- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: Active standby failure
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Active standby failure
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-06-2020 02:33 AM
Hi,
I have asa deployed active standby .
In my standby I don't have connectivity to DMZ interface due to lack of budget .
Now the problem is , it shows active standby failure . Is it due to the missing connectivity
or something else
?
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-06-2020 04:37 AM
The command "show failover" will tell you the reason the Standby unit is marked failed.
If it is only because of an interface you expect to not come up then you can remove that interface from failover monitoring and it will not affect the failover pair state.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-28-2020 03:06 AM
Hi ,
here is the failover result . but i dont kmow the reason . Please help
sh failover
Failover On
Failover unit Primary
Failover LAN Interface: FW-Failover GigabitEthernet0/6 (up)
Unit Poll frequency 1 seconds, holdtime 15 seconds
Interface Poll frequency 5 seconds, holdtime 25 seconds
Interface Policy 1
Monitored Interfaces 4 of 1025 maximum
MAC Address Move Notification Interval not set
failover replication http
Version: Ours 9.2(4)27, Mate 9.2(4)27
Last Failover at: 15:07:53 MSK May 3 2020
This host: Primary - Active
Active time: 10787760 (sec)
slot 0: ASA5585-SSP-20 hw/sw rev (3.0/9.2(4)27) status (Up Sys)
Interface Outside (OUTSIDE-IP): Normal (Waiting)
Interface DMZ1 (172.16.5.1): Normal (Waiting)
Interface Inside (172.16.3.1): Normal (Waiting)
Interface DMZ2 (172.16.6.1): Normal (Waiting)
slot 1: ASA5585-NM-4-10GE hw/sw rev (1.0/) status (Up)
slot 2: empty
Other host: Secondary - Failed
Active time: 897 (sec)
slot 0: ASA5585-SSP-20 hw/sw rev (3.0/9.2(4)27) status (Up Sys)
Interface Outside (0.0.0.0): Normal (Waiting)
Interface DMZ1 (172.16.5.2): Normal (Waiting)
Interface Inside (172.16.3.2): Normal (Waiting)
Interface DMZ2 (172.16.6.2): No Link (Waiting)
slot 1: ASA5585-NM-4-10GE hw/sw rev (1.0/) status (Up)
slot 2: empty
Stateful Failover Logical Update Statistics
Link : FW-Failover GigabitEthernet0/6 (up)
Stateful Obj xmit xerr rcv rerr
General 2688694275 0 2828542 0
sys cmd 2539556 0 2539554 0
up time 0 0 0 0
RPC services 0 0 0 0
TCP conn 1825689955 0 194589 0
UDP conn 809062791 0 88688 0
ARP tbl 48431735 0 5646 0
Xlate_Timeout 0 0 0 0
IPv6 ND tbl 0 0 0 0
VPN IKEv1 SA 1135 0 4 0
VPN IKEv1 P2 15367 0 7 0
VPN IKEv2 SA 126290 0 0 0
VPN IKEv2 P2 4645 0 0 0
VPN CTCP upd 0 0 0 0
VPN SDI upd 0 0 0 0
VPN DHCP upd 0 0 0 0
SIP Session 2801048 0 11 0
Route Session 3001 0 28 0
Router ID 0 0 0 0
User-Identity 18752 0 15 0
CTS SGTNAME 0 0 0 0
CTS PAC 0 0 0 0
TrustSec-SXP 0 0 0 0
IPv6 Route 0 0 0 0
STS Table 0 0 0 0
Logical Update Queue Information
Cur Max Total
Recv Q: 0 23 2830358
Xmit Q: 0 120 2713687577
FW#
FW# write
Building configuration...
Cryptochecksum: 5d2ea11b 29524c5e 8d5845c9 6258bb36
126887 bytes copied in 1.260 secs (126887 bytes/sec)
[OK]
FW# sh fa
FW# sh failover h
FW# sh failover history
==========================================================================
From State To State Reason
==========================================================================
08:05:43 MSK Jan 7 2020
Failed Standby Ready Interface check
08:05:54 MSK Jan 7 2020
Standby Ready Just Active Other unit wants me Active
08:05:54 MSK Jan 7 2020
Just Active Active Drain Other unit wants me Active
08:05:54 MSK Jan 7 2020
Active Drain Active Applying Config Other unit wants me Active
08:05:54 MSK Jan 7 2020
Active Applying Config Active Config Applied Other unit wants me Active
08:05:54 MSK Jan 7 2020
Active Config Applied Active Other unit wants me Active
14:51:20 MSK May 3 2020
Active Failed Interface check
14:51:30 MSK May 3 2020
Failed Standby Ready Interface check
14:51:38 MSK May 3 2020
Standby Ready Just Active Other unit wants me Active
14:51:38 MSK May 3 2020
Just Active Active Drain Other unit wants me Active
14:51:38 MSK May 3 2020
Active Drain Active Applying Config Other unit wants me Active
14:51:38 MSK May 3 2020
Active Applying Config Active Config Applied Other unit wants me Active
14:51:38 MSK May 3 2020
Active Config Applied Active Other unit wants me Active
14:52:55 MSK May 3 2020
Active Failed Interface check
15:07:45 MSK May 3 2020
Failed Standby Ready Interface check
15:07:53 MSK May 3 2020
Standby Ready Just Active Other unit wants me Active
15:07:53 MSK May 3 2020
Just Active Active Drain Other unit wants me Active
15:07:53 MSK May 3 2020
Active Drain Active Applying Config Other unit wants me Active
15:07:53 MSK May 3 2020
Active Applying Config Active Config Applied Other unit wants me Active
15:07:53 MSK May 3 2020
Active Config Applied Active Other unit wants me Active
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-28-2020 05:34 AM
The reason is due to no link on monitored interface DMZ2:
Interface DMZ2 (172.16.6.2): No Link (Waiting)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-08-2020 03:41 PM
If I just add a switch (there is no uplink for the switch ) and connect the interface to the switch , does it will work ?
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-08-2020 07:47 PM
Yes that would work.
Or you could just exclude the DMZ interface from failover monitoring.
One line config change vs install new hardware - whichever you prefer.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-06-2020 03:12 AM
Hi,
I tried to install new hardware ,but after couple of minutes asa complaining no link
What could be the reason
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-06-2020 03:46 AM
You're not giving enough information to give you a useful reply.
Are both ASAs connected to the new hardware? Are their DMZ interfaces both up and in the same VLAN? Have you configured a standby address for the DMZ interface?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-06-2020 04:13 AM
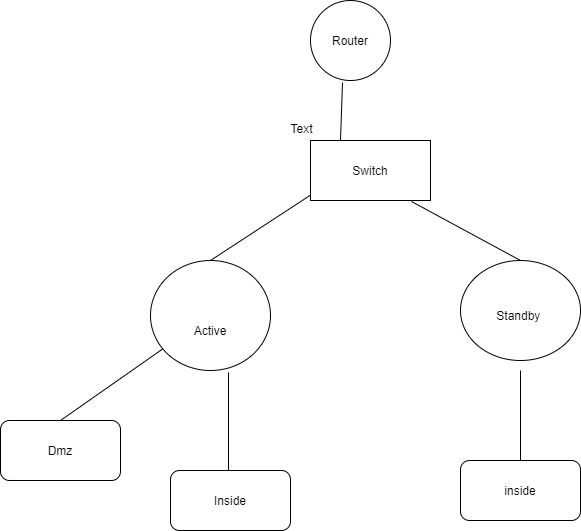
Hi,
Below is the topology diagram . Secondary asa I don't have connectivity to the DMZ switch since it is geographically far from the dmz switch . .
(there are multiple dmz zone but in the diagram I Showed only one . other dmz has identical configuration for both location )
So I thought of putting a dummy l2 switch in the secondary location .
ASa standby ip address configured on standby ASA
Hope this information is enough
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-06-2020 04:44 AM
If the Active ASA cannot reach the configured standby address for the DMZ on the Standby ASA, failover monitoring will show the Standby unit has failed (assuming default monitoring config).
Why do you want to monitor that interface if there's nothing "real" connected to it? Any result you get will be misleading at best.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-07-2020 07:44 AM
But with not active DMZ interface on the Secondary, any hosts in the DMZ will not be accessible. The Secondary needs layer 1 and layer 2 connection to the DMZ vlan/switch to function correctly.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-07-2020 12:14 PM
just to add what other said. you can give a command show failover history
the reason you cant the see DMZ could be layer 2 (vlan) issue.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide