- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: Purge endpoints based on blank status?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Purge endpoints based on blank status?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-07-2023 12:03 PM
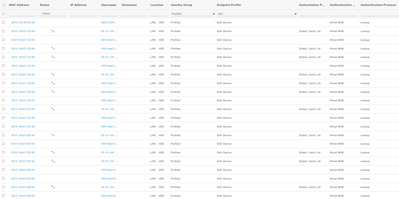
As you can see by the image below (just a subset), I am getting a lot of endpoints show up that appear to never actually hit one of my rules. It will sit like this until it hits the inactiveDays endpoint purge or I purge manually. Does anyone know a way to either purge these more quickly, or deny them from getting into the database altogether?
- Labels:
-
Identity Services Engine (ISE)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-09-2023 08:06 AM
@Josh Morris Please drill into a few of such client endpoints and see how they are learned (i.e. which probe(s) used as the source(s)).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-10-2023 07:12 AM
Most are Radius. I did have the pxGrid profiler enabled and was getting a lot of blank endpoints from that but have since disabled the profiler.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-09-2023 09:41 AM
The information you are displaying is from the context visibility, this information is purged regularly depending upon the rules you have configured in Administration>Identity Management> Settings> Endpoint Purge , see example below , when an endpoint attempts to log in your network with base on attributes this is going to be classified accordingly , if you have identified a group of endpoints what you can do is to set a rule that make the purge quicker, for your reference https://www.cisco.com/c/en/us/support/docs/security/identity-services-engine/215931-ise-guest-account-management.html
Let me know if that helped you .
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-10-2023 07:14 AM
Thanks. I am using quite a few Endpoint Purge rules. The problem here is that there aren't enough attributes to do much with these. I can't get them profiled to a group in order to use in a purge rule. I also am unwilling to create a default purge rule based on Elapsed or Inactive Days because there are many endpoints that would hit that rule that I don't want to purge.
What I'm really hoping is that ISE has a mechanism to purge endpoints when the attributes are blank.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-12-2023 08:35 PM
In addition to what it has been said here, once you checked the livelogs of such endpoints you can elaborate a rule based on the characteristics of those using the attributes option that is available in the endpoint purge page.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-11-2023 02:13 PM
@Josh Morris We are trying understanding how these endpoints got in as Internal Endpoints. Many of them seem gone through authentication only but not authorization. Please check the auth detail reports for some of such endpoints.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-15-2023 07:43 AM
@hslai I think there are two cases here. The first is that an endpoint connects to a switch, and does just enough to get an endpoint created in the context visibility but doesn't go through the full AAA process, as seen with the endpoint details below. This is my main concern. These are the types of situations I'm trying to prevent.
Then, there is the following situation, where the endpoint seems to go through the AAA process, and get matched to an authorization rule.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide