- Cisco Community
- Technology and Support
- Security
- Network Access Control
- VLAN change based on guest user type
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-08-2020 01:35 PM
Hi,
I'm new in ISE, doing some test and PoC's right now and I have a question - is it possible to move a guest user (authenticated on a webauth page) to a specific VLAN based on the guest type?
My idea is to create different guest types with different "network access levels" - for example "new guests" are moved to a "limited access" VLAN, but "known guests" are put into a "full access" one.
Is it doable in ISE 2.7 or the only option is to use a different SSID's?
Regards,
Piotr
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-13-2020 05:22 PM
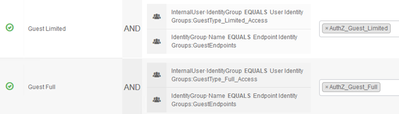
There are two typical associations related to Guest services... Guest Type and Endpoint Identity Group.
The Guest Type is assigned by the Sponsor at the time of the Guest account creation. A Sponsor with the right permissions (e.g. Sponsor All with 'can create accounts' with the relevant Guest Types) can also change the Guest Type after the initial account creation. ISE automatically creates a User Identity Group for each Guest Type.
The endpoint MAC Address is associated with the Endpoint Identity Group as part of the Guest Registration flow (default is GuestEndpoints). The common documented Guest flows use this EIG association to allow registered endpoints to connect without the Guest user having to constantly login to the Guest Portal.
You could use either (or both) of these attributes in your AuthZ Policy to provide differentiated access between your 'limited' and 'full' access guests/endpoints.
Example:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-08-2020 04:01 PM
Dynamic VLAN assignment is possible on a Cisco WLC. See this TechNote for an example.
The difficulty with your scenario is answering questions like:
- What constitutes a 'new guest' vs. a 'known guest'?
- When does a 'new' become a 'known' and what attribute can ISE use to differentiate between them?
There are various examples of Guest configuration and scenarios at cs.co/ise-guest that might give you some ideas.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-08-2020 11:21 PM
Let me explain the baseline - one of our clients has a network (wireless VLAN) with a lot of restrictions regarding applications (e.g. YouTube is completely blocked). When any of employees wants to use YouTube, has to ask for it and there is a different SSID temporarily enabled (different VLAN) with full Internet access.
My idea was to create (manually) a guest user for anyone who wants to use YouTube and put this user into a "YouTube' user group. After webauth, such user is being switched to a full access VLAN (based on the group). Is it a good idea?
I know that there is a lot of features which help to control users, but in this case the network admin want's to have a manual control over full Internet access. I'm just trying to find a best solution having C9800 as a controller, 3 FlexConnect locations, AD and ISE 2.7
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-09-2020 12:02 AM
Hi,
As long as the required policy are already in place (i mean to which resources does the WIFi user get access to), and ISE just needs to put the user in the proper VLAN, this is a simple task. You'll be having two different groups of users, and based on the group membership, ISE assign a different VLAN.
Regards,
Cristian Matei.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-09-2020 12:44 AM
Yes, but is it possible regarding guest users that are not in the AD?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-13-2020 05:22 PM
There are two typical associations related to Guest services... Guest Type and Endpoint Identity Group.
The Guest Type is assigned by the Sponsor at the time of the Guest account creation. A Sponsor with the right permissions (e.g. Sponsor All with 'can create accounts' with the relevant Guest Types) can also change the Guest Type after the initial account creation. ISE automatically creates a User Identity Group for each Guest Type.
The endpoint MAC Address is associated with the Endpoint Identity Group as part of the Guest Registration flow (default is GuestEndpoints). The common documented Guest flows use this EIG association to allow registered endpoints to connect without the Guest user having to constantly login to the Guest Portal.
You could use either (or both) of these attributes in your AuthZ Policy to provide differentiated access between your 'limited' and 'full' access guests/endpoints.
Example:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-15-2020 01:49 AM
Thank you Greg, that is what I was looking for :)
I will try to test it now and check the result.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide