- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: PC Imaging on NAC secured ports
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-06-2018 11:46 AM
We are in the process of deploying 802.1x/MAB port security in our organization using ISE. Our client computing group has given us the requirement of being able to image/re-image workstations from the users desks in a self-service model. This would be initiated in one of three methods; one using a USB thumb drive with Windows PE on it, two using a hidden Windows PE partition on the PC, or three using PXE Boot to get the Windows PE image. The Windows PE image will then need to contact the designated SCCM server (over 200 company wide) to pull down the new image and at the end of the process it will join the domain. I am trying to figure out how to develop an ISE policy to allow this process to work as it does today without being wide open. Any help and suggestions on this would be greatly appreciated.
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-06-2018 04:26 PM
Hi Craig,
This is typically one of the most difficult things to provide in an ISE/802.1x environment, especially when you move from a Monitor Mode phase to Low Impact or Closed Mode.
At a high level, the typical options are as follows:
- Provide a separate build area that does not have NAC enabled but requires physical security to access.
- Develop a process for users to contact IT to be moved into a temporary state that will allow the necessary network access for a build. This can be done either manually by an ISE admin or via development of a tool to leverage the ISE API.
- Provide a ‘Build’ portal that users can access via another corporate system. Users would be required to login to the portal (hosted on ISE) and enter their MAC address prior to attempting build/rebuild. Either the User or Admin would later remove the endpoint from this group after the build completes (or try to leverage the endpoint purge policy in ISE).
- Modify the current build process to leverage scripts that will enable the Windows 802.1x supplicant early in the build (prior to domain join) and use a pre-defined username/password (PEAP-MSCHAPv2) to authenticate. This would require development changes in SCCM.
- Open the Pre-Auth ACL to allow all traffic required for a build/rebuild. This would include access to the AD domain, build TFTP servers, and any other 3rd party systems accessed during the build process. The size of this ACL could have adverse impacts on the switch TCAM.
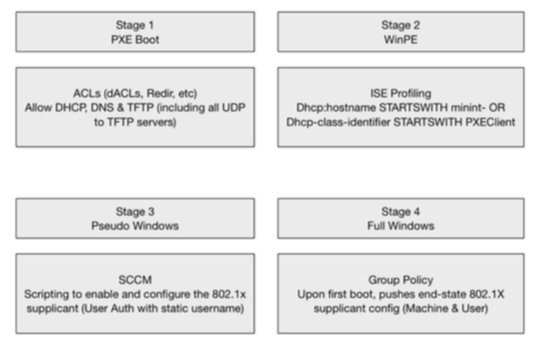
Option 4 is a process I developed and tested with a customer's SCCM team and provides the most dynamic option I've encountered. The process flow is illustrated below.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-06-2018 04:26 PM
Hi Craig,
This is typically one of the most difficult things to provide in an ISE/802.1x environment, especially when you move from a Monitor Mode phase to Low Impact or Closed Mode.
At a high level, the typical options are as follows:
- Provide a separate build area that does not have NAC enabled but requires physical security to access.
- Develop a process for users to contact IT to be moved into a temporary state that will allow the necessary network access for a build. This can be done either manually by an ISE admin or via development of a tool to leverage the ISE API.
- Provide a ‘Build’ portal that users can access via another corporate system. Users would be required to login to the portal (hosted on ISE) and enter their MAC address prior to attempting build/rebuild. Either the User or Admin would later remove the endpoint from this group after the build completes (or try to leverage the endpoint purge policy in ISE).
- Modify the current build process to leverage scripts that will enable the Windows 802.1x supplicant early in the build (prior to domain join) and use a pre-defined username/password (PEAP-MSCHAPv2) to authenticate. This would require development changes in SCCM.
- Open the Pre-Auth ACL to allow all traffic required for a build/rebuild. This would include access to the AD domain, build TFTP servers, and any other 3rd party systems accessed during the build process. The size of this ACL could have adverse impacts on the switch TCAM.
Option 4 is a process I developed and tested with a customer's SCCM team and provides the most dynamic option I've encountered. The process flow is illustrated below.

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-07-2018 02:46 AM
hi grgibbs
the option4 you are describing seems really interresting
from what i understand :
- in stage 3 you are using something like a unique authentication credential (PEAP with specific account, or perhaps a specific default certificate in eap-tls),
- and in stage 4 them after AD domain joining, AD GPO are pushing 802.1x typical config (machine+user), and if eap-tls is beeing used perhaps GPO will auto-enroll certificates ?
Is this the correct understanding ?
Thanks for this usefull tip !
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-07-2018 12:30 PM
Correct Guillaume.
Stage 3 is when the PC initially boots out of the WinPE image, starts enumerating devices, and loads drivers. There's not really any network access needed at this point until the PC needs to join the domain.
The customer inserted new steps in SCCM that copy the scripts needed to configure the supplicant for PEAP-MSCHAPv2 with a static username/password (e.g. username 'pcbuild' password 'password123') during the WinPE stage and execute the scripts before the domain join step in Stage 3. We looked at using certificates and EAP-TLS, but we would have to pass both the cert and the private key to the PC, so we felt it wasn't any more secure and more complex than using PEAP. You can authenticate this user either against an AD service account or an internal ISE network user account.
At the initial boot into Full Windows (Stage 4), the GPO push happens before the user first logs in, at which point the end-state supplicant configuration can be pushed (including pushing a machine cert and EAP-TLS config if needed).
Hope this helps,
Greg
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-12-2018 07:52 AM
Hi grgibbs,
Thanks for the response. I had looked into option 4 and recommended it to our client computing group. They came back and said that adding 802.1x support to the Windows PE image wasn't supported by Microsoft. Did you run into this issue?
Thanks,
Craig
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-12-2018 01:32 PM
Hi Craig,
Yes, I've heard from other customers that MS does not support the customisation needed in SCCM to spin-up 802.1x during the build process. To me, this sounds like a typical response from MS when there is mention of doing anything custom. They don't want to be on the hook to support something they didn't develop, which is understandable. This should not mean, however, that they won't support the build process at all if you add one or more custom steps. You simply might have to disable/remove those custom steps if you need to seek support from MS in the future.
Since MS have yet to provide a better solution (this has been a problem for many years now), the customer I worked with decided to move forward with this solution anyway.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-12-2018 04:02 PM
I found this online circa 2010-2012.
I'm not a windows admin so not sure if it works.
Westminster's NetMan: SCCM, WinPE and 802.1x
http://wgsnetman.blogspot.co.uk/2010/06/sccm-winpe-and-8021x-directors-cut.html
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-01-2019 04:06 PM
Hi @Greg Gibbs
I just want to get some more details on how option 3 works (Provide a ‘Build’ portal)? Is this using the mydevices portal to register the endpoint mac address? We are already using BYOD, so how can we differentiate between the byod machines and the machines needing re-imaging?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-01-2019 04:55 PM
Yes, this would be using the same My Devices portal flow but with a different portal. In newer versions of ISE (at least 2.2+), you can create more than one My Devices Portal. These portals can each be configured with a different 'friendly' FQDN (i.e. mydevices.corp.com vs. build.corp.com), different Endpoint ID Group, Authentication method, etc.
You might need to test this first, however, to ensure if a user with a BYOD endpoint and Build endpoint sees each endpoint only in the relevant portal.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-01-2019 08:14 PM - edited 04-04-2019 05:26 PM
Thanks I'll test it out.
Im trying to determine whats the easiest option to have PC imaging without manual intervention. Option 4 - making changes to SCCM seems a bit too complicated for us.
What about option 3 - but using API to automatically add the machine's MAC address to an endpoint group then using a MAB policy to allow access for rebuilding for that endpoint group? Doing via portal will be cumbersome when 30-50 devices need to be rebuilt in bulk. Would this work?
Option 5 - we can add the tftp to pre-auth ACL, but customer is not willing to allow access to AD, which will be open to anyone. And we need to access AD towards the end of the build processes to get the machine onto the domain, get certs etc.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide



