- Cisco Community
- Technology and Support
- Networking
- Network Management
- FTD Deployed configurations are too large
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
FTD Deployed configurations are too large
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-20-2022 02:10 PM
Hi,
I upgraded a pair of 5516-x firewalls to ftd version 7.0.1 and I'm getting the message above. Detail below: I have a very basic setup on these withe very few rules in my policies. I was curious to know if anyone else has run into this issue and How you got out of it. The firewalls are running fine, but I don't like to see messages like this. I was on 6.4.0.14 and all was well.
Thanks
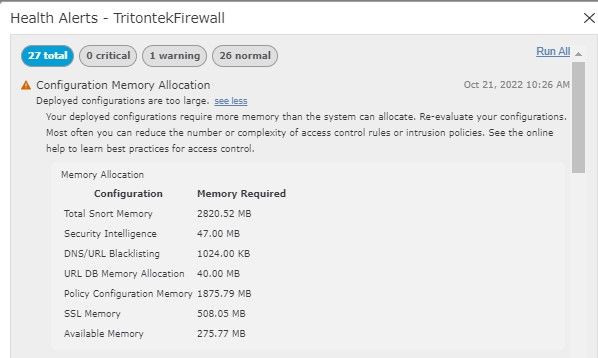
| Total Snort Memory | 2758.80 MB |
| Security Intelligence | 156.00 MB |
| DNS/URL Blacklisting | 19.00 MB |
| Policy Configuration Memory | 2124.66 MB |
| SSL Memory | 0 B |
| Available Memory | 361.92 MB |
- Labels:
-
Network Management
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-20-2022 03:12 PM
for ASA
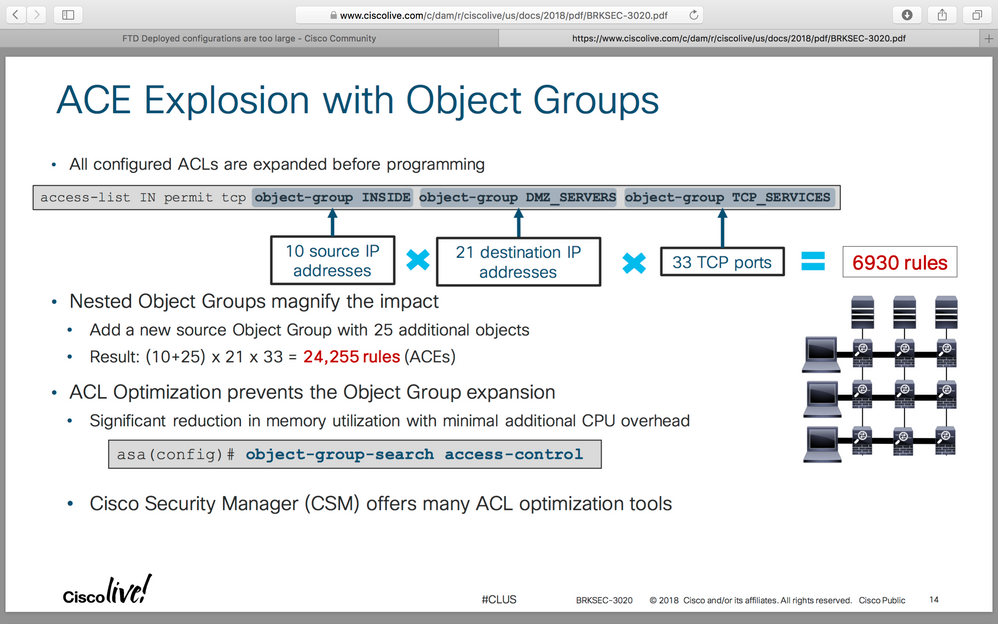
even one simple ACL produce 24,255 rules !!!
there is command for ASA but for FTD I will search and end you command.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-20-2022 03:42 PM
Thank you so much for replying. Yes that's crazy.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-16-2022 08:49 AM
i have the same problem. what was the fix for this one?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-16-2022 09:03 AM
Hello,
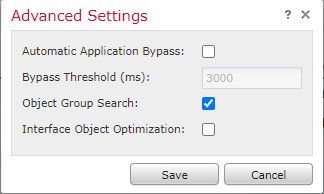
did you try the fix mentioned in the screenshot ?
You can reduce the memory required to search access rules by enabling object group search, but this is at the expense rule lookup performance. When enabled, object group search does not expand network objects, but instead searches access rules for matches based on those group definitions. You can set this option using the object-group-search access-control command.
You can improve system performance and reliability by using the transactional commit model for access groups. See the basic settings chapter in the general operations configuration guide for more information. Use the asp rule-engine transactional-commit access-group command.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-18-2022 10:37 PM
Hi Sir, i am running FTD and my CLI access is limited. would that command still run using the expert mode?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-19-2022 09:26 PM
On FTD managed by FMC you will find the object group search option into the GUI at device management - device properties, I don't know if the same applies for FDM.
Note that object group search reduce memory consumption at the expenses of cpu, if you have a very large rule set with intensive use of objects you may significantly reduce memory consumption but at the same time significantly increase cpu usage.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-20-2022 07:28 PM - edited 10-20-2022 07:48 PM
Hi Sir,
i have enabled the Object Group Search and it seems the error has not gone away (still present) but i will still keep my eye on this issue and will continue to monitor maybe this will be gone in a few. would you also recommend upgrading my Snort 2 to Snort 3? i read some KB about Snort3 is more scalable, flexible and may use lower memory compare to Snort 2. If i ever upgrade my Snort version is there any changes in my config?
Thank you sir
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-20-2022 09:36 PM
Cisco suggests to move to snort3 for efficiency and performance, but I have very few experience about it, I did it in my lab only and noticed not much difference, but it's a lab
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-20-2022 11:32 PM
i will try to upgrade my Snort this coming weekend. one last more question, after upgrading your Snort version did it used too much memory or just the same? Because i have no problem upgrading my Snort version but am bit hesitant if that upgrade would make any good or worsen my problem.
if Snort3 would rather used up more memory than the Snort2 then i rather stay in my current.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-22-2025 06:08 AM
which device model do you have? Did you solve this problem?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-17-2022 01:12 PM
Yes I read this. The ASA is set up as an ASA with a sourcefire module running. Are you saying that applying this command to the ASA will reduce the memory needed, or increase memory available on the Sourcefire module?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-18-2022 12:44 AM
Hello,
good question. Since the ASA and the SFR work in conjunction, reducing the required memory on the ASA should impact the SFR as well. Are there actually (a lot of) (nested) object groups in your ASA config ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-17-2022 09:51 PM
A TAC engineer told me that this is a predictive alarm, based on your current configuration and some unknown traffic profiles you MAY run out of memory the way it explains in the table.
In short it's telling you that you are at risk of being out of memory and you have to start considering upgrading firewall model or disabling some function which consumes memory.
Cleaning access rules and/or enabling object group search is a possible way, but it depend on your environment how much effective it can be.
You can compltely disable the alarm on health policy, it's called "confoguration memory allocation" on 7.x releases, it had a different name in 6.x releases which I can't recall.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide