- Cisco Community
- Technology and Support
- Security
- Network Access Control
- TACACS two factor authentication with DUO
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-10-2019 11:53 AM
Hi folks,
I haven't worked much on multi factor authentication on ISE. So it would be great if I get more details on this, The customer needs the below design to support from ISE, is it possible? So basically they want to do TACACS auth for the below devices where the authentication request should go to AD and then once successful it should go to DUO server for phonecall or token? Is there any configuration example which helps the scenerio
List of network devices we will use for testing:
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-10-2019 01:09 PM
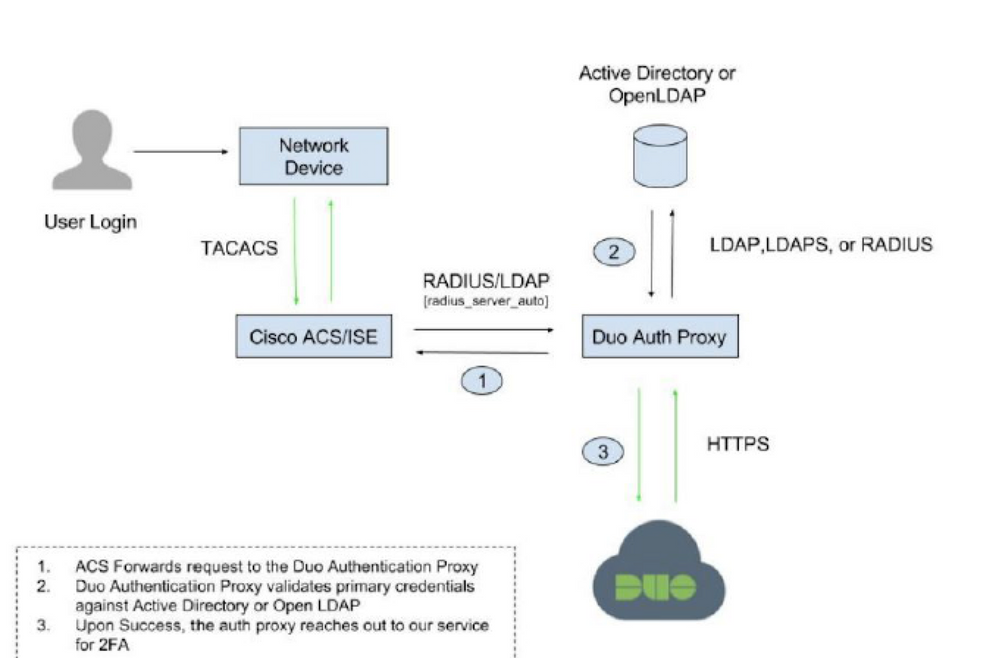
Configure authentication to be done against ISE (Configure ISE to look for the user in AD) and authorization to be done against DUO.
This will work as long as the network device supports different servers for authentication and authorization.
ISE in itself does not support MFA but utilizes the third party device capability to do so. TACACS has a very limited scope when it some to MFA on ISE. For instance : https://community.cisco.com/t5/security-documents/using-duo-with-ise-2-3-and-acs-5-x-for-2fa-cisco-network-admin/ta-p/3642171
If you plan to use RADIUS, then you can probably try this https://www.cisco.com/c/en/us/support/docs/security/identity-services-engine/213239-configure-external-radius-servers-on-ise.html#anc7 . Here you can check with DUO call or OTP first and then lookup the user in the AD in authorization policies if you choose the option to continue with authorization on Access-Accept.
You cannot do the other way around with ISE with either of the protocols i.e., AD first and then DUO.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-10-2019 01:09 PM
Configure authentication to be done against ISE (Configure ISE to look for the user in AD) and authorization to be done against DUO.
This will work as long as the network device supports different servers for authentication and authorization.
ISE in itself does not support MFA but utilizes the third party device capability to do so. TACACS has a very limited scope when it some to MFA on ISE. For instance : https://community.cisco.com/t5/security-documents/using-duo-with-ise-2-3-and-acs-5-x-for-2fa-cisco-network-admin/ta-p/3642171
If you plan to use RADIUS, then you can probably try this https://www.cisco.com/c/en/us/support/docs/security/identity-services-engine/213239-configure-external-radius-servers-on-ise.html#anc7 . Here you can check with DUO call or OTP first and then lookup the user in the AD in authorization policies if you choose the option to continue with authorization on Access-Accept.
You cannot do the other way around with ISE with either of the protocols i.e., AD first and then DUO.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-10-2019 06:50 PM
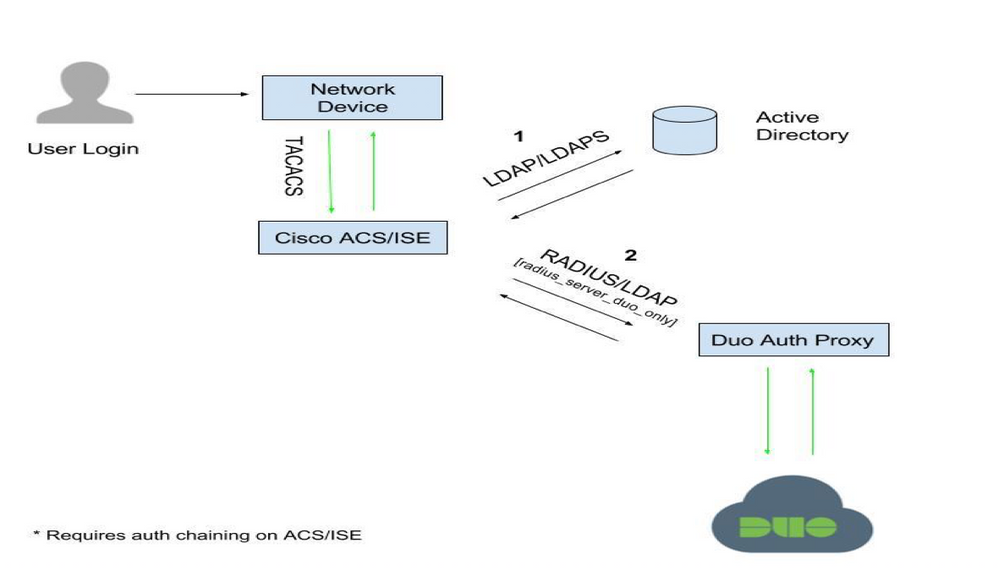
Thanks @Surendra for responding, so my understanding is ISE cannot support the customer ask (which is auth goes to AD first and then to token server). ISE can only forward the authentication request to DUO proxy first and then the proxy forwards to AD and duo token server i.e as shown in diagram below. Am I right?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-11-2019 01:19 AM
1. ISE forwards/proxies the request to DUO.
2. DUO validates the credentials entered by the user.
3. DUO sends an access-accept back to ISE if the credentials are correct.
4. ISE will lookup the user in the AD.
5. Sned a final access-accept back to the network device.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-04-2019 07:36 AM
So the auth proxy will check with the AD ( primary auth ) and then with Duo Cloud ( Secondary auth)
Why does ISE have to check with AD again?
Can ISE Integrate with Duo for 2FA, after doing primary auth with AD ( without a auth proxy in the middle)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-11-2019 04:55 AM
Yes, you are correct. What is the reason to hit AD first?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-05-2019 03:14 AM
Hi Surendra,
1) Do we need only to add ISE as a radius token server on achieving 2 FA?
2) Without doing ISE for authentication and DUO for authorization, can we done same authentication request get authenticated by ISE and DUO.
regards
hasitha
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide