- Cisco Community
- Technology and Support
- Networking
- Network Management
- How to config Web (80/443) forward on Cisco ISR4331?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-07-2020 10:44 PM - edited 08-07-2020 10:55 PM
Hi all,
I am new to Cisco and trying to do some learning by doing, please advice me on how to go:
- Background:
Our Cisco is provided with following setting:
+ Connection to Internet on Interface Dialer0 and provided with static ip 112.160.15.101
+ Inside Interface for Cisco is: interface GigabitEthernet0/0/1
+ This GigabitEthernet0/0/1 is connected to a Fortigate at 192.168.3.2/10.86.2.3 and route to local lan with 10.86.2.0
+ The local lan 10.86.2.0 is also connected to a Sonicwall interface (X5) 10.86.2.252
+ Our web server is 10.86.19.2 and behind the SonicWall
Routings for Local Nets are fine as I can ping the 192.168.3.1 and 192.168.1.1 from 10.86.19.2 and can access the router 192.168.3.1 using ssh/ telnet. Also from the Cisco router, pinging/ssh/ftp to 10.86.19.2 is working fine.
- Requirement:
I would like to set up port forwarding on 80/443 from the Dialer0 (112.160.15.101) to server 10.86.19.2. I tried many ways with some definitions grabbed from Internet and Cisco Tutorial as below:
2.1 On GigabitEthernet0/0/1 I did
interface GigabitEthernet0/0/1
ip address 192.168.1.1 255.255.255.0 secondary
ip address 192.168.3.1 255.255.255.0
ip nat inside
negotiation auto
spanning-tree portfast disable
2.2 On Dialer0 I did
interface Dialer0
ip address negotiated
ip mtu 1442
ip nat outside
encapsulation ppp
ip tcp adjust-mss 1400
dialer pool 1
ppp authentication pap callin
[Cisco does not allow this line on user and password]
ppp ipcp dns request
2.3 For NAT and routing I did the following
ip nat inside source static 10.86.19.2 112.160.15.101 route-map NAT-MAP-WEBSERVER-X5 extendable
ip nat inside source list 100 interface Dialer0 overload
no ip forward-protocol nd
and
ip route 0.0.0.0 0.0.0.0 Dialer0
ip route 10.86.2.0 255.255.255.0 192.168.3.2
ip route 10.86.19.0 255.255.255.0 10.86.2.3
ip route 10.86.19.0 255.255.255.0 Dialer0
2.4 For Access list I did:
ip access-list extended PORT-FORWARD-WEBSERVER-X5
permit tcp host 112.160.15.101 host 10.86.19.2 eq www
and
access-list 7 permit 10.86.19.0 0.0.0.255
access-list 100 permit ip 10.86.2.0 0.0.0.255 any
!
route-map NAT-MAP-WEBSERVER-X5 permit 10
match ip address PORT-FORWARD-WEBSERVER-X5
However, the port forward/NAT did not work, no connection to HTTP/HTTPS on the 112.160.15.101 worked Please advice me with thanks.
The next question I would like you to help is: "How to stop SSH/Telnet access from internet to the Router at 112.160.15.101 but still accessible from inside?"
Dang Dinh Ngoc - Vietnam
Solved! Go to Solution.
- Labels:
-
Network Management
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-08-2020 12:17 AM - edited 08-08-2020 12:18 AM
Hi,
For routing, you don't actually need the below red statement. Your 10.86.19.0 is behind your SonicWall, but not the behind the Internet.
ip route 0.0.0.0 0.0.0.0 Dialer0 ip route 10.86.2.0 255.255.255.0 192.168.3.2 ip route 10.86.19.0 255.255.255.0 10.86.2.3ip route 10.86.19.0 255.255.255.0 Dialer0
You also don't need route-map for port forwarding. Instead, jsut create two static nat statements for port 80 & 443 is fine.
ip nat inside source static 10.86.19.2 112.160.15.101 route-map NAT-MAP-WEBSERVER-X5 extendablewww
route-map NAT-MAP-WEBSERVER-X5 permit 10
match ip address PORT-FORWARD-WEBSERVER-X5
ip access-list extended PORT-FORWARD-WEBSERVER-X5
permit tcp host 112.160.15.101 host 10.86.19.2 eq
ip nat inside source static tcp 10.86.19.2 80 112.160.15.101 80
ip nat inside source static tcp 10.86.19.2 443 112.160.15.101 443
Verify the nat translation table by 'show ip nat tran'
Pro Inside global Inside local Outside local Outside global tcp 112.160.15.101:80 10.86.19.2:80 --- --- tcp 112.160.15.101:443 10.86.19.2:443 --- ---
2. "How to stop SSH/Telnet access from internet to the Router at 112.160.15.101 but still accessible from inside?"
Apply access list to your line vty 0 15 so that only whitelisted IP addresses could access to your router.
access-list 50 permit 10.86.19.0 0.0.0.255 access-list 50 permit 10.86.2.0 0.0.0.255 access-list 50 permit 192.168.3.0 0.0.0.255 <... your inside networks ...> line vty 0 15 access-class 50 in
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-08-2020 12:17 AM - edited 08-08-2020 12:18 AM
Hi,
For routing, you don't actually need the below red statement. Your 10.86.19.0 is behind your SonicWall, but not the behind the Internet.
ip route 0.0.0.0 0.0.0.0 Dialer0 ip route 10.86.2.0 255.255.255.0 192.168.3.2 ip route 10.86.19.0 255.255.255.0 10.86.2.3ip route 10.86.19.0 255.255.255.0 Dialer0
You also don't need route-map for port forwarding. Instead, jsut create two static nat statements for port 80 & 443 is fine.
ip nat inside source static 10.86.19.2 112.160.15.101 route-map NAT-MAP-WEBSERVER-X5 extendablewww
route-map NAT-MAP-WEBSERVER-X5 permit 10
match ip address PORT-FORWARD-WEBSERVER-X5
ip access-list extended PORT-FORWARD-WEBSERVER-X5
permit tcp host 112.160.15.101 host 10.86.19.2 eq
ip nat inside source static tcp 10.86.19.2 80 112.160.15.101 80
ip nat inside source static tcp 10.86.19.2 443 112.160.15.101 443
Verify the nat translation table by 'show ip nat tran'
Pro Inside global Inside local Outside local Outside global tcp 112.160.15.101:80 10.86.19.2:80 --- --- tcp 112.160.15.101:443 10.86.19.2:443 --- ---
2. "How to stop SSH/Telnet access from internet to the Router at 112.160.15.101 but still accessible from inside?"
Apply access list to your line vty 0 15 so that only whitelisted IP addresses could access to your router.
access-list 50 permit 10.86.19.0 0.0.0.255 access-list 50 permit 10.86.2.0 0.0.0.255 access-list 50 permit 192.168.3.0 0.0.0.255 <... your inside networks ...> line vty 0 15 access-class 50 in
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-08-2020 12:48 AM - edited 08-08-2020 01:13 AM
Thank ngkin2010,
I did the revisions as you guided (in fact I have done this following cisco recomendation on NAT/PAT and static NAT). But I dont really know it still does not work. Below Telnet said that connection refuse. Initially Web UI is on and I tried to disabled https via Web ui and tried to define a NAT rule using Web ui and it failed as well. Please advise me a bit further
Telnet 112.160.15.101 443 ... connection refused
... ! multilink bundle-name authenticated ! ! bridge irb ! interface GigabitEthernet0/0/0 no ip address ip nat outside negotiation auto pppoe enable group global pppoe-client dial-pool-number 1 ! interface GigabitEthernet0/0/1 ip address 192.168.1.1 255.255.255.0 secondary ip address 192.168.3.1 255.255.255.0 ip nat inside negotiation auto spanning-tree portfast disable ! interface GigabitEthernet0/0/2 no ip address shutdown negotiation auto ! interface Serial0/1/0 no ip address shutdown ! interface GigabitEthernet0 vrf forwarding Mgmt-intf no ip address shutdown negotiation auto ! interface Dialer0 ip address negotiated ip mtu 1442 ip nat outside ip access-group NOSPOOF in encapsulation ppp ip tcp adjust-mss 1400 dialer pool 1 ppp authentication pap callin <<Connection variable, obmited>> ppp ipcp dns request ! ip nat inside source static tcp 10.86.19.2 80 112.160.15.101 80 extendable ip nat inside source static tcp 10.86.19.2 443 112.160.15.101 443 extendable ip nat inside source list 100 interface Dialer0 overload no ip forward-protocol nd ! no ip http server no ip http secure-server ip route 0.0.0.0 0.0.0.0 Dialer0 ip route 10.86.2.0 255.255.255.0 192.168.3.2 ip route 10.86.19.0 255.255.255.0 10.86.2.3 ! access-list 100 permit ip 10.86.2.0 0.0.0.255 any ! ! end
Any reason with the following?, I removed and still dont work
bridge irb
the show ip nat trans is:
Pro Inside global Inside local Outside local Outside global
tcp 113.160.5.101:443 10.86.19.2:443 --- ---
tcp 113.160.15.101:80 10.86.19.2:80 --- ---
I found this sharing https://community.cisco.com/t5/switching/static-nat-not-working/td-p/736310#
It might be a case as my Router is using for:
+ Allowing 10.0.0.0 to access internet; and
+ Allowing the internet user to access web services as described before.
So I tried this:
<<External IP>>Routed/NAT to <<secondary IP 192.168.1.1>>Routed/NAT to <<10.86.19.2>>
in stead of route/NAT directly:
<<External IP>>Routed/NAT to <<10.86.19.2>>
It sounds a bit logical as from the router, I can access the web-server inside with ftp/ssh/ping but still do not work... Haiz.
Thank you for your support
Ngoc
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-08-2020 01:41 AM
You've mentioned that the connection was refused (Telnet 112.160.15.101 443 ... connection refused), but I am wonder it's refused by who.
Applying source NAT on router might help as your firewalls (FortiGate & SonicWall) might block the connection from External IP address. So you should have a check on both firewalls as well.
There is few scenarios for your case, and it's easy to figure it out if you have access to all of your devices (Router, FortiGate, SonicWall).
Scenario 1: NAT is not working as expected due to whatever reason.
In this scenario, NAT is not working. Your router has pick up the incoming connection (113.160.5.101:443), and refused the connection due to 'no ip http server'. If that is the case, there should have no related traffic flow through the FortiGate and SonicWall. Try to view the traffic log / perform packet capture to confirm it.
Scenario 2: NAT is working, but traffic is refused by FortiGate.
In this scenario, your traffic should already flow through your router and forwarded to FortiGate. Check on the traffic log to see whether it's passed or not.
Scenario 3: NAT is working, traffic has passed FortiGate, but it's refused by SonicWall.
In this scenario, check on the traffic log on SonicWall to see whether it's passed or not.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-08-2020 02:34 AM - edited 08-08-2020 03:02 AM
Thank you very much for your attention,
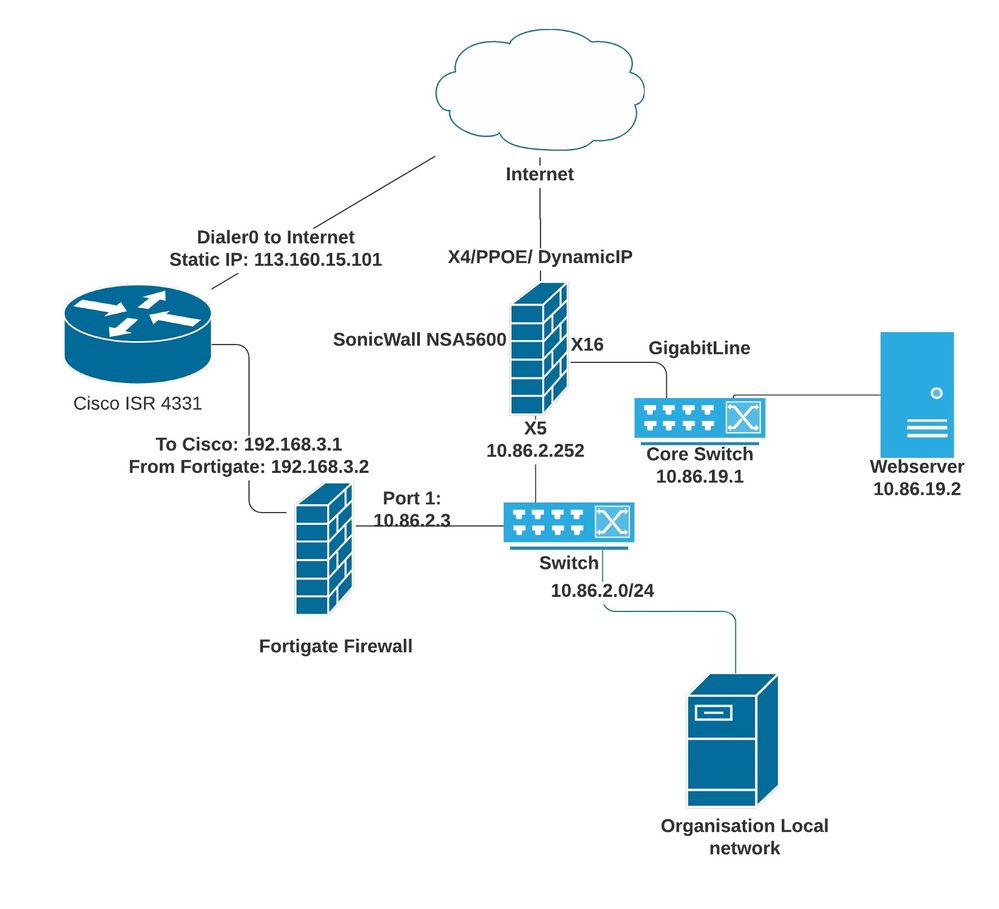
To help you understand our network, please see the diagram below:
All internal routes was working fine.
Connection from Fortigate, Cisco to Soniwal and to web server (CentOS) were fine with telnet/ssh/ping/ftp.
But connection from outside to IP 113.160.15.101 failed over 80/443 port with telnet.
Please help!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-08-2020 06:01 AM - edited 08-08-2020 06:06 AM
Dear James (ngkin2010),
It is my great thank to your support for fixing the issue. In fact, I have no experience at all with those networking stuff and your guidance during site support was gorgeous and bright me up a lot.
You have just supported half million of vulnerable people in Caobang to have stable access to their system and they will be able to raise their concerns requesting local government supports at any time and almost at any circumstances.
Please accept my and our great thanks to your entire work.
I am not a real technical staff at networking but in the situation of shortage of professional staff at a remote province, this helps is so much valuable.
Again, thank you for your work and hope you will gain great success in the future as a sincere and wholehearted person for community. Thank Cisco to enable me meeting with such a beautiful supporting community.
Best regards,
Dang Dinh Ngoc - from Vietnam
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-08-2020 02:40 AM
I have connection through all of them and following is the check:
Scenario 3 (I sit on terminal of fortigate) : from: Fortigate >> Soniwall >> Server: telnet 10.86.19.2 80/443 work
Scenario 2 (I sit on Cisco SSH): From Cisco directly to 10.86.18.2: telnet 10.86.19.2 80/443 work
But from internet telnet the External Ip on cisco 113.... refused! So I doubt there is somethings on Access rule on Cisco as on Fortigate and Sonicwall I allow all connection into Web Server
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide