- Cisco Community
- Technology and Support
- Security
- Network Access Control
- TACACS Authentication and Fortigate Appliances
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
TACACS Authentication and Fortigate Appliances
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-04-2013 03:16 PM - edited 03-10-2019 08:37 PM
I have been trying to get TACACS authentication setup for my Fortigate webfilters and analyzers however I am missing the attributes to set the match conditions for the users who log in with the AD credentials to assign them the correct user profile type. I was wondering if anyone has a complete guide on how to do this. Thanks for your help.
- Labels:
-
AAA
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-04-2013 06:40 AM
What exactly is the problem? The AV configuration looks correct (make sure you have the Netsec group created in FortiNet).
Did following the link in the very first post? http://kb.fortinet.com/kb/microsites/microsite.do?cmd=displayKC&externalId=FD33320
You need to make sure you have a group and user created with all the same settings as shown in the link. Compare your configuration output against theirs. One thing to make sure of is to have the "set accprofile-ovride enable" on the user.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-05-2013 04:46 AM
Hi,
Thanks for your help upto now.
The issue I am having is I get an error message in the Fortigate logs saying invlaid password.
I have checked this username and password with other equipment we have and it works well.
Please find below the configuration of the Fortigate I currently have in place. The ACS configuration is in the above thread.
config system accprofile
edit "prof_admin"
set admingrp read-write
set authgrp read-write
set endpoint-control-grp read-write
set fwgrp read-write
set loggrp read-write
set mntgrp read-write
set netgrp read-write
set routegrp read-write
set sysgrp read-write
set updategrp read-write
set utmgrp read-write
set vpngrp read-write
set wanoptgrp read-write
set wifi read-write
next
edit "MGT"
set admingrp read-write
set authgrp read-write
set endpoint-control-grp read-write
set fwgrp read-write
set loggrp read-write
set mntgrp read-write
set netgrp read-write
set routegrp read-write
set sysgrp read-write
set updategrp read-write
set utmgrp read-write
set vpngrp read-write
set wanoptgrp read-write
set wifi read-write
next
edit "NOACCESS"
next
end
config system admin
edit "admin"
set trusthost3
set accprofile "super_admin"
set vdom "root"
config dashboard-tabs
edit 1
set name "Status"
next
edit 2
set columns 1
set name "Top Sources"
next
edit 3
set columns 1
set name "Top Destinations"
next
edit 4
set columns 1
set name "Top Applications"
next
edit 5
set columns 1
set name "Traffic History"
next
edit 6
set columns 1
set name "Threat History"
next
end
config dashboard
edit 1
set tab-id 1
set column 1
next
edit 2
set widget-type licinfo
set tab-id 1
set column 1
next
edit 3
set widget-type jsconsole
set tab-id 1
set column 1
next
edit 4
set widget-type sysres
set tab-id 1
set column 2
next
edit 5
set widget-type gui-features
set tab-id 1
set column 2
next
edit 6
set widget-type alert
set tab-id 1
set column 2
set top-n 10
next
edit 21
set widget-type sessions
set tab-id 2
set column 1
set top-n 50
set sort-by msg-counts
next
edit 31
set widget-type sessions
set tab-id 3
set column 1
set top-n 25
set sort-by msg-counts
set report-by destination
next
edit 41
set widget-type sessions
set tab-id 4
set column 1
set top-n 25
set sort-by msg-counts
set report-by application
next
edit 51
set widget-type sessions-bandwidth
set tab-id 5
set column 1
next
end
config login-time
edit "admin"
set last-failed-login 2013-09-03 04:08:27
set last-login 2013-09-05 04:36:27
next
end
set password ENC AK1O4Q8273vSAUyUkC4t4GOkSb40llfIAUEnr4uqWDgBX8=
end
edit "jackw"
set remote-auth enable
set trusthost1
set accprofile "NOACCESS"
set vdom "MGT"
config login-time
edit "jackw"
set last-failed-login 2013-09-04 08:10:41
next
edit "jackw@888holdings.com"
set last-failed-login 2013-09-04 07:53:30
next
end
set wildcard enable
set remote-group "Netsec"
set accprofile-override enable
next
end
config user tacacs+
edit "tacacs+"
set authorization enable
set key ENC jTbeQPV44emKUByXuHAQdY3CoxYY3/9MoFsuW4YAiC88JiSJmd3yrFv7VMyrGVUJK6Fv3DzcL9VMetGJ60I332W5cLP53jpYSHJnkJB0B5aKffK7mdC+PBU/HcmyogEWACOO9my9fxG85AFqKdRj6VUirtmluw4WR0GTkdtCbXK4zE8JHC+iYx5ALicUK/G/tWbc/g==
set server "192.118.67.39"
next
end
config user group
edit "Netsec"
set member "tacacs+"
config match
edit 1
set server-name "tacacs+"
set group-name "Netsec"
next
end
next
end
config user local
edit "jackw"
set type tacacs+
set email-to ""
set tacacs+-server "tacacs+"
next
end
Thanks again.
Jack.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-05-2013 06:47 AM
Here is a couple of things that I noticed:
1. The NOACCESS accprofile should have some output similiar to (set admingrp none, set authgrp none....)
2. I have my user group-type set to firewall
config user group
edit "Netsec"
set group-type firewall
set authtimeout 0
set http-digest-realm ''
set sslvpn-portal ''
set member "tacacs+"
next
end
3. The tacacs+ configuration should have a source-ip, otherwise, the ACS server can't match it to it's AAA client
Other things to note, be sure to add the Fortinet as a AAA client and make sure the key matches. Check the logs on both the ACS server and the Fortinet side. The Fortinet side should not determine that the password is incorrect, it should be the ACS server's job. Everything else looks right so make those changes and check the ACS log.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-15-2014 05:38 AM
Hi chheangva,
As you said I created two shell profiles in ACS , one for RO and other for RW.
On the Fortinet side, I created an Admin user (ie, "test") that is setup for Remote login, Wildcard, and a profile of NOACCESS.
but they are not overriding the noaccess setting. Please help
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-26-2014 06:01 AM
The configuration isn't correct, in the field "Custom attributes" you have to set the following values:
memberof=<tacacs+-group>
admin_prof=<Req. profile>
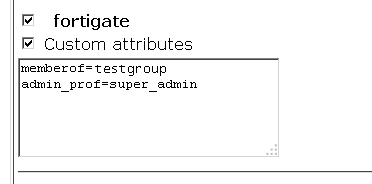
For further details read the KB from Fortinet.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-26-2014 06:19 AM
Hi Erik,
In the custom attributes all required values mentioned. But always users getting no_access profile.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-26-2014 07:19 AM
Then you dont have the override function set in the admin user configuration.
Please attach your user configuration (on fortigate) for review.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-29-2014 12:58 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-12-2014 11:29 PM
Config seems to be okay, check your config on the TACACS+ Server, maybe is there something wrong.
You can debug the logon on Fortigate with "diag debug app fnbadm -1".
Try to use the newer Version of FortiOS, Version 4 isn't anymore supported since April 2014.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-04-2015 02:50 PM
I have been able to do this for my fortigates, but I haven't been able to find the correct attributes and values for FortiManager and FortiAnalyzer. Anybody know them?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-05-2015 12:00 AM
service=fortigate
memberof=<tacacs-serverbzw gruppe>
admin_prof=<access profil>
adom=<adom>
I got it with analyzing the communication between Manager and ACS server.
Sniffing the packets and then import it in wireshark for analyzing.
The attributes for the manager and the analyzer are the same.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-09-2013 11:49 PM
Hi
Please go through this link, this will be helpful regarding TCSACS Authentication and Fortigate configuration:
- « Previous
-
- 1
- 2
- Next »
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide