- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Hi Joana,Were you able to
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
WiSM2 - ISE Central Web Authentication - Redirection ACL does not work for Guest Access
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-16-2014 08:51 AM - edited 03-10-2019 09:38 PM
Hi
I am using these devices to setup Central Web Authentication for Guest Wireless:
- WiSM2 - 7.6.110.0: Foreing Controller.
- WLC 5760 - 03.03.01SE: Anchor Controller.
- Cisco ISE 1.1.X
Mobility is UP between controllers. Clients can connect to GUEST SSID, get an IP address but they are never redirected to Cisco ISE Guest Portal for Authentication. Instead of going to ISE Web Portal, they can talk straight to the Internet bypassing any authentication.
I think the Pre-Auth ACL specified in the ISE Authorization Profile is not properly applied to the Clients so they are not restricted to talk to the Internet.
This is my configuration:
WiSM2:
1. Radius:

2. WLAN GUEST - WLAN ID 2:
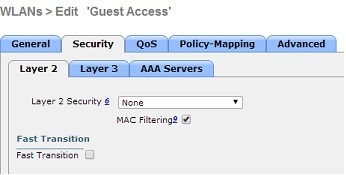
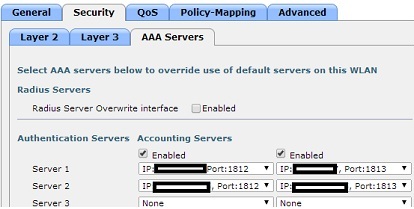

3. ACLs:
3.1 Unknown - Pre-Auth ACL that permits traffic to ISE.

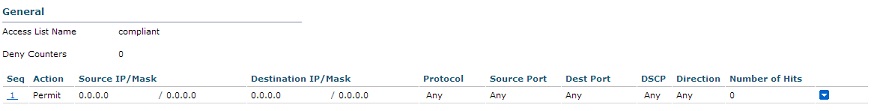
3.2 Compliant - User sucessfully authenticated:
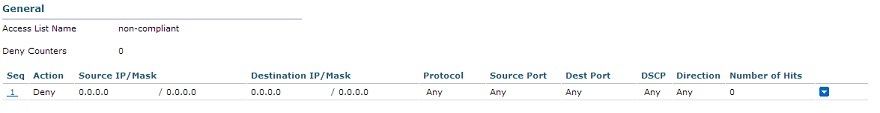
3.3 Non-compliant - User is not allowed.
4. Controller:
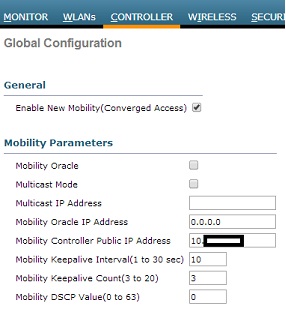
WLC ANCHOR 5760:
aaa new-model
aaa group server radius ISE
server name ise
aaa authentication dot1x ise_webauth group ISE
aaa authorization network cwa_macfilter group ISE
aaa authorization credential-download ise_webauth group ISE
aaa server radius dynamic-author
client '10.X.X.X (ISE IP Address)' server-key 7 1363D3AC00070D3E773B27E70A
auth-type any
ip access-list extended compliant
permit ip any any
ip access-list extended non-compliant
deny ip any any
ip access-list extended unknown
deny udp any eq bootps any
deny udp any any eq bootpc
deny udp any eq bootpc any
deny udp any any eq domain
deny tcp any any eq domain
deny ip any host '10.X.X.X'(ISE IP address)
deny ip any host '10.X.X.X'(DHCP Server IP Address)
permit tcp any any eq www
permit tcp any any eq 443
!
radius-server attribute 6 on-for-login-auth
radius-server attribute 31 send nas-port-detail mac-only
radius server ise
address ipv4 '10.X.X.X(ISE IP address)' auth-port 1812 acct-port 1813
key 7 033771233103226B5B5A0A113C4112
!
wireless mobility controller
wireless mobility group member ip '10.X.X.X WiSM2 Ip Address' public-ip '10.X.X.X WiSM2 Ip Address' group GUEST
wireless mobility group name GUEST
wireless mobility dscp 46
wlan GUEST 2 GUEST
aaa-override
client vlan 230
ip dhcp opt82 format add-ssid
ip dhcp server 10.X.X.X
mac-filtering cwa_macfilter
mobility anchor
nac
peer-blocking drop
no security wpa
no security wpa akm dot1x
no security wpa wpa2
no security wpa wpa2 ciphers aes
security dot1x authentication-list ise_webauth
session-timeout 1800
no shutdown
CISCO ISE:
1. Authorization Profiles:

I also configured: Airspace ACL Name = unknown. I am not sure if this is needed?? I have tried with/without this option.
2. Authentication:
3. Authorization:


4. Operations Authentication:
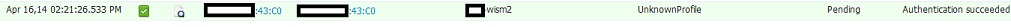
I never get the point where the profile is Compliant. It is always UnknownProfile/Pending.
Client:
WiSM2:

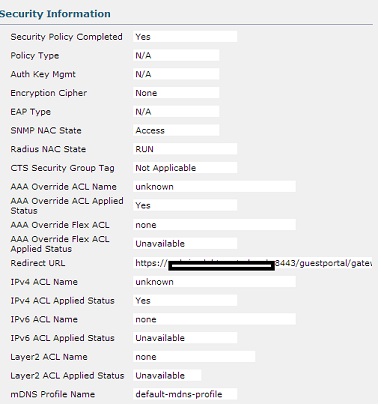
ANCHOR 5760:
 Even the Policy Manager State is "CENTRAL_WEB_AUTH", ACL "unknown" (pre-auth ACL) is applied and Redirect URL is pointing to ISE Guest Portal, clients bypass authentication and can talk straight to the Internet. They are not redirected to Cisco ISE for authentication at any time.
Even the Policy Manager State is "CENTRAL_WEB_AUTH", ACL "unknown" (pre-auth ACL) is applied and Redirect URL is pointing to ISE Guest Portal, clients bypass authentication and can talk straight to the Internet. They are not redirected to Cisco ISE for authentication at any time.
I would appreciate some help to understand why the redirection part of the process is not working and why any client traffic is allowed.
Thank you very much.
Joana.
- Labels:
-
AAA
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-23-2014 07:40 AM
any suggestions? I run out of ideas...
Although clients are able to talk to the Internet bypassing ISE Central Web Authentication, if I do it manually, copy the redirect URL and login, it works fine. I pass through the authentication/authorization policies configured on ISE successfully.
The issue is I am not automatically redirected to ISE (WLC doesn't seem to intercept web traffic) and my clients bypass the restrictions applied by the redirect ACLs. Any traffic is allowed.
Thanks,
Joana.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-24-2014 05:04 AM
your cwa_redirect ACL need to be configured correctly.. Refer this document.
You must deny the traffic that you want to redirect to guest portal for authentication.
HTH
"Please rate helpful posts"
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-24-2014 06:22 AM
Hi,
Thanks for you response.
I already followed the configuration steps of the document that you have suggested. This is the cwa_redirect ACL configured on my wism2 (foreign controller).
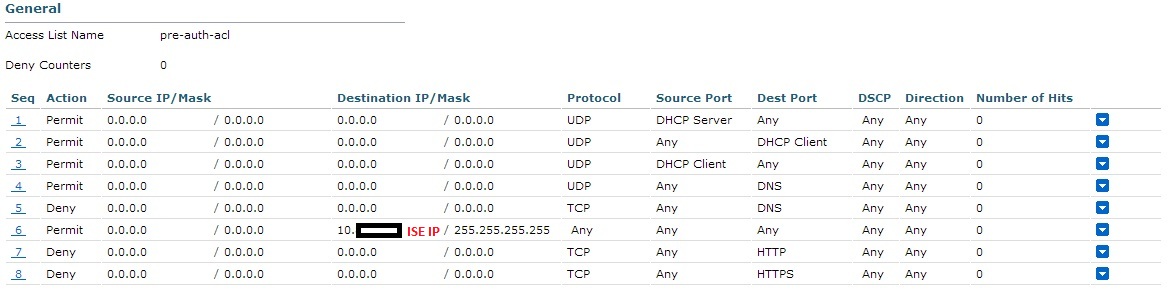
and this is the ACL configured on the Anchor Controller 5760:
ip access-list extended pre-auth-acl
deny udp any eq bootps any
deny udp any any eq bootpc
deny udp any eq bootpc any
deny udp any any eq domain
deny tcp any any eq domain
deny ip any host 'ISE_IP_Address'
permit tcp any any eq 80
permit tcp any any eq 443
According to the attached document, on the 5760 'deny' means do not redirect and 'permit' means redirect to ISE (the opposite to wism cwa_redirect ACL). However, I have changed deny by permit and I still have the same behaviour:
ip access-list extended pre-auth-acl
permit udp any eq bootps any
permit udp any any eq bootpc
permit udp any eq bootpc any
permit udp any any eq domain
permit tcp any any eq domain
permit ip any host 'ISE_IP_Address'
deny tcp any any eq 80
deny tcp any any eq 443
Is this what you meant?
Thanks again.
Joana.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-29-2014 08:33 PM
Hi Joana,
Were you able to solve this situation? I have the exact same scenario as you (ISE and 5760) and have configured it almost the same way except that i have the authz for CWA a bit different on ISE . I havent had the chance to test it though but i got really confused about 5760 configs...your inputs would help me a lot.
Thanks!
emilio
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-30-2014 01:19 AM
Hi Emilio,
I have been off on holiday so I didn't have time to continue testing. I will let you know once I get any improvement.
Thanks!
Joana.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-03-2016 04:06 AM
Hello Joana,
Did you find any solution?. I also faced the similar issue with 5760 as foreign WLC and 5508 as Anchor WLC. I have tried ACL given by your last post and still no luck.
Highly appreciate any information.
Regards,
Pradeep.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-05-2016 03:00 AM
Hi Pradeep,
My configuration was right from the beginning. I had to upgrade the 5760 Anchor Controller from version 03.03.01SE to version 03.03.04SE to resolve the redirection issue.
Joana
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-24-2014 06:49 PM
I just set this up on a wism2 with anchor. The key was your redirect acl need to be identical on your anchor and foreign controllers. Also match your wlan ssid settings identically except the interface for your foreign which should be your mngt. Good luck and let me know how you make out.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2014 01:18 AM
Hi,
Ok, I will go through the configuration to verify that the configuration is the same for wism2/5760 controllers. How have you configured your redirect acl? I am confused about using deny or permit in the acl entries... I read a lot of documentation and I came across with different redirect acl examples.
Could you share your redirect acls configured on foreign/anchor controllers? It would be very helpful.
Thank you very much.
Joana.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2014 09:15 AM
So this is my redirect ACL.....Like I said its identical on each internal WLC and Anchor.
On Cisco ISE 1.2 our PSN NIC 0 is a (eg. 10.10.10.100) so for Security > Radius we point to 10.10.10.100
On the same PSN NIC 4 is dedicated for Guest Portal on port 8445 and has an ip of 192.168.2.12 hanging off the DMZ
Since the client will talk directly to the ISE Guest Portal the first rule allows TCP to the Portal (192.168.2.12) on port 8445 along with return traffic. Not sure if HTTPS will work since we changed the port number and its neither 443 or 8443. Thats why we choose port number.
Next DHCP and DNS and then deny everything else.
As soon as we connect to our open SSID and try a url we are instantly redirected. Verify on your WLC that your override ACL name appears. Our problem was it showed in the internal but not anchor until we matched them.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-30-2014 01:22 AM
Thank you very much. Really appreciate it! I am going to review my configuration based on your redirect acls. It is good to have an example that is working as a reference. I will let you know how it is going.
Thanks!
Joana.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-30-2014 07:09 AM
Hi,
I am afraid it is still not working for me.... I have tried exactly the same entries in the redirect ACL (change ISE IP address) and I configured it in both foreign/anchor WLC but no difference. I also verified both SSIDs have the same options configured.
I have post some more information about my topology and configuration as an answer to Poonam Garg (up in this discussion thread). I would appreciate if you can have a look and check if there is something that you think might be wrong.
Thanks again.
Joana.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-08-2014 04:10 AM
Hi RyanCoombs,
Sorry to bother you. I was wondering if you can check something for me in your configuration. You already have the same scenario working. I would really appreciate it.
As I said in my previous post, we have the same scenario working completely fine with 3850 foreign controllers rather than wism2. I noticed a difference in the authentication details on ISE. If a client is connecting through wism2 there is no Tunnel Details, it is blank. However, if the client is coming through 3850 wlc the Tunnel Details specify the management VLAN (see below).
A client connecting through 3850 WLC:
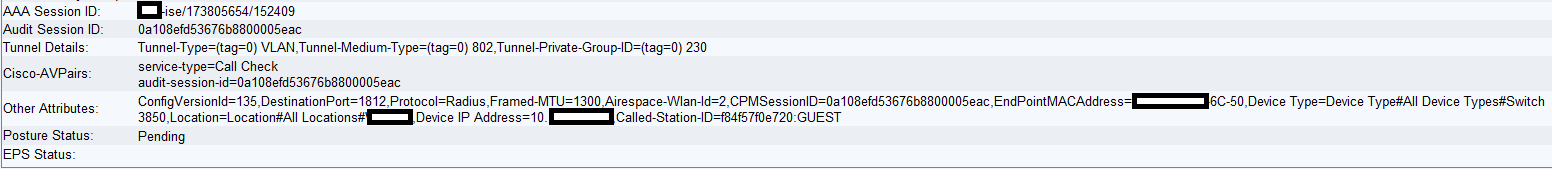
A client connecting through wism2:
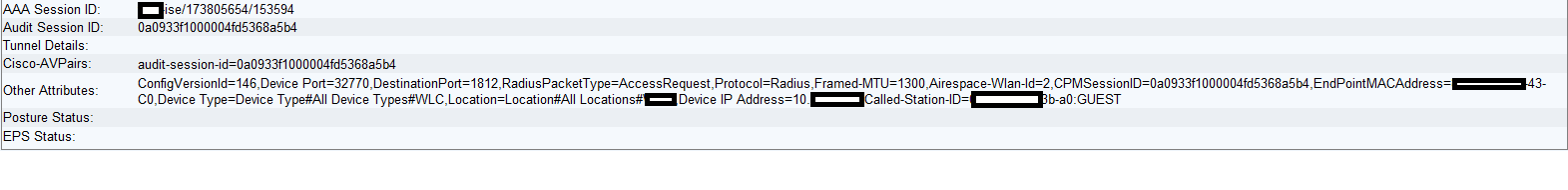
This is the only difference that I can see between the two connections. The management interface in wism2 is untagged, it doesn't have any vlan assigned, just a 0. I am wondering if the management interface in wism2 needs to be assigned to a vlan in order to work, to the native vlan (wism module 6 controller 1 native-vlan 601) or add some additional configuration on ISE?.
Can you please let me know how do you have the management interface configured on wism2?
Are your APs in the same VLAN than the management interface?
I am wondering if it could be a problem of design more than something missed on the configuration.
Thanks a lot!
Joana.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2014 09:59 AM
If you compare the switch redirect ACL and the WLC redirect ACL, you will see the differences. We use the statement deny udp any any eq 53 to stop DNS traffic from being redirected on the switch and on the WLC we use a permit action for DNS traffic. This is because the redirect ACL on the WLC is just a regular wireless ACL. Hence, the ACL rules must have permit statements for allowed traffic flows like DNS and traffic to and from ISE . Any other traffic is caught by the implicit deny statement and is re-directed to the redirect URL set in the ISE. This ACL is invoked when ISE sends the VSA through the authorization profile.Refer Cisco Trustsec How-to Guide-Central Web Authentication
Secondly, Since this web authentication method is Layer 2, you have to be aware that it will be the foreign WLC that does all of the RADIUS work. Only the foreign WLC contacts the ISE, and the redirection ACL must be present on the foreign WLC (In your case its WiSM2).
Can you post your topology
HTH
"Please rate helpful posts"
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide