- Cisco Community
- Technology and Support
- Security
- Network Access Control
- VPN Authentication using Certificates Only, with ISE Posturing
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-25-2020 07:01 AM
Hello,
I am trying to setup a remote VPN solution using Anyconnect 4.8 with ISE for Posturing Only...we do not want ISE to authenticate the connection, just to run a Posture scan on the client and allow/reject based on a posturing policies.
We will be using “User” certificate authentication to Cisco ASA only. We do not want the client to prompt for username/password.
Once authenticated to the ASA, we need ISE to run a posture scan, basic requirements for now, we are just checking to see if a file exists on C drive.
Steps Taken:
If we use “certificate” & “aaa” in the Tunnel-group configuration on the ASA, we are prompted for a username/password, and this works without any issues authenticating firstly against the CA certificate on the ASA, and then with username/password against a local account in ISE - so works, but we don't want 2FA.
If we use “certificate” only authentication and send through the "username-from-certificate", then a user must be configured in ISE's local identity store for posturing to work. If a user is NOT present locally in ISE, then the posture assessment goes straight to “Compliant” – even though the machine is not in a compliant state (missing file on C drive)
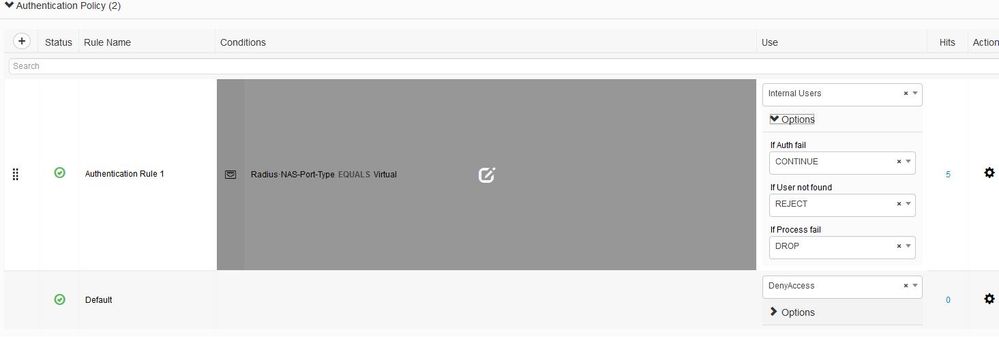
Under the Authentication Policy in ISE, we have Use “Internal Users”, “If Auth Fail” set to continue, and “If user not found” set to Reject, however the connection is still allowed even if the user is not found, yet posturing does not take place.
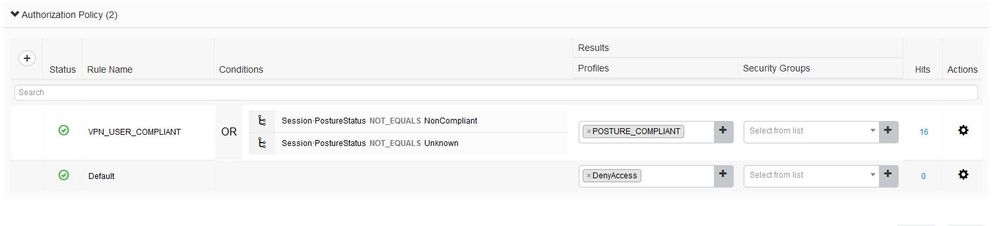
The Authorization policy only has two outcomes, posture-status "Compliant" or "not-Compliant".
In monitoring it goes directly to "compliant" but the posture scan never takes place. To the end user it shows the system as compliant and network access is allowed, when in reality, CoA never happened, so the full access dACL never gets applied.
Can anyone please advise if this is a supported configuration, and if so advise on the configuration steps required for this to work?
Tried searching the forums and found similar issues, but not exactly how I need it to work as above.
Many thanks in advance,
Marc
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-29-2020 07:58 AM
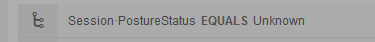
This is because your ISE authz policies are not properly setup (shown/determined from post above). We also cannot see your CPP policies. That ASA config will work to accomplish what you need from an ISE authz only and posture functionality perspective. I now recommend working on ensuring you have properly configured the ISE portion of the solution via the guides shared. Posture status can have three results (unknown, compliant, non-compliant). At the start, Unknown is first & should be where you redirect users, and begin the posture assessment. You need an authz policy to support this, which would reference the following condition:
Then the authz profile that gets assigned to this policy should have your web redirect setup to steer client to proper CPP and assign redirect acl to session. Then once client goes through posture assessment and ISE deems client as (non-compliant or compliant) the session status changes and grants respective network access.
I strongly suggest watching videos on labminutes as it will assist you with the ISE config. HTH!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-25-2020 07:54 AM - edited 06-25-2020 07:56 AM
Can anyone please advise if this is a supported configuration, and if so advise on the configuration steps required for this to work?
-You can absolutely accomplish what you want to do. I currently have a customer that does CAC auth against the ASAs, and relies only on ISE/AD for authorization and ISE posturing. In the connection profile we set it up to extract certificate UPN to pass that to ISE that is then mapped to AD sec groups. I think the tricky part for your config will be mapping the users to internal ISE accounts. Any chance you have the ability to integrate with AD? Also, there should be three states: Unknown, Compliant, or Non-Compliant. The "unknown" state is where you would setup ISE portal redirection to begin the client provisioning/posture assessment which then authorizes the client to the respective network based on Compliant or Non-compliant result, which then throws a new dacl to the ASA/user session. I would recommend looking at these two sources as they have helped me in the past on this topic and they should give you a better understanding of the overall process:
https://community.cisco.com/t5/security-documents/ise-posture-prescriptive-deployment-guide/ta-p/3680273
http://labminutes.com/video/sec
Good luck & HTH!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-26-2020 01:51 AM
Hi Mike,
I have the certificate mapping working. However the username UPN needs to be configured as a local account in ISE, if the account is not there, or there is a typo, then posturing never kicks in and the end user Anyconnect client goes straight to "Compliant", which actually is not true as the scan never takes place. From ISE side it also shows the session as compliant, but never actually did any scanning.
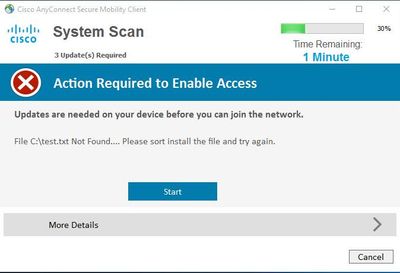
If the username is configured in ISE correctly, then everything works OK. When I connect I get the popup "System Scan" window telling me action is required (attached). Unfortunately we have no option to integrate into AD.
So the problem I have is that ISE does not take any notice of the Authentication step "If User not found" = Reject, and for some reason thinks the default session PostureStatus is "Compliant" - when in reality it never performed a scan to find out.
Attached a few screenshots of my authentication and authorization policies. As you can see its pretty basic. We either want the client to be compliant (after doing a scan), or we want to reject the connection completely. We do not have any need for remediation or client provisioning.
Appreciate any help you can give.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-26-2020 05:49 AM
-Flip 'If Auth Fail' to Reject. This should fix that problem. Take a peek at this guide as it will assist you further: https://community.cisco.com/t5/security-documents/ise-authentication-and-authorization-policy-reference/ta-p/3850472
Lastly, if you use labminutes and the posture guide it will assist you with properly deploying this solution. HTH!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-29-2020 04:42 AM
Hi Mike,
Sorry this does not resolve the problem. Flipping "If Auth Fail" to Reject just rejects the whole session, as expected, as no password information is being sent in the Radius request.
I have looked at the Labminutes guides, as with many other guides. None of them relate to what I am trying to achieve. My problem is not that I cant get posturing to work using normal username/password or 2FA... my problem is that I only need ISE to do posturing, not Authentication.
Authentication is being done on the ASA using certificates. I just need ISE to Authorize the session based on "Compliant" or "Non-Compliant" - so far the scanning process only starts "IF" I have a user configured locally in ISE that matches the UPN sent from the certificate. If the user is not found, the end client does NOT do a posture scan, and the client moves to showing a green tick and the words "Compliant" - this is not true.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-29-2020 05:27 AM - edited 06-29-2020 05:56 AM
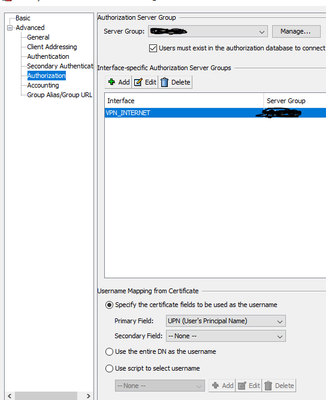
You can rely on ISE for authorization and posture assessment only. In the connection profile set the authentication method to certificate only. Then under Advanced->Auhtorization specify the authz server group (ISE), check the user must exist in DB, and properly configure username mapping from certificate. In this configuration the UPN will get stripped from Cert after CAC auth against ASA, passed to ISE for authz only, and your detailed radius live log for each session will depict authorize only.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-29-2020 07:11 AM
Hi Mike,
I have already tried this, it doesn't work. Its how I currently have everything configured now:
tunnel-group GROUP2 type remote-access
tunnel-group GROUP2general-attributes
authorization-server-group ISE
authorization-required <<<<< This is the tick box in your ASDM screenshot.
If I use "authorize-only" under the aaa-server then its the same result, goes straight to "Compliant" but never performed a scan. Live logs shows the Posture Status as "Compliant", when truth is its not.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-29-2020 07:58 AM
This is because your ISE authz policies are not properly setup (shown/determined from post above). We also cannot see your CPP policies. That ASA config will work to accomplish what you need from an ISE authz only and posture functionality perspective. I now recommend working on ensuring you have properly configured the ISE portion of the solution via the guides shared. Posture status can have three results (unknown, compliant, non-compliant). At the start, Unknown is first & should be where you redirect users, and begin the posture assessment. You need an authz policy to support this, which would reference the following condition:
Then the authz profile that gets assigned to this policy should have your web redirect setup to steer client to proper CPP and assign redirect acl to session. Then once client goes through posture assessment and ISE deems client as (non-compliant or compliant) the session status changes and grants respective network access.
I strongly suggest watching videos on labminutes as it will assist you with the ISE config. HTH!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-30-2020 04:30 AM
Hi Mike,
Success!!!
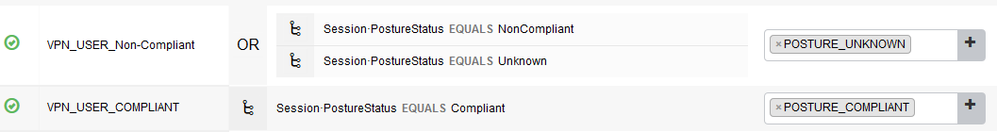
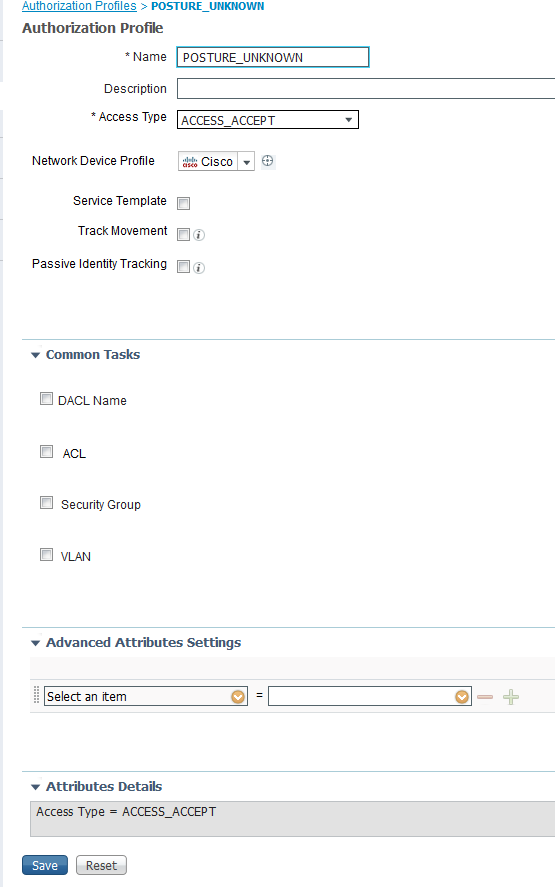
Separated the Authz policy as per below and sent the Unknown and Non-compliant to a blank Authorization Profile.
Shown below:
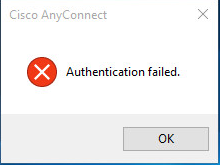
Strangely, this has also now kicked in the "If User not Found" to work as expected too. I get the expected error below as soon as I hit Connect, when a user has not been configured locally:
Like I said, I have watched the videos and gone through all configuration steps that would be aligned with a standard setup. I think I was more focused on why a username matching locally the Posture scanning starts, and when not, it doesn't. It also doesn't explain why in Live logs the connection is seen as "Compliant" - when a scan never took place.
Separating the Authz policy was the missing link.
Thank you for your help, its much appreciated.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-29-2020 05:35 AM
I've not tried this scenario, but what about configuring ASA aaa for "authorize-only", so authentication is skipped in ISE.
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-29-2020 07:15 AM
Hi Rob,
Thank you, but this doesn't work either. It gives the same result in that the client never performs a Posture scan and ends up going straight to a "Compliant" state, even though the file on C drive is missing.
Kind regards,
Marc
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide