- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: Unable to complete BYOD onboarding process on iPhone
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-11-2017 03:24 PM
I'm not sure if this is an ISE or an iPhone issue.
ISE 2.2.0.470
Patch 2
iOS version 10.3.3
I have ISE set up to use an Entrust certificate for Portal and EAP Authentication. Native Supplicant Provisioning is set up to issue the profile with ISE Internal CA from the Certificate Template.
My iPhone is failing the onboarding process with an error message of:
Profile Installation Failed
The server certificate for <"https://....> is invalid.
Here are the steps I take:
1. Connect to the ssid and enter my username and password.
2. Then, I have to trust the certificate. According to Apple's documentation, Entrust should already be a trusted root certificate. Do you know why I have to trust this certificate?

3. After trusting the certificate, I'll open a webpage and get redirected to the BYOD portal.
4. Then enter a Device Name
5. Click the Launch the Apple Profile and Certificate Installers Now button.
6. I'm then prompted to Install Profile (I believe this is the "ISE Internal CA" from the Certificate Template")
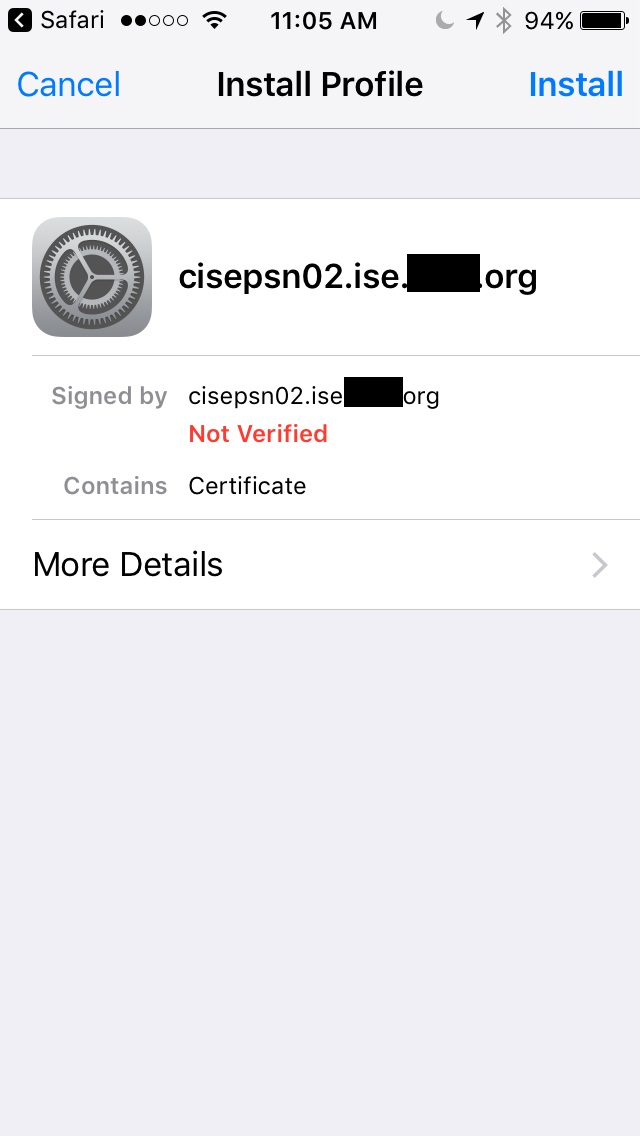
7. I then enter my iPhone's password
8. Then click install at the Warning page where it says the authenticity cannot be verified.
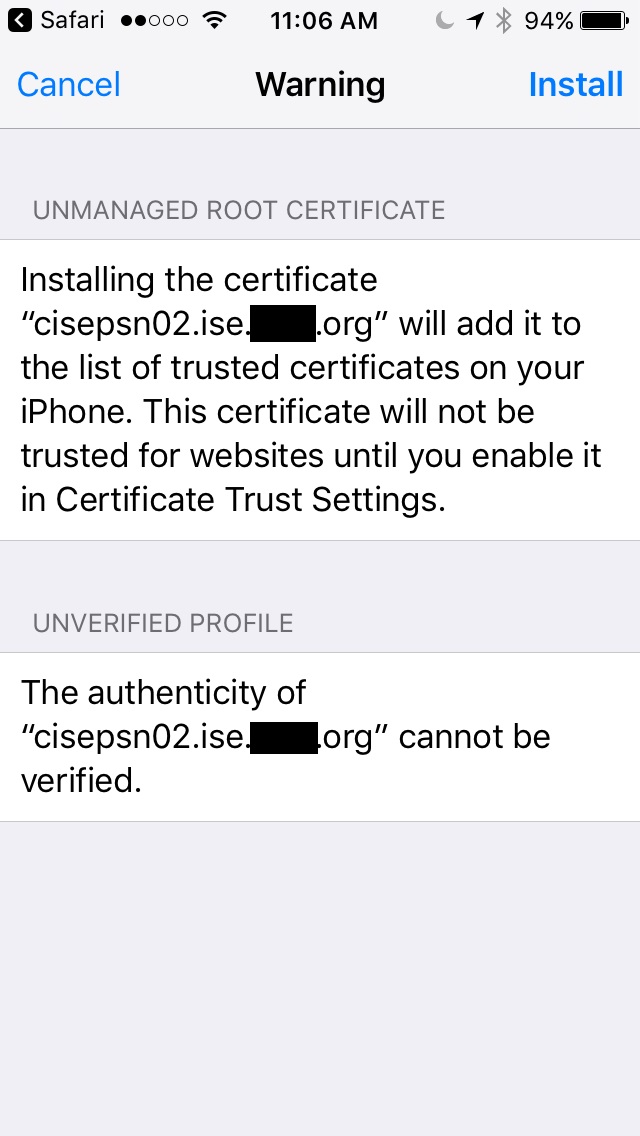
9. The Profile Installed page is showing verified. I click Done.
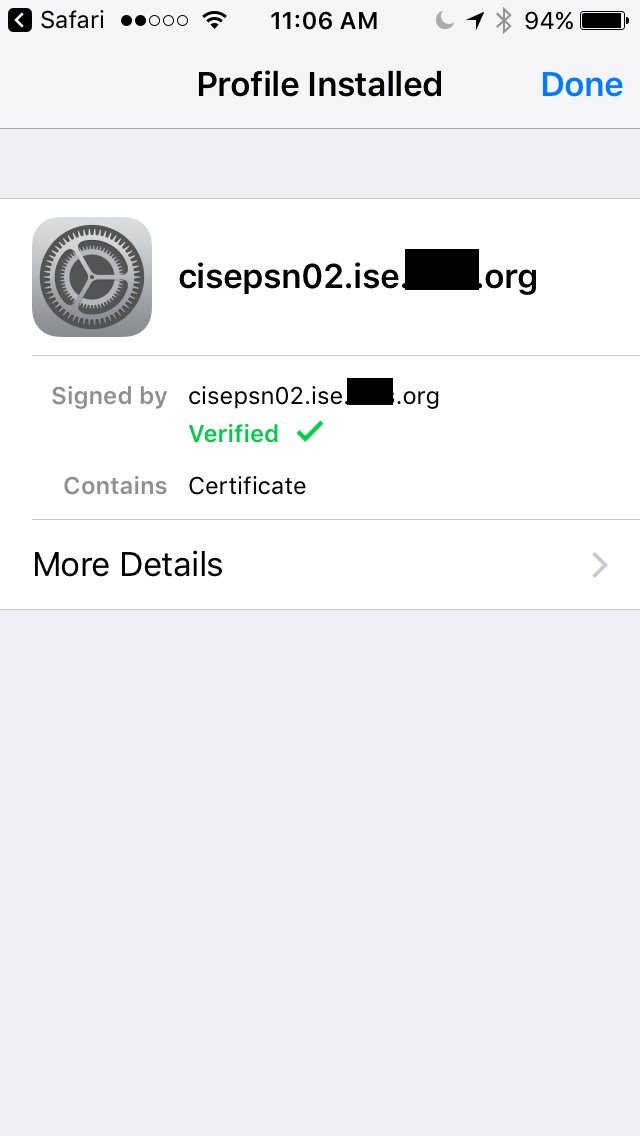
10. The wizard attempts to install another profile.
11. I click the Home button and navigate to Settings > General > About > Certificate Trust Settings and Enable Trust
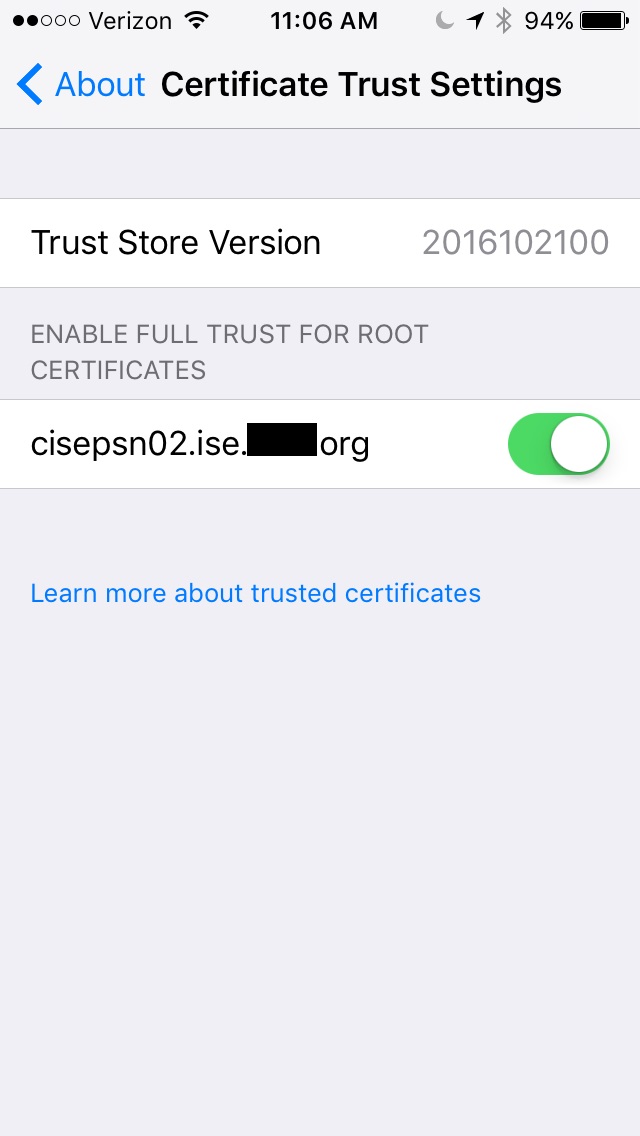
12. I return back to Safari to complete the onboarding process
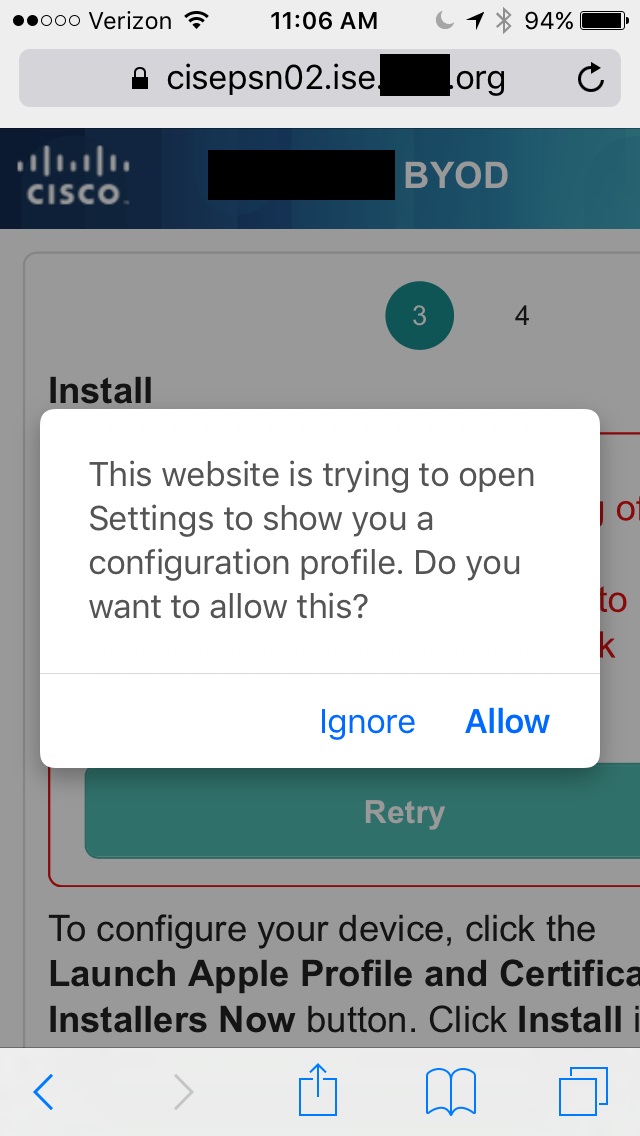
13. I attempt to Install the second "Install Profile"
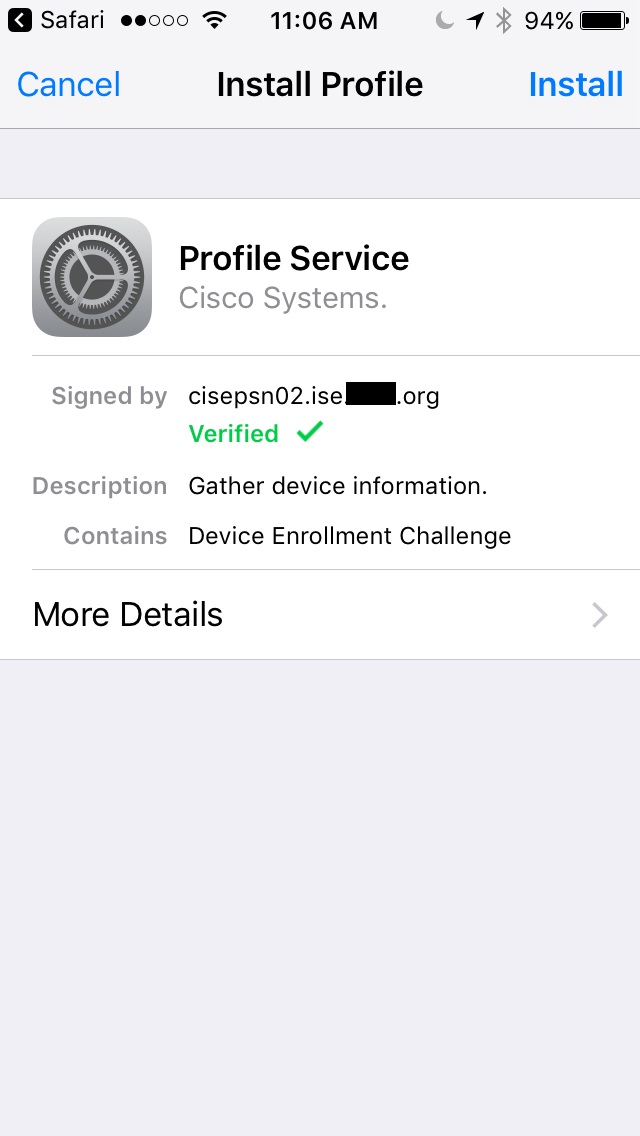
14. I enter my password, click install, and it fails.
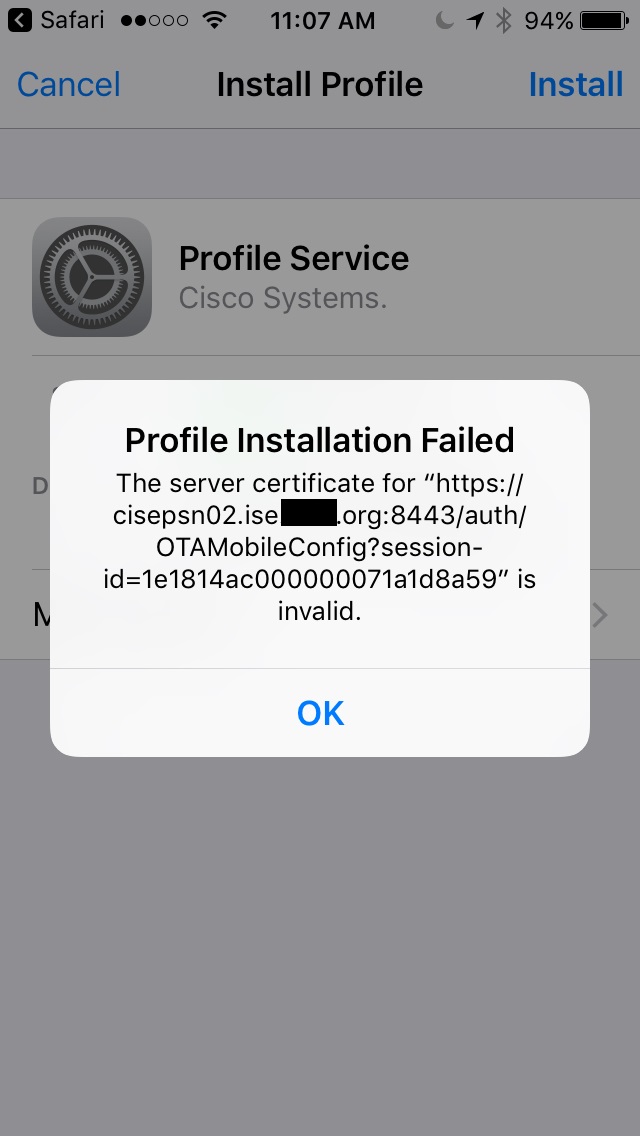
Does anyone have any ideas of why it is failing to install the Profile with a certificate that has been explicitly trusted on the phone?
Thanks,
Sean
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-12-2017 11:51 PM
To make a long story short, a reboot fixed the problem.
I think my environment just got jacked up somehow.
Long story:
I checked the test portal URL and it was showing that is was using the Entrust certificate. The test port URL was an IP address, instead of a name. It was using the Entrust certificate. I then checked all 4 of my PSNs by editing the "test portal URL" with the PSN fqdn. (I was unable to navigate to https://cisepsn01.ise.sTLD.org. I needed to add the https://cisepsn01.ise.sTLD.org/portal/PortalSetup.action... section as well.) They were using the Entrust certificate as well.
The onboarding was working when I was using certificates from our MS CA. I switched it to Entrust Public CA so that BYOD devices would already trust the certificate. As a test, I tried to put it back to the MS CA. This is were I noticed something was off.
When I changed the Portal and EAP Authentication certificate, I only made the change to the PAN. I thought it would update the change on all the PSNs automatically. Which I think that is what it is supposed to do. It didn't sync up correctly with the PSNs. Some of the PSNs had different certificate settings than the others. Also, cisepsn03 had EAP Authentication set on two different certificates at the same time, which I thought was impossible. I then tried to manually change it in the GUI, but the change would fail. Then, I tried going into the command line to try to find a command to manually set the certificate. I didn't find one, but I did notice that Certificate Authority was disabled from the "show application status ise" command. I went back to the gui, disabled the Internal CA, then re-enabled the Internal CA. I went back to the command line and Certificate Authority was still showing disabled. I then rebooted all PSNs. (We still aren't in production yet.) All PSNs came back up and were showing Certificate Authority as running. I then set the certificates for Portal and EAP Authentication on the PAN. This time, it synced automatically to all PSNs.
I still have to manually trust the Entrust certificate on my iPhone, which is lame. But, I am able to complete the onboarding process again.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-11-2017 05:56 PM
It seems you are using two different certificates -- aaa.ise.sTLD.org and cisepsn02.ise.sTLD.org. The latter appears to be self-signed and used by the portal. Is that done on purpose?
Nonetheless, the self-signed one should still work, after explicitly trusted. If it stays the same after rebooting the phone, then the Apple iOS might not like some of the properties on the self-signed certificate. I would suggest to switch to the aaa one.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-12-2017 12:32 AM
Hi hslai,
Yes, I'm using two certificates. My thought process was that any certificate presented from the ISE PSNs to ISE Endpoints will be signed by a Certificate Authority that is trusted by almost all devices by default. Also, all ISE Endpoints will present an internally-signed certificate to the ISE PSNs, that was manually configured as a Trusted Certificate in ISE.
I have configured the Entrust certificate on the BYOD Portal page and for EAP Authentication within ISE. When a user connects to the SSID without a certificate, they are redirected to the BYOD Portal page. ISE then presents the Entrust Certificate to the device. This Entrust certificate should already be trusted by iPhone by default, according to Apple's page here. Once they connect to the portal, a new profile with ssid and certificate gets pushed the device. The certificate in the profile is the self-signed certificate from ISE.
As far as I know, I can't push my Entrust certificate to clients (aaa.ise.****.org). I also can't make any changes to the Internal CA certificate (cisepsn02.ise.****.org).
-Sean
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-12-2017 10:10 AM
Is your BYOD portal not using TCP 8443? Please use the test portal URL and accessing https://cisepsn02.ise.sTLD.org:8443 and ensure they are both the Entrust one.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-12-2017 11:51 PM
To make a long story short, a reboot fixed the problem.
I think my environment just got jacked up somehow.
Long story:
I checked the test portal URL and it was showing that is was using the Entrust certificate. The test port URL was an IP address, instead of a name. It was using the Entrust certificate. I then checked all 4 of my PSNs by editing the "test portal URL" with the PSN fqdn. (I was unable to navigate to https://cisepsn01.ise.sTLD.org. I needed to add the https://cisepsn01.ise.sTLD.org/portal/PortalSetup.action... section as well.) They were using the Entrust certificate as well.
The onboarding was working when I was using certificates from our MS CA. I switched it to Entrust Public CA so that BYOD devices would already trust the certificate. As a test, I tried to put it back to the MS CA. This is were I noticed something was off.
When I changed the Portal and EAP Authentication certificate, I only made the change to the PAN. I thought it would update the change on all the PSNs automatically. Which I think that is what it is supposed to do. It didn't sync up correctly with the PSNs. Some of the PSNs had different certificate settings than the others. Also, cisepsn03 had EAP Authentication set on two different certificates at the same time, which I thought was impossible. I then tried to manually change it in the GUI, but the change would fail. Then, I tried going into the command line to try to find a command to manually set the certificate. I didn't find one, but I did notice that Certificate Authority was disabled from the "show application status ise" command. I went back to the gui, disabled the Internal CA, then re-enabled the Internal CA. I went back to the command line and Certificate Authority was still showing disabled. I then rebooted all PSNs. (We still aren't in production yet.) All PSNs came back up and were showing Certificate Authority as running. I then set the certificates for Portal and EAP Authentication on the PAN. This time, it synced automatically to all PSNs.
I still have to manually trust the Entrust certificate on my iPhone, which is lame. But, I am able to complete the onboarding process again.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-08-2018 12:32 PM
One of the reason why the IOS device would not trust the certificate. The IOS 11 has a list of trusted certs. Please see the link provided. https://support.apple.com/en-us/HT208125
The trust certificate for entrust by Apple IOS device is G2 which is a public certificate. My guess is that you are running a G3 certificate on your IOS device. This is a private SSL certificate by Entrust. This is not trusted by the IOS device. Now it looks like android has a list of trusted certificate also. The reason I know this. I was running into the exact error message. It took me about two weeks to understadwhat was going on.
This is Cisco work around fix. It worked for me a few times on the G3 private SSL but stopped working all together this was IOS 11.0.4. https://bst.cloudapps.cisco.com/bugsearch/bug/CSCvd38467/?rfs=iqvred
| Entrust Root Certification Authority - G2 | Entrust Root Certification Authority - G2 | RSA | 2048 bits | SHA-256 | 4A 53 8C 28 | 17:55:54 Dec 7, 2030 | 2.16.840.1.114028.10.1.2 | 43 DF 57 74 B0 3E 7F EF 5F E4 0D 93 1A 7B ED F1 BB 2E 6B 42 73 8C 4E 6D 38 41 10 3D 3A A7 F3 39 |
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide