- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: user account in ISE keeps on disabling
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-15-2018 11:30 PM
Hi Everyone,
I'm just wondering why a network access user account defined internally to ISE keeps on disabling after some time.. i even make the "account disable policy" disabled. but still, the user account keeps on disabling after some time.
In our environment, we have another machine that needs to login to Cisco switches to make necessary config automatically. our Cisco switch is configured for AAA to look for tacacs.
In Cisco ISE we configured policy for tacacs to look for active directory and internal.
The machine that is logging into our Cisco switches doesn't have an active directory account, that is why we defined a user internal to ISE.
See attached image for reference.
any advice, please
thank you and regards,
ben
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-16-2018 03:56 AM
Check password lifetime and lockout policy for failed login attempts. It may be expiring due to password change due or script is rapidly exceeding failed login attempts. Try deleting and re-entering the values expected. Also check for the fallback policy if user not found. Is ID sequence set to continue to next store if User Not Found in AD? Consider building a separate policy set for this access, or separate rule in main policy set to match this specific use case so you can set the correct ID store as first/only selection. You should see log history of failed attempts. If basic troubleshooting does not ral issue, then may need to open TAC case.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-20-2018 05:58 PM
My screenshot shows the Password Lifetime option [v] Disable user account after [ 60 ] days if password was not changed.
If you indeed set it like that, then the user will get disabled because the password not periodically updated.
Also, please try creating a new user with username all in lower case.
If none helped, please engage Cisco TAC, as we are likely needing a copy of your CFG backup to debug further.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-16-2018 03:56 AM
Check password lifetime and lockout policy for failed login attempts. It may be expiring due to password change due or script is rapidly exceeding failed login attempts. Try deleting and re-entering the values expected. Also check for the fallback policy if user not found. Is ID sequence set to continue to next store if User Not Found in AD? Consider building a separate policy set for this access, or separate rule in main policy set to match this specific use case so you can set the correct ID store as first/only selection. You should see log history of failed attempts. If basic troubleshooting does not ral issue, then may need to open TAC case.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-17-2018 12:47 AM
password lifetime for this account is disabled. ill check if there is a lockout policy set for failed login attempts.
the sequence I make is AD then Internal.
ill try to build a separate policy set for this access using the sequence to Internal only and see if it will be disabled on its own again.
thank you and regards,
ben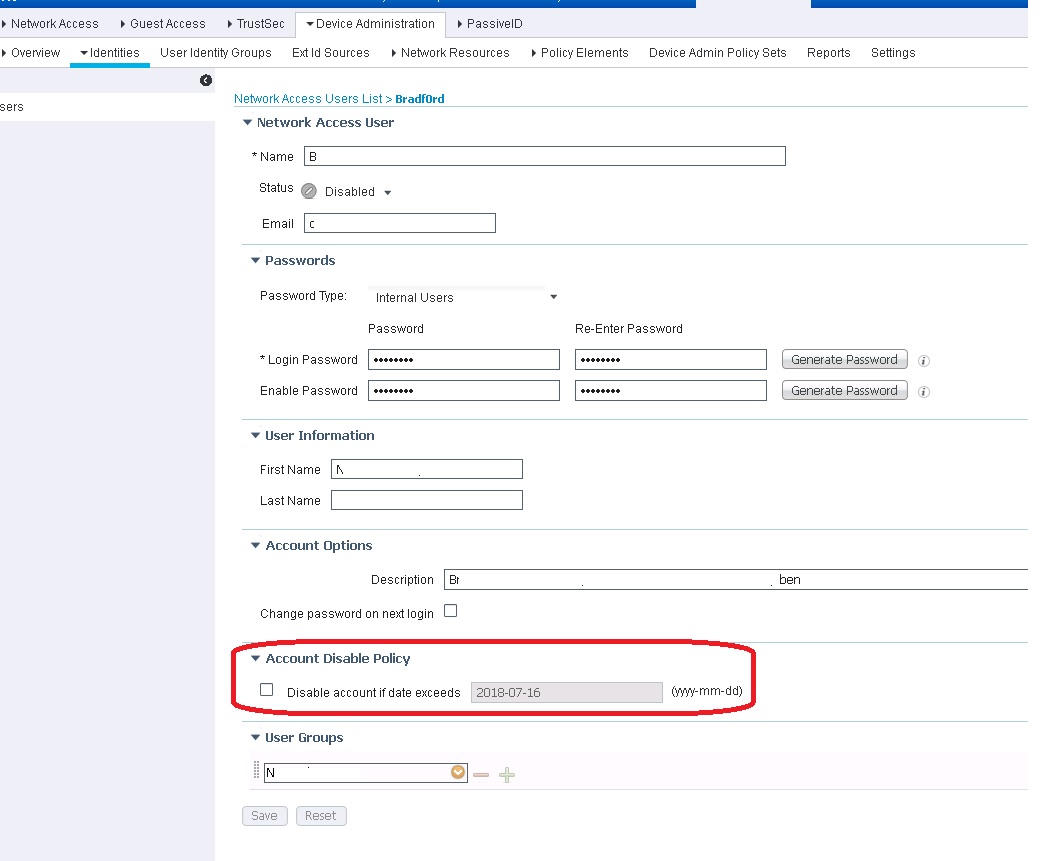
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-17-2018 09:32 AM
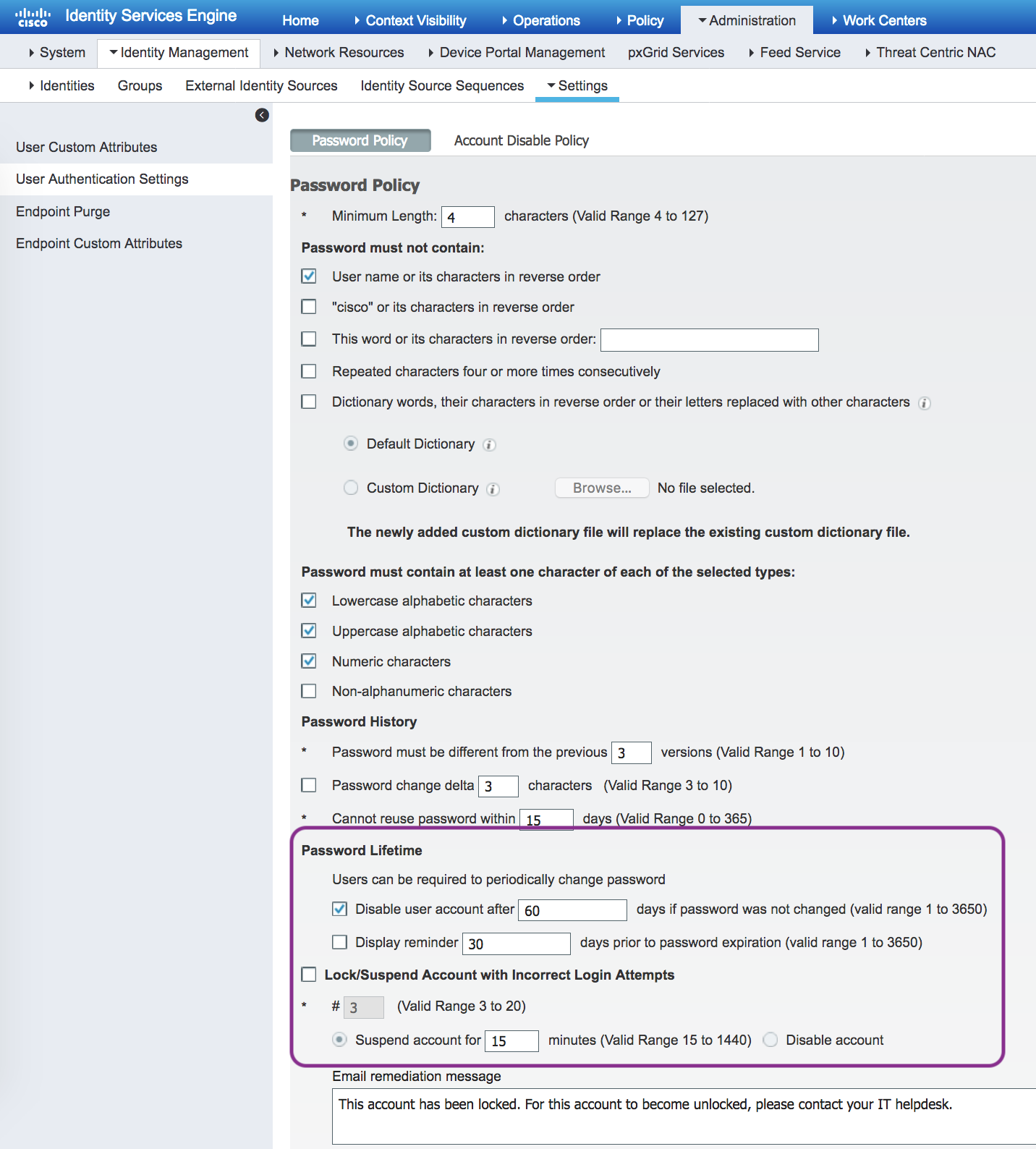
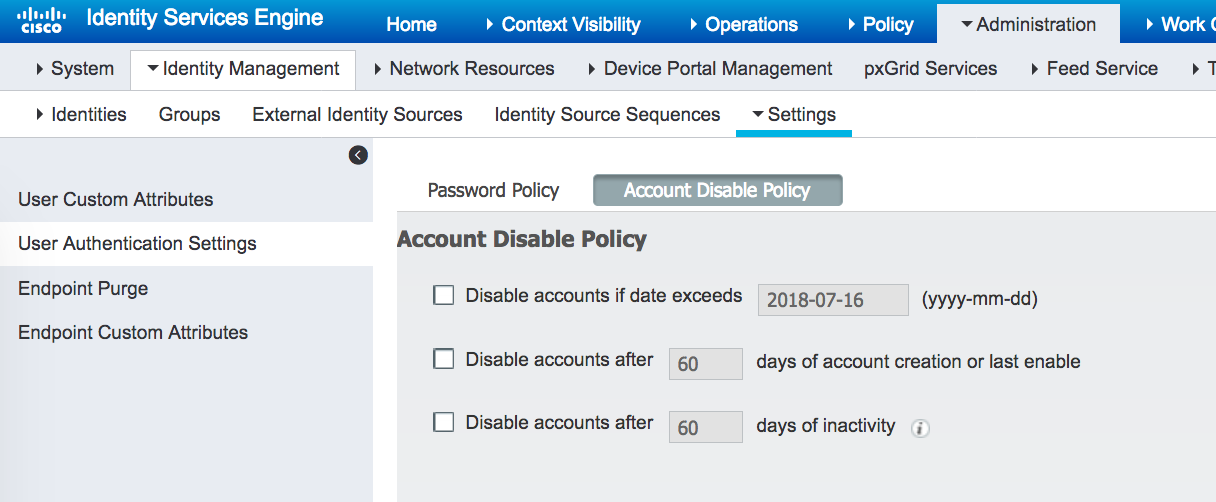
Please check the global settings of password policy and account disable policy for internal users.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-20-2018 04:30 AM
I did check, and the settings are exactly the same screenshot you posted. I checked today and the internal user account becomes disabled again. ![]()
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-20-2018 05:58 PM
My screenshot shows the Password Lifetime option [v] Disable user account after [ 60 ] days if password was not changed.
If you indeed set it like that, then the user will get disabled because the password not periodically updated.
Also, please try creating a new user with username all in lower case.
If none helped, please engage Cisco TAC, as we are likely needing a copy of your CFG backup to debug further.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-22-2018 01:24 AM
hslai wrote:
My screenshot shows the Password Lifetime option [v] Disable user account after [ 60 ] days if password was not changed.
If you indeed set it like that, then the user will get disabled because the password not periodically updated.
Yesterday, I found that the user becomes disabled again.. I uncheck the box for "Disable user account after [ 60 ] days...". today I didn't find the user account disable. Will observe it for now and see.
Thank you very much Hslai ![]()
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-20-2018 05:01 AM
I did create another policy set only for the server01, this server automatically logins to network devices but doesn't have AD account (the reason we create internal user).
image01: is the original policy where the sequence is AD then Internal. with exception to Administrators (uses AD) and server01 (uses Internal).
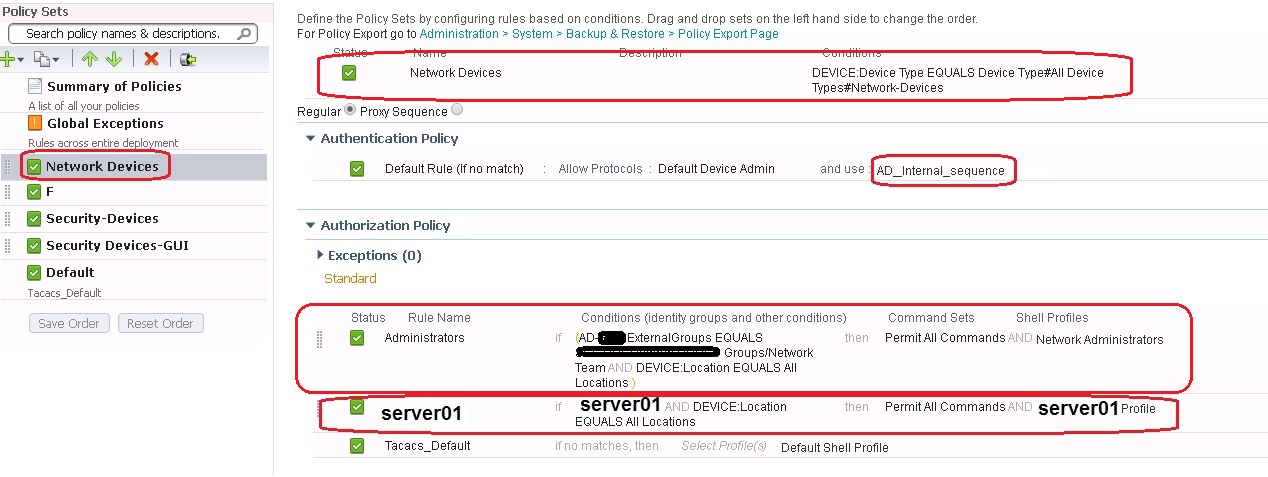
image02: created a separate policy for server01 (Internal), and it works fine. but since it is above the "Network Devices" policy, we cannot login now to network devices using AD.
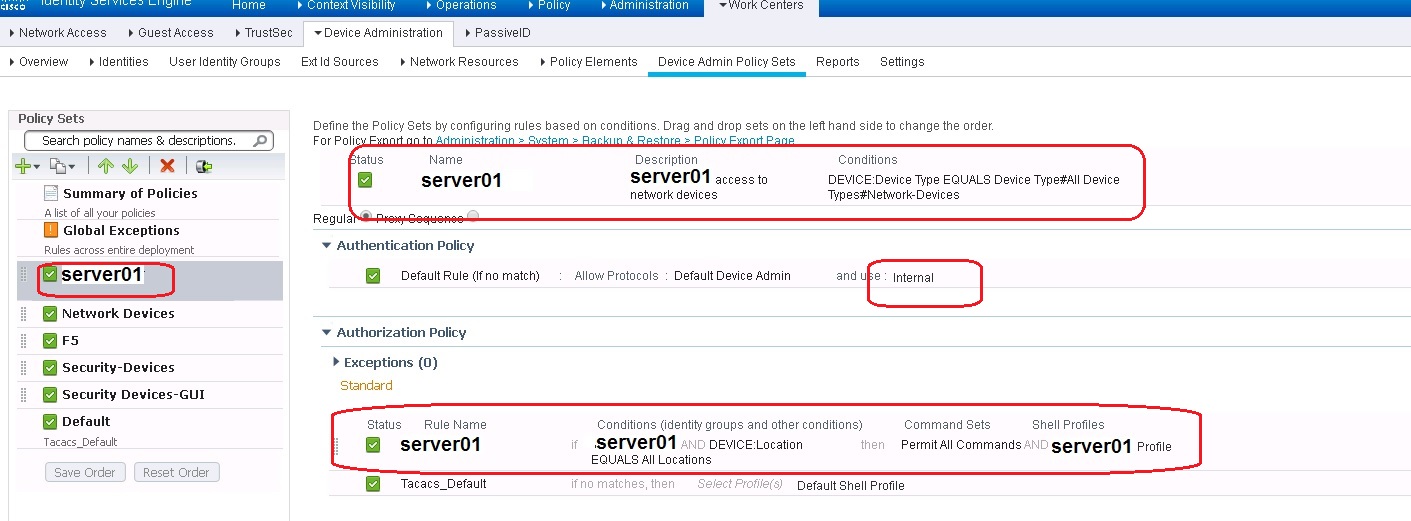
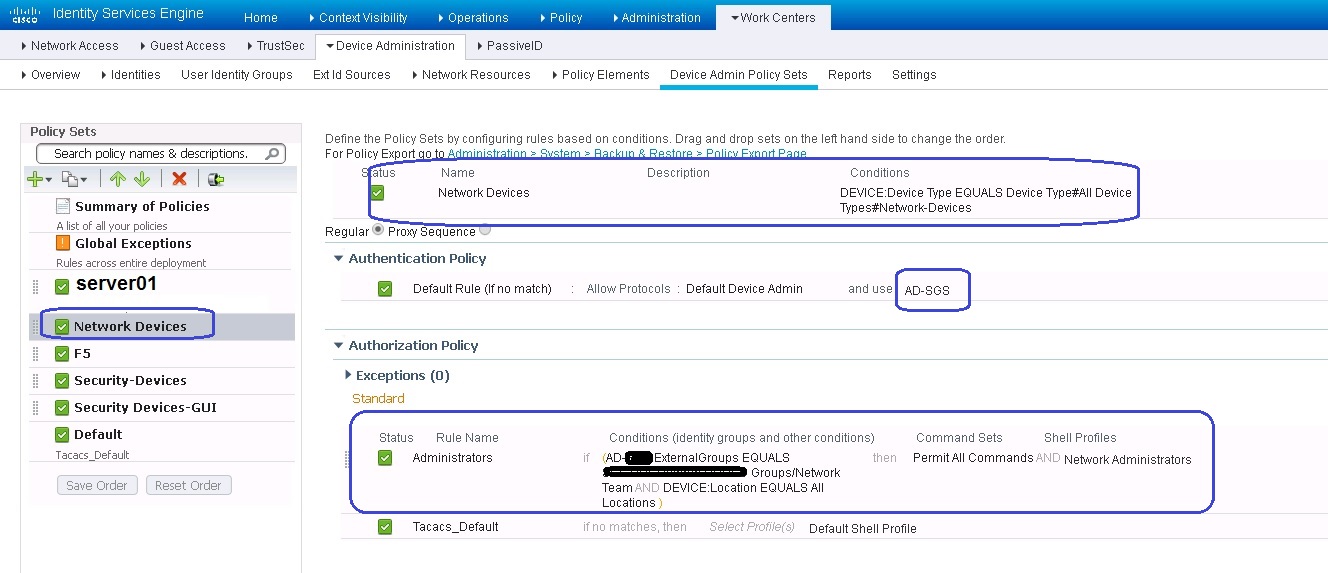
image03: Content of "Network Devices" policy. If a make this policy above "server01" policy then I can now log in to a network device using AD. but then log in to a network device using Internal will fail.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-22-2018 01:25 AM
Thank you very much Chyps ![]()
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide

