- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: ISE tacacs+ in distributed environment
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-17-2018 02:53 AM - edited 02-21-2020 10:53 AM
Hi All,
I want to have a distributed deployment of ISE using two physical server with one Device Administration license. I am going to load balance TACACS+ and RADIUS requests between primary and secondary ISE nodes by configuring half of the devices to primary and half to secondary.
Can someone confirm whether secondary ISE can also respond to TACACS+ requests with same license?
Solved! Go to Solution.
- Labels:
-
Other NAC
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-17-2018 03:44 AM
The concept of Primary and Secondary applies to Administration and Monitoring personas, not to the Policy services persona, which will actually be the one that responds to the RADIUS and TACACS requests.
The Policy Services personas do not use any kind of primary/secondary style failover. If one goes offline, it is up to the network device to detect the failure and switch to using different ISE node.
The Device Administration licence is per deployment, so yes, all nodes with Policy Service persona enabled will serve TACACS requests, if configured to do so.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-17-2018 03:44 AM
The concept of Primary and Secondary applies to Administration and Monitoring personas, not to the Policy services persona, which will actually be the one that responds to the RADIUS and TACACS requests.
The Policy Services personas do not use any kind of primary/secondary style failover. If one goes offline, it is up to the network device to detect the failure and switch to using different ISE node.
The Device Administration licence is per deployment, so yes, all nodes with Policy Service persona enabled will serve TACACS requests, if configured to do so.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-14-2020 12:21 PM
I am self-admittedly not an ISE expert so with that, I have a question about AAA authentication. Currently all of our switches and network equipment are pointing to tacacs server ISE-PRIMARY which is our Primary Monitoring Node. From what I understand, the "Monitoring Node" doesn't provide TACACS authentication services. Just wondering how this is working but it indeed does. My goal is to point AAA authentication for my network devices to our local Policy Services Node. Any help would be appreciated.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-15-2020 09:01 AM
TACACS is just a persona that can be enabled on any ISE node. All roles can run on any node, but that's not necessarily aligned with best practices. It comes down to how the deployment was designed, standalone, hybrid, or distributed.
If you only have two nodes then you are running a standalone deployment and it is ok to have device admin running with the mnts.
If you navigate to this page, you can enable/disable personas, you will also see DEVICE ADMIN listed in the services column. DEVICE ADMIN indicates that node has tacacs enabled.
https://<ise primary ip>/admin/#administration/administration_system/administration_system_deployment
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-17-2018 07:58 AM
Based on my understanding, you need a different license for TACACS on ISE. In fact, I would suggest you ISE 2.3 for TACACS services because there are some details supported on this version and NOT the previous ones.
Important to mention that you can assign 2 entries (serial number) to the same license so in case that primary pan fails the secondary can be promoted and no issues with the licensing part would happen. I mean, the license would have the serial number attached of Primary and Secondary PAN.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
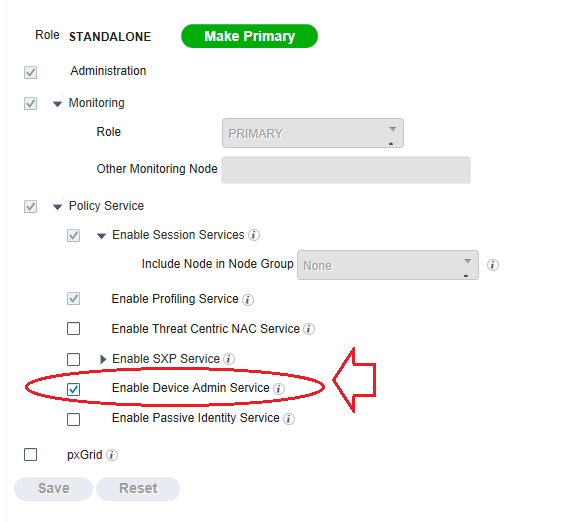
04-17-2018 08:02 AM
One more detail. To enable TACACS on ISE , check the following box.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide