- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Suppressing wrong password attempts during wireless BYOD via CWA
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Suppressing wrong password attempts during wireless BYOD via CWA
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-15-2023 09:26 AM
Hello!
We're using BYOD via CWA (setup on ISE) in our wireless network so that users could self-register and issue/download a certificate profile. The normal scenario looks like this: user connects to an ssid, gets a redirect to guest web portal, enters his domain credentials and then follows the BYOD flow, in the end he gets his certificate profile and installs it on its phone. Since our domain controller has a policy of blocking account after 5 consecutive wrong password attempts we set up CWA portal to 3 attempts until rate limiting.
And it works totally fine while user using the same session. But apparently there is a way to bypass that limitation: after 1-2 login attempts a user can reopen the browser, get a redirect to the login page again and try another 2 times of logging in and so on. We've tried it, and after the 5th attempt the testing account was blocked.
We haven't really seen anyone doing it, but there is a possibility of cases like that, or some attackers who would try to block some employees domain accounts.
So, I'm trying to find a way to suppress/block users who tries to login via guest portal using wrong password. We're using ISE 2.7, maybe new versions of ISE have settings we need.
- Labels:
-
ISE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-15-2023 12:52 PM
Are you sure these are Guest splash page logins? Or are they PEAP logins from RADIUS from an SSID?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-15-2023 11:34 PM
I'm pretty sure it's a guest splash, since I set it up. We're using Guest flow + BYOD and it's set up in Work centers -> Guest Access -> Portal & Components -> Sponsored Guest Portal
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-16-2023 04:53 AM - edited 02-16-2023 04:54 AM
There is already an enhancement filed for this issue on ISE 3.0 version:
https://bst.cloudapps.cisco.com/bugsearch/bug/CSCwc56883
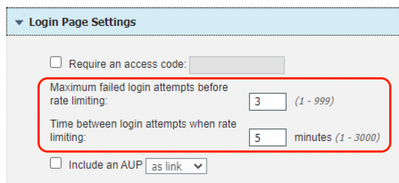
The ISE guest portal provides the following feature: > Maximum Failed Login Attempts Before Rate Limiting: Specify the number of failed login attempts from a single browser session before Cisco ISE starts to throttle that account. This does not cause an account lockout. The throttled rate is configured in Time between login attempts when rate limiting.
This enhancement request is filed to improve this feature to not bind the limit to one session. The reason is, that the limit can be easily bypassed when replacing the session cookies (portalSessionId / APPSESSIONID / token) for each request.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-29-2023 01:40 AM - edited 05-29-2023 01:41 AM
Hello everyone!
Does anyone know if there is a fix/workaround released for that problem?
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide