- Cisco Community
- Technology and Support
- Networking
- Network Management
- Re: Create Firewall Rule to block Ports 2500-3300 (Veeam Backup Traffi
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-23-2022 10:44 AM
Hi,
I want to finally lean how to create a rule on a Cisco ASA GUI interface to block traffic coming from outside to inside of our company that blocks only port range 2500 to 3300 which are the ports used for Veeam Backup. We want to block this so the users working outside of company IP ranges cannot send large amounts of backup data to our company servers.
Is there a good soul that can create this rule and attach a screenshot here together with the answer?
I am a complete noob when it comes to creating rules so please bare with me
Thanks!
Solved! Go to Solution.
- Labels:
-
Network Management
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-27-2022 12:39 AM
Hi,
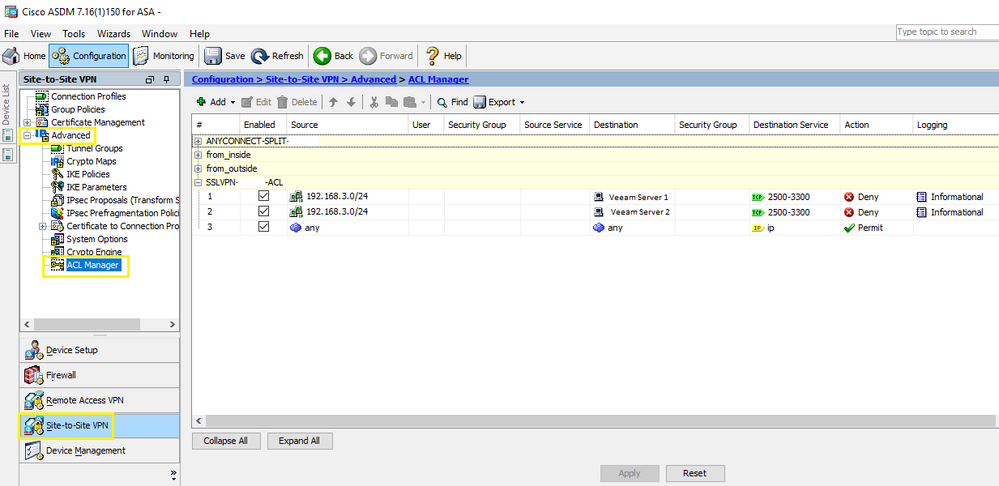
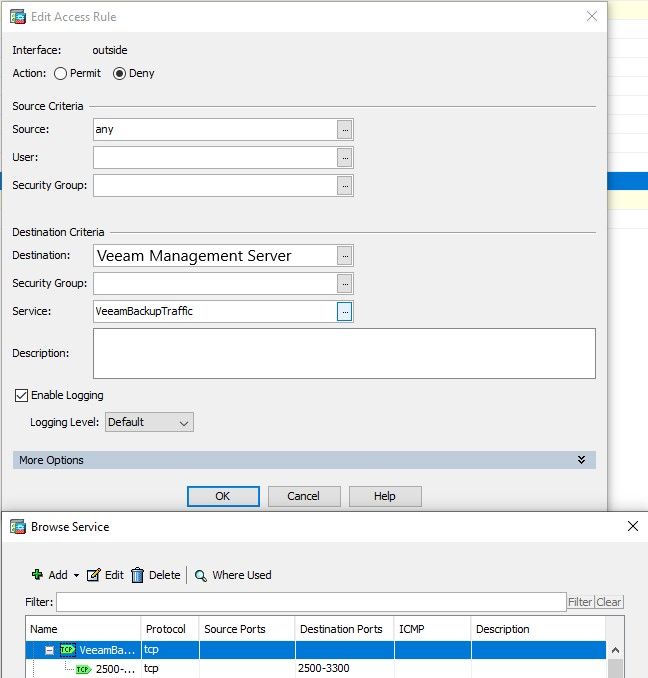
this was the solution to my question, all I needed was a screenshot like this so I can set it up myself:
So the rule will block all traffic on ports 2500-3300 which are being used by Veeam for backup traffic from the 192.168.3.0 which is our VPN subnet.
Best regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-23-2022 11:07 AM
try this way
object service Obj-Ports-Range
service udp/tcp source/destination range 2500 3300
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-23-2022 11:45 AM
Hi MHM,
thank you. I am scared as it is, would like to do it over ASDM Console aka GUI?
BR
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-23-2022 12:19 PM
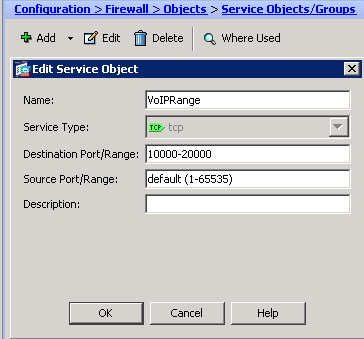
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-23-2022 10:53 PM - edited 06-23-2022 10:54 PM
Hi MHM,
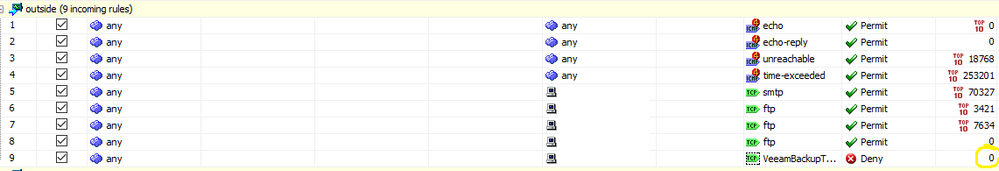
I appreciate you trying to help, but it is too little info for someone who has only the most basic knowledge of firewalls, i am not a pro. I would need this procedure from A to Z with screenshots as I was unable to find something easy on the internet. Could you do this for me please? I have created a rule 10min ago, but I am not sure if this is good:
The rule is set on the last place as a 9th rule with all of the rules having the permit option. Does this need to be changed:
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-23-2022 11:22 PM
Hello,
the rule you created looks good as far as I can tell. Keep in mind though that the order of access rules is important, so make sure to move your rule to the top spot:
"The order of rules is important. When the ASA decides whether to forward or drop a packet, the ASA tests the packet against each rule in the order in which the rules are listed in the applied ACL. After a match is found, no more rules are checked. For example, if you create an access rule at the beginning that explicitly permits all traffic for an interface, no further rules are ever checked."
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-23-2022 11:26 PM
Hi Georg,
thanks for your input. Now i am reading the documentation because i think i have made a mistake. The documentation says the following:
Inbound and Outbound Rules
The ASA supports two types of access rules:
• Inbound—Inbound access rules apply to traffic as it enters an interface. Global access rules are
always inbound.
• Outbound—Outbound access rules apply to traffic as it exits an interface.
I have created an outbound rule - this does not help me as I want to block the ports from outside to inside of the company?
Why does this have to be so hard
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-24-2022 05:49 AM
I don't see any error in your config still do you config PAT for these port ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-24-2022 05:54 AM
Hi MHM,
how do I check this? Will post any screenshot that you tell me to capture.
BR
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-24-2022 06:10 AM
https://www.youtube.com/watch?v=OqBm-jTfUwE
this video how to config NAT keep notice that you must use Service Object (you use in ACL) in NAT also for port-range.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-27-2022 12:39 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-27-2022 05:01 AM
first glad you solve the issue second your original post about port range you don't mention there is VPN.
anyway good job friend.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide