- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: VLAN group and IP fixed from DHCP Server
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-31-2017 03:58 AM
Hello,
As an introduction, my customer has ISE 2.0.1Patch 1 full distributed deployment with 4 x PSN in 2 different datacenters. He has several buildings and branch offices and the endpoints on these places are authenticating against the PSNs in the DCs.
In order to reduce broadcast domains, customer created different VLANs for the corporate network. From ISE, we always push a VLAN group called "Corporate" and we configure this VLAN group in the switches adding into it the corporate VLANs existent on the switch. All is working fine, the endpoints receives and IP from the corporate VLAN less used inside the VLAN group (Corporate).
The problem we are facing now is due to some users have an static assignation in the DHCP server, some MAC addresses always receive a specific IP which has specific access in further firewalls. To receive this specific IP address, the endpoint must be in a specific corporate vlan and as we are pushing the VLAN group (Corporate) from ISE, sometimes the endpoint "falls" in the correct VLAN inside the vlan group and receives the expected IP but many times it "falls" into another VLAN so the IP delivered by the DHCP Server is not the fixed one and get no access through the firewalls.
I was planning to create a specific AuthZ rule to match this users or endpoints and deliver them an AuthZ Profile without VLAN pushing, only and ACCESS ACCEPT, so they will always go to the vlan configured in the switch port, which is the correct one. But the problem is that this solution doesn't scale properly and they've already confirmed that there are more than 700 users/endpoints in the company in this situation so this solution is unmanageable and not valid for them.
Does anybody face this before? What would be the best way to tackle this?
Thanks,
Víctor.
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-01-2017 10:59 AM
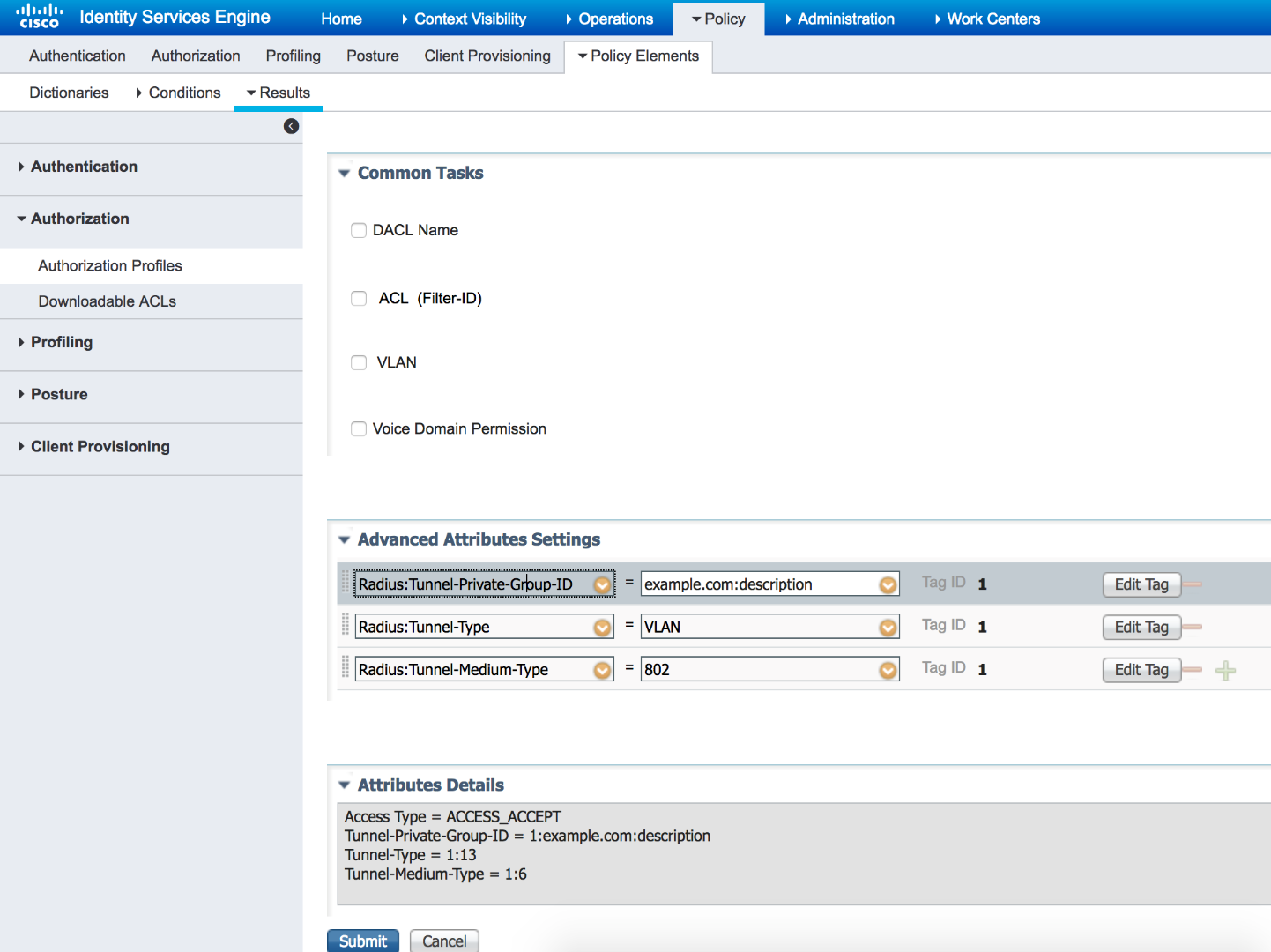
You can use per user attribute in AD or internal database. Simply populate an AD or internal DB attribute with VLAN ID or name and then use it dynamically during Authorization. Here is an example using AD:Description attribute for VLANs. If using AD, you need to ensure the attribute is indexed attribute for faster retrieval:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-31-2017 08:57 AM
I’m sorry to ask a question in response to your question. Will you please help us understand why you are choosing VLAN assignment vs dACLs? Also, why are the static users being pushed the wrong VLAN? Is it possible to get the static users in an AD group or an OU that you can then use to test membership and determine which AuthZ profile to respond with?
Thanks,
George
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-01-2017 10:59 AM
You can use per user attribute in AD or internal database. Simply populate an AD or internal DB attribute with VLAN ID or name and then use it dynamically during Authorization. Here is an example using AD:Description attribute for VLANs. If using AD, you need to ensure the attribute is indexed attribute for faster retrieval:

Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide

