- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: ISE2.6 is able to reject any unauthorized access when after boot ?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-29-2022 02:05 AM
HI !
We use the ISE2.6 for MAC authentication. It has two ISE server with HA as active standby. If both server shutdown when the ISE not work for MAC authentication. All client is able to access any access point (AP) after ISE server shutdown. Could the ISE2.6 is able to reject any unauthorized access when after the ISE boot again?
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-03-2022 01:25 AM
Any existent session that has already passed the authentication and the authorization will not be affected when ISE nodes go down, until the sessions expire. When those sessions expire and try to reauthenticate they will be rejected. Same will happen for any new session.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-29-2022 09:44 AM
The connection to the APs themselves doesn't necessarily mean accessing to the network. If you don't have the critical VLAN configured as a fall back, the clients should be denied access to the network when both ISE nodes are down. This is because in that case, there will be no returned attributes to allow the clients any access.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-29-2022 04:57 PM
Thank you for your support.
We are able to access to AP when the ISE both go to down. This is the current ISE specification we have.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-30-2022 04:23 AM
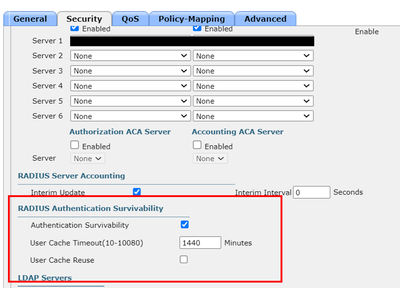
Do you have RADIUS Authentication Survivability enabled on your WLC to allow clients to authenticate when ISE is unavailable? - see below.
Might be worth re-posting on the wireless forum to see if it is possible for WLC to reauthenticate clients if there is an AAA available event
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-30-2022 10:30 PM
Thank you for your answer.
I do not know about RADIUS Authentication Survivability settings. Because I have not any ID to access to WLC. However I know that any client is able to access to AP when both ISE server go to down. So I think may be RADIUS Authentication Survivability setting enabled on our WLC.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-30-2022 01:42 AM
When ISE nodes are down, the WLC wouldn't be able to contact/receive any reply back from ISE, so the clients should be denied accesses to any SSID that is reliant on ISE. Could you please elaborate a bit more of the current setup and what you are trying to achieve?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-30-2022 10:49 PM
Thank you for your response.
I would like to migrate ISE on VMware virtual machine to new VMware infrastracture. Also I use Cold v-motion to magarate ISE on VMware virtual machine. I have to shutdown ISE before maigration. However alrady any client use AP via ISE RADIUS Authentication. I heard that if both ISE go to down when any AP do not reject all client. In other word, all client is able to access to any AP. I will allow someone to continue to have access to the AP during the ISE migration time. However, we cannot allow unauthenticated client connections after the migration is complete. For this reason, I want to disconnect only connections from unauthenticated clients.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-03-2022 01:25 AM
Any existent session that has already passed the authentication and the authorization will not be affected when ISE nodes go down, until the sessions expire. When those sessions expire and try to reauthenticate they will be rejected. Same will happen for any new session.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-03-2022 02:03 AM
Thank you for your good answer.
I think that your answer is best.
I do not know that ISE command for sessions expire. Please tell me ISE command as check setting for sessions expire time if you can do that.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-04-2022 01:12 AM
You are welcome sir. There is no command on ISE that I'm aware of that would show you the endpoints/clients reauthentication timers because the timer does not set on ISE itself, however, it does set on the network device, whether a switch, firewall, access point etc. From ISE perspective you can set the reauthentication timer, as well as the idle timer, from within the authorization profiles. If I remember correctly the attributes names are "Reauthentication" in the common tasks list, and "Idle-Timeout" in the RADIUS advanced attributes menu.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide