- Cisco Community
- Technology and Support
- Security
- Network Access Control
- TEAP and ISE machine and user certificate authentication
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
TEAP and ISE machine and user certificate authentication
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-09-2021 11:51 AM
Hello guys.
Have anyone already configured TEAP with ISE ?
There is an issue with authorization matching because of the anonymous Radius Name.
Can we match Username from Overview or Authentication Details of the request ?
Or maybe there is a Registry key on Windows to make Windows to send /host as Radius User Name ?
Any other suggestions are appreciated.
Here is a description.
This is ISE 3.0 and a switch 3750 and Windows 10 with TEAP configured.
1) TEAP sends anonymous as Other Attributes -> Radius Username for both machine and user authentication all the time,
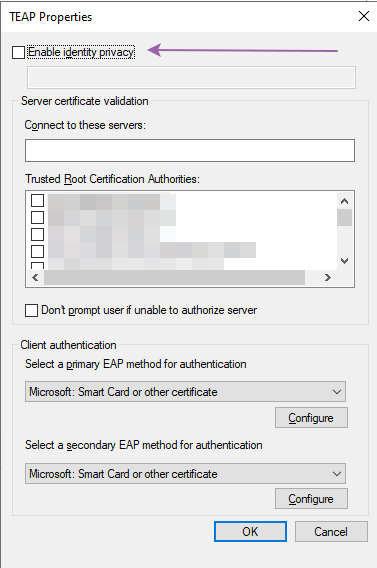
but Windows "Enable identity privacy" it is not configured.
2) For the "Machine only" authoriZation the well known filter Radius User-Name == starting as /host doesn't work because the host doesn't send it in the request.
3) If configure the AuthZ rule to match User-Name == starting as "anonymous", it matches for user authentication/authorization as well.
These is a piece of the logs for the machine authentication:
Overview
| Event | 5200 Authentication succeeded |
| Username | anonymous,host/HOST.DOMAIN.com |
Authentication Details
| Source Timestamp | 2021-06-09 12:49:28.762 |
| Received Timestamp | 2021-06-09 12:49:28.762 |
| Policy Server | ise |
| Event | 5200 Authentication succeeded |
| Username | anonymous,host/HOST.DOMAIN.com |
Other Attributes
| RADIUS Username | anonymous |
Windows 10 configuration:
.
.
- Labels:
-
Identity Services Engine (ISE)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-09-2021 11:50 PM
M.
-- Each morning when I wake up and look into the mirror I always say ' Why am I so brilliant ? '
When the mirror will then always repond to me with ' The only thing that exceeds your brilliance is your beauty! '
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-10-2021 12:21 PM
Hello Marce.
Thank you for the link. It is not like I posted this thread after googling for 5 minutes only
Regarding the guide:
AuthN
1)There are no explicit requirements for the certificate authentication.
They don't show us what is included in the "cert_profile" as well.
I am going to check CN for a machine certificate and SAN for user certificate by creating 2 separated rules. It is not working correctly.
On the windows machine I am not checking "Enable identity privacy" checkbox but it still uses Radius User-Name = ANONYMOUS for both machine and user requests.
AuthZ
2) For these policies - I would prefer these rules to be more specific then it is configured in the guide.
For that reason I am trying explicitly distinguish Machine vs User authentication by checking /host portion of the name.
This is the way it works for NAM, for example.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-10-2021 06:15 AM
I have not run into this issue when testing TEAP. That anonymous identity you see in live logs means that there was only machine auth.
See if this helps/sheds light: Using TEAP for EAP Chaining – Cisco ISE Tips, Tricks, and Lessons Learned (ise-support.com)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-10-2021 12:56 PM - edited 06-10-2021 12:57 PM
Hello Mike !
Thank you for your reply. I red this guide as well.
The point is I am not configuring anonymous on TEAP, so I am expecting Radius User Name to contain /host portion of it the way it works for EAP-FAST.
I am very positive that for User Authentication this fiend remains the same.
Other field in the logs are changing, though.
Such as: Username USERNAME,host/HOSTNAME.DOMAIN.com
The request has user portion /host domain portion in the request.
Again we don't see what is it in SecDemo_AD_CAP certificate profile for AuthN.
The policy in the guide doesn't check a certificate portion like CN or SAN.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-10-2021 02:42 PM
At the same time I have to distinguish between the statuses:
1) MACHINE PASS, when user didn't attempt to authenticate, and grand access,
2) and Machine Pass but a User fails, so the access should not be granted.
For both cases the eap chaining status will be User failed and machine succeeded.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide