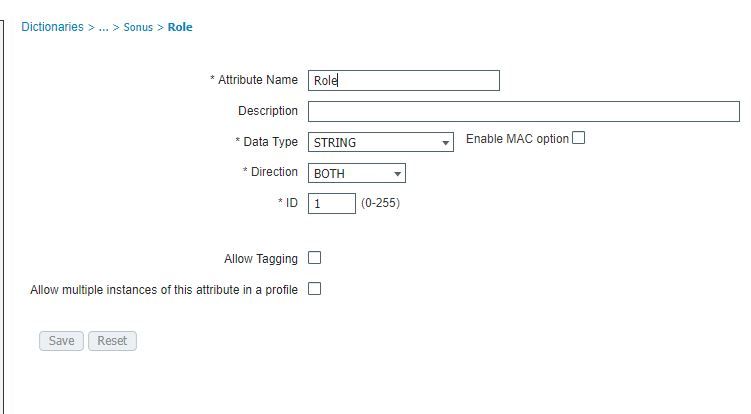
How did you define the VSA? I would imagine it looks something like what I have below?
One thing to remember is that when you add the Sonus NAS to ISE, you need to give it a Vendor type. What vendor type did you give it? If, e.g. you left the default of "Cisco" then that's fine, but then the Result Profile has to either also be of type "Cisco" or "blank".
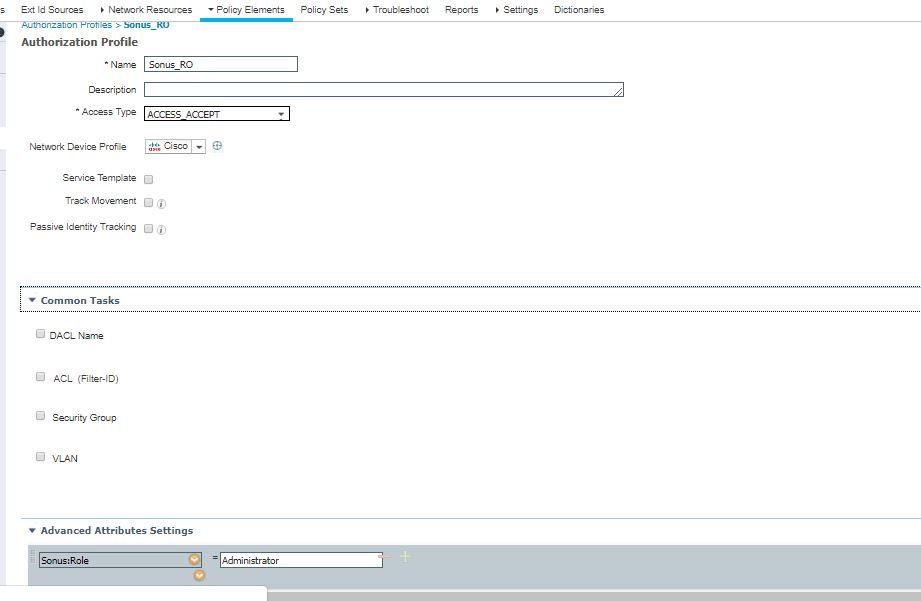
And then you would use a Result Profile like below in your Authorization Rule
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-11-2019 12:57 AM
Hi Arne,
Thanks for your response
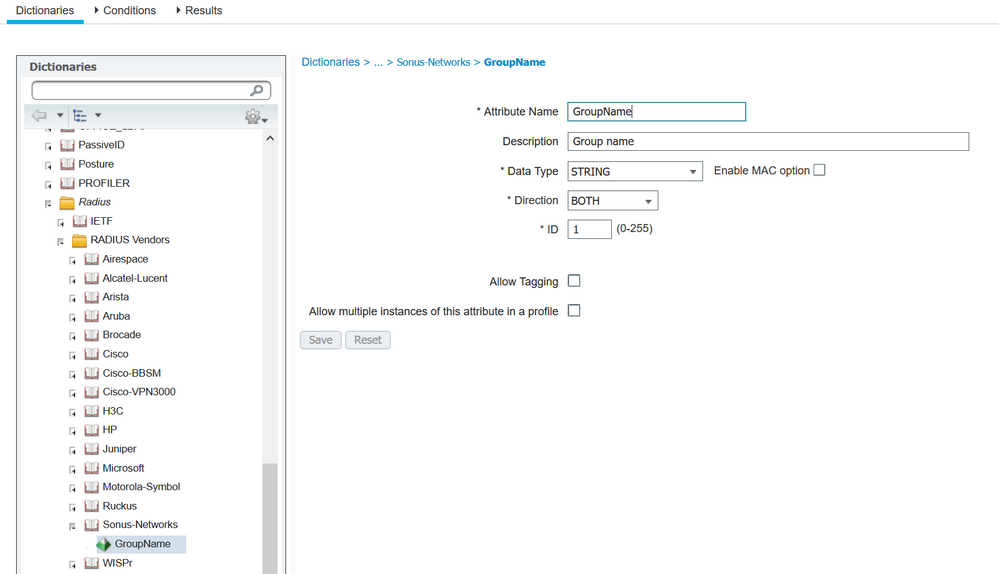
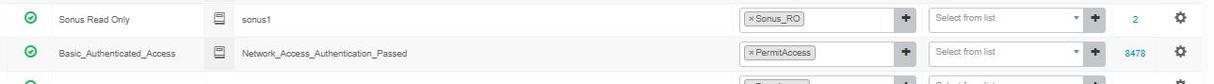
Please find the screenshot of Sonus dictionary attribute:
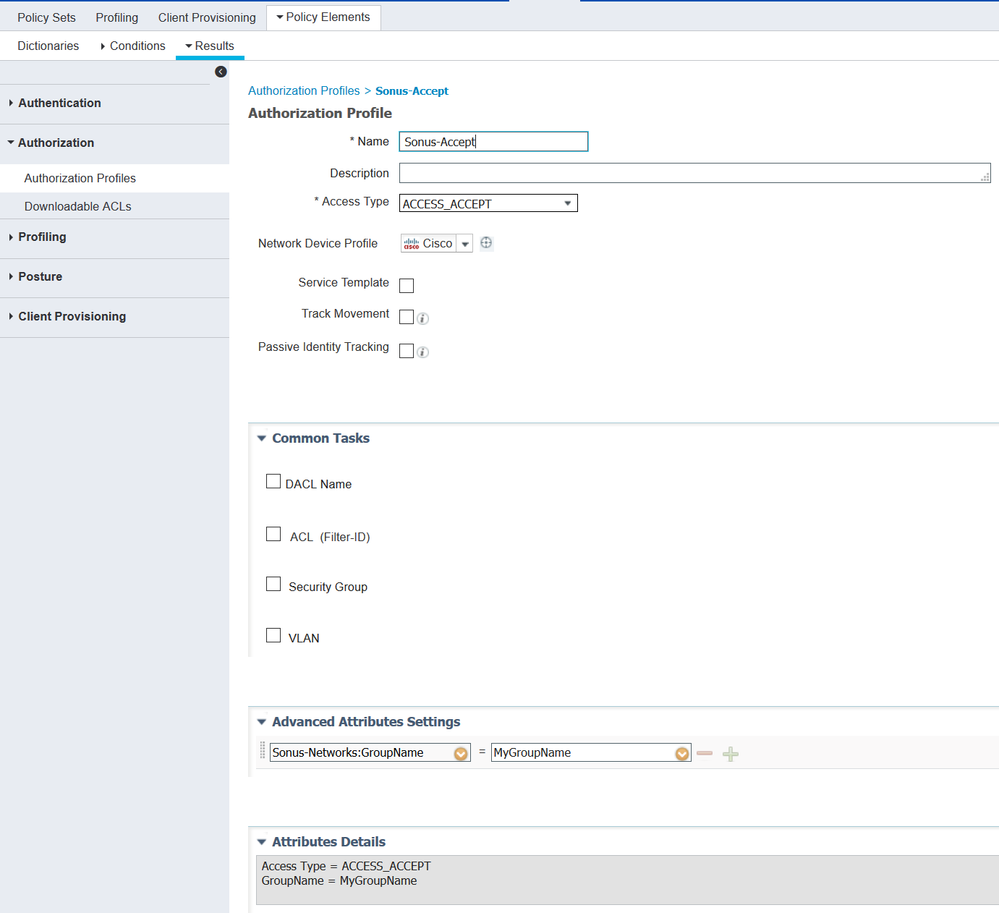
I have created following authorization profile
and the screenshot of authorization rule:
I added NAS with device profile "Cisco" and Result Profile is also "Cisco". But still it is failing
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-11-2019 01:15 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-11-2019 02:48 AM
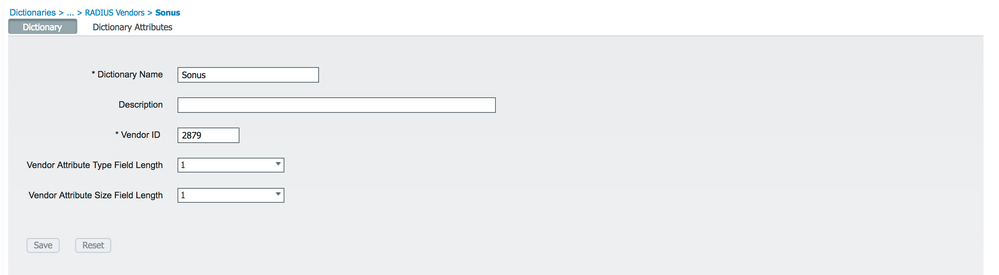
This is a custom dictionary.
Sonus document talks about radius attributes in following document under "Obtain Correct Privileges via RADIUS Transaction" section
As per Sonus TAC team,
ACCESS_ACCEPT response from ISE should carry following:
Code: Access-Accept (2)
Packet identifier: 0x1 (1)
Length: 41
Authenticator: e5e3b89c308061b1237bf678be059cd1
[This is a response to a request in frame 1]
[Time from request: 0.000233000 seconds]
Attribute Value Pairs
AVP: t=Vendor-Specific(26) l=21 vnd=Sonus Networks, Inc.(2879)
Type: 26
Length: 21
Vendor ID: Sonus Networks, Inc. (2879)
VSA: t=Unknown-Attribute(1) l=15 val=41646d696e6973747261746f72
Type: 1
Length: 15
Unknown-Attribute: 41646d696e6973747261746f72
There is no mention of VSA which should carry group information. Also I tried with Vendor Specific attribute[26] specified in RFC 2865 but ISE responds with ACCESS_REJECT
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-11-2019 03:26 AM
[cid:image001.png@01D4A9CE.5EC23510]
[cid:image002.png@01D4A9CE.5EC23510]
[cid:image003.png@01D4A9CE.5EC23510]
[cid:image004.png@01D4A9CE.5EC23510]
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-11-2019 04:01 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-11-2019 03:03 AM
As far as I can see you have done everything correct. It smells like a bug to me. The issue is not with Sonus because ISE is not even getting as far as processing the Authorization Policy. The Attribute value=1 will be sent as a STRING - that all looks good to me.
I have seen a similar bug before in ISE 2.2 or 2.3 regarding TACACS policies - I was configuring Policy but ISE didn't seem to recognise it.
My IT help-desk answer would be: "Are you able to do an application ise stop/start?" ;-)
Failing that - delete the Authorization Policy and re-add it. That might re-program it.
If all else fails, TAC .... :-( - but either way, please let us know how you get on. This should not be tricky at all.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
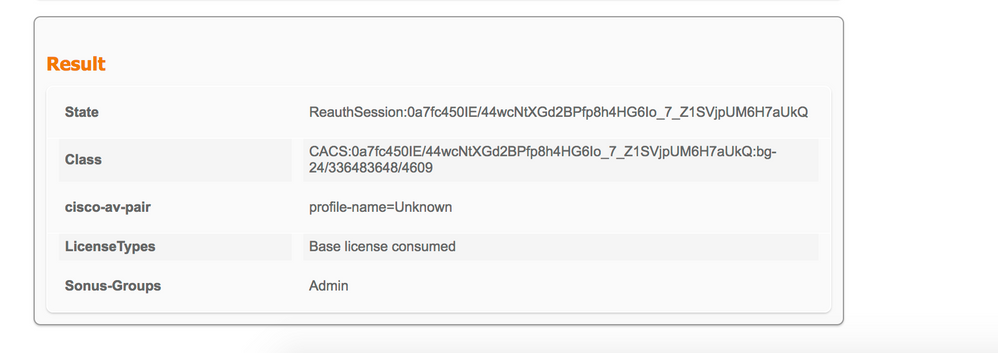
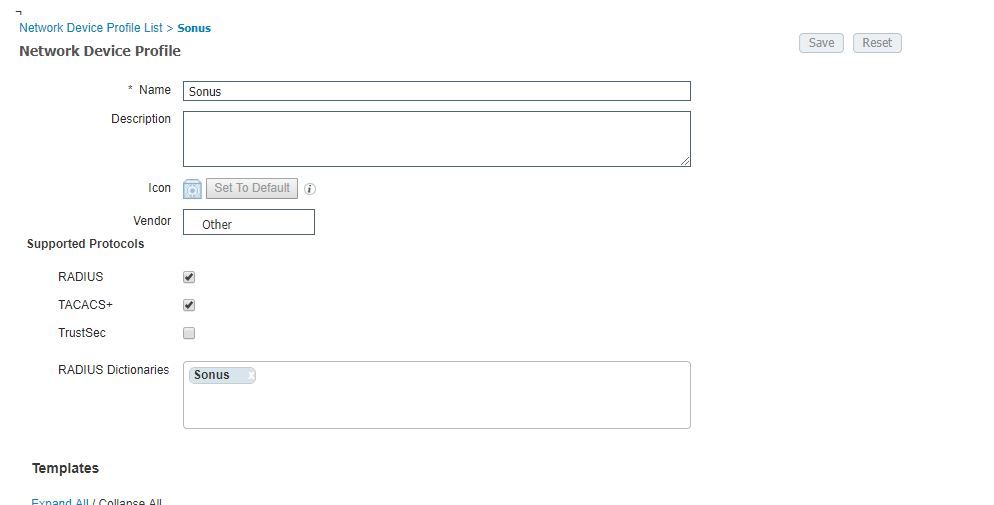
01-25-2019 02:09 AM
Hi All,
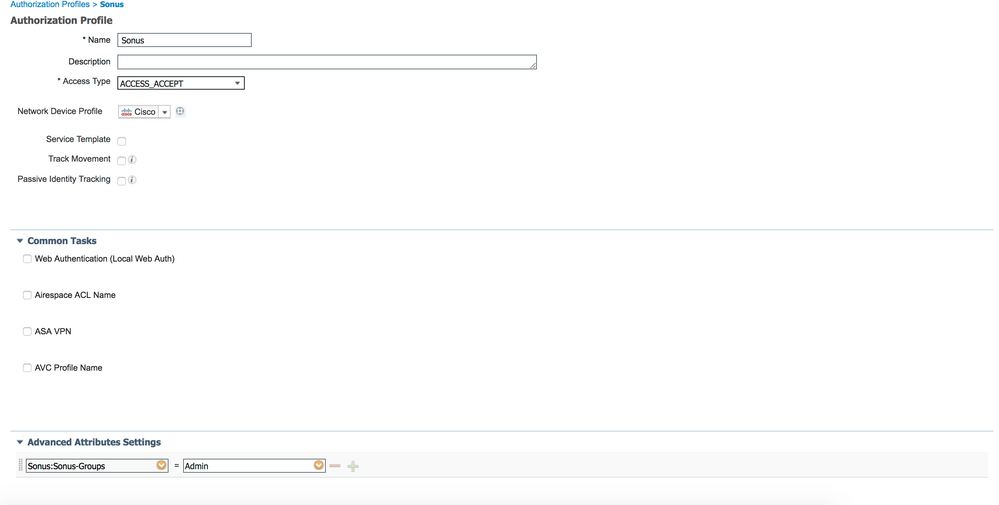
We got it working...
TAC Engineer created a separate Network Device Profile.
Assigned this profile in device instead of Cisco
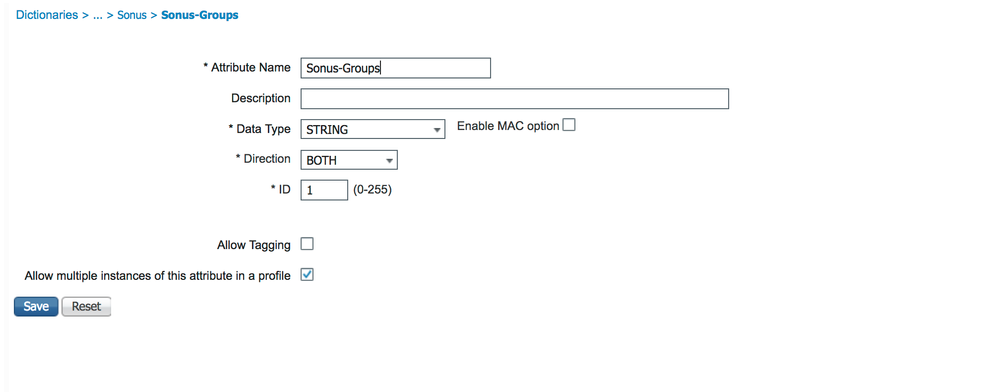
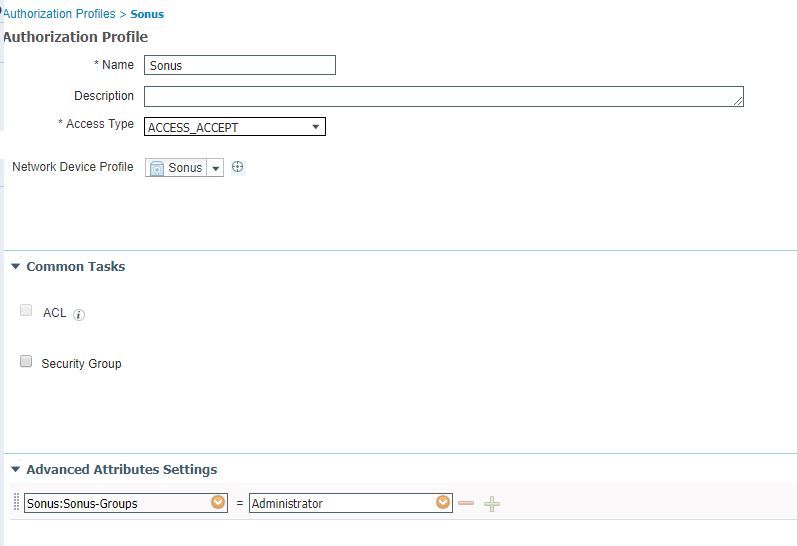
Authorization Profile is created with attribute "Sonus-Groups":
Thanks all.....
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide