- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: Allowing External Traffic on Cisco ASA
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-17-2019 08:06 AM - edited 02-21-2020 08:40 AM
Hi - I have a Cisco ASA and I'm really struggling with something very simple. I have an outside interface and I would like to allow traffic to hit the outside interface on TCP Port 81 and get NAT'd to a private IP on a webserver. I believe I have the NAT piece of the equation solved but the ACL is processed first and I can't figure out the ACL for the life of me. Here's what I have:
On the outside interface, I created an incoming rule with any source, any destination and a service of TCP Port 81. However, when I run a Packet Tracer from any public IP to the IP of the outside interface on Port 81 the packet is dropped via an implicit rule.
I'm running ASA 9.9, thoughts?
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-22-2019 06:17 AM
you have not change the nat rules put in this order
no nat (inside,outside) source static SERVER interface service CUSTOM80 CUSTOM81
nat (inside,outside) source static SERVER interface service CUSTOM81 CUSTOM80
!
no access-list outside_access_in extended permit tcp any object SERVER eq 80
access-list outside_access_in extended permit tcp any object SERVER eq 81
access-group outside_access_in in interface outside
!
packet-tracer input outside tcp 8.8.8.8 81 96.89.224.197 80
====================================================================
This is the config you just put them earlier change them as describe above. I test them in lab enviroment you should be ok now.
Manual NAT Policies (Section 1)
1 (inside) to (outside) source static Utility1 interface service CUSTOM80 CUSTOM81
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-17-2019 08:43 AM
Not 100% sure of your exact configuration, but you would specify the real IP address and port in the ACL. See example:-
object nat SRV1
host 10.2.2.5
nat (inside,outside) static 96.89.224.197 service tcp 80 81
access-list OUTSIDE_IN permit tcp any host 10.2.2.5 eq 80
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-17-2019 09:05 AM
You need this.
object network SERVER
host 10.2.2.5
nat (inside,outside) static interface service tcp 80 81
!
access-list outside_in permit tcp any host 10.2.2.5 eq 80
access-group outside_in in interface outside
!
packet tracer input outside tcp 8.8.8.8 1234 10.2.2.5 eq 81
!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-17-2019 10:46 AM
So, unfortunately I'm having trouble with the NAT statement you suggested. I think via my Googling I've found that 8.3+ requires a new NAT format and syntax. Here is what I typed to try to get it as close to yours as possible:
nat (inside,outside) source static any interface service Port80 Port81
I had to create Service Objects as it wouldn't let me specify the port explicitly. I also had to add the source parameter before the word static.
Unfortunately, even with this command and the the access-list/access-group commands I still get dropped packets via an implicit rule.
Config snippets:
nat (inside,outside) source static any any destination static NETWORK_OBJ_10.1.2.0_26 NETWORK_OBJ_10.1.2.0_26 no-proxy-arp route-lookup
nat (inside,outside) source dynamic obj_any interface
nat (wlan,outside) source dynamic obj_any interface
nat (inside,outside) source static any interface service Port80 Port81
object service Port80
service tcp source eq www destination eq www
object service Port81
service tcp destination eq 81
access-list outside_in extended permit tcp any host 10.1.1.79 eq www
access-group outside_access_out out interface outside
access-group inside_access_in_1 in interface inside
access-group inside_access_out_1 out interface inside
access-group wlan_access_in_1 in interface wlan
access-group wlan_access_out out interface wlan
I've attached the entire config file if that would be more helpful.
Thanks!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-17-2019 11:21 AM - edited 01-17-2019 12:37 PM
You've defined your nat statement globally, rather than under the object "Utility1", the ACL is also wrong, you need to reference the real port not the natted port. Example:-
object network Utility1
host 10.1.1.79
nat (INSIDE,OUTSIDE) static interface service tcp www 81
access-list outside_access_in extended permit tcp any object Utility1 eq 80
You don't have an access-group inbound on the outside interface. E.g-
"access-group outside_access_in in interface outside"
Remove the old configuration:-
no access-list outside_access_in extended permit tcp any host 10.1.1.79 range 81 81
no nat (inside,outside) source static any interface service Port80 Port81
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-17-2019 11:48 AM - edited 01-17-2019 11:49 AM
@Rob Ingram
is that typo error
access-list outside_access_in extended permit tcp any object Utility1 10.1.1.79 eq 80
<-------------->
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-17-2019 12:38 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-18-2019 11:49 AM
Hi - Unfortunately that didn't seem to make a difference. My packet-tracer still fails with an implicit rule drop.
Here are the snippets from my config:
object network Utility1
host 10.1.1.79
access-list outside_access_in extended permit tcp any object Utility1 eq www
object network Utility1
nat (inside,outside) static interface service tcp www 81
access-group outside_access_in in interface outside
Thoughts?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-18-2019 11:54 AM
My guess is possibly there is another NAT rule above the new NAT rule which it is matching against and therefore failing.
You could also run "show nat" and check the output
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-18-2019 11:57 AM
Hey - Below is my show NAT and the packet tracer output. Thanks again for all of the help!
ciscoasa(config)# show nat
Manual NAT Policies (Section 1)
1 (inside) to (outside) source static any any destination static NETWORK_OBJ_10.1.2.0_26 NETWORK_OBJ_10.1.2.0_26 no-proxy-arp route-lookup
translate_hits = 818, untranslate_hits = 881
2 (inside) to (outside) source dynamic obj_any interface
translate_hits = 292844, untranslate_hits = 14867
3 (wlan) to (outside) source dynamic obj_any interface
translate_hits = 4092438, untranslate_hits = 308198
Auto NAT Policies (Section 2)
1 (inside) to (outside) source static Utility1 interface service tcp www 81
translate_hits = 0, untranslate_hits = 0
2 (any) to (outside) source dynamic obj_any interface
translate_hits = 15869, untranslate_hits = 0
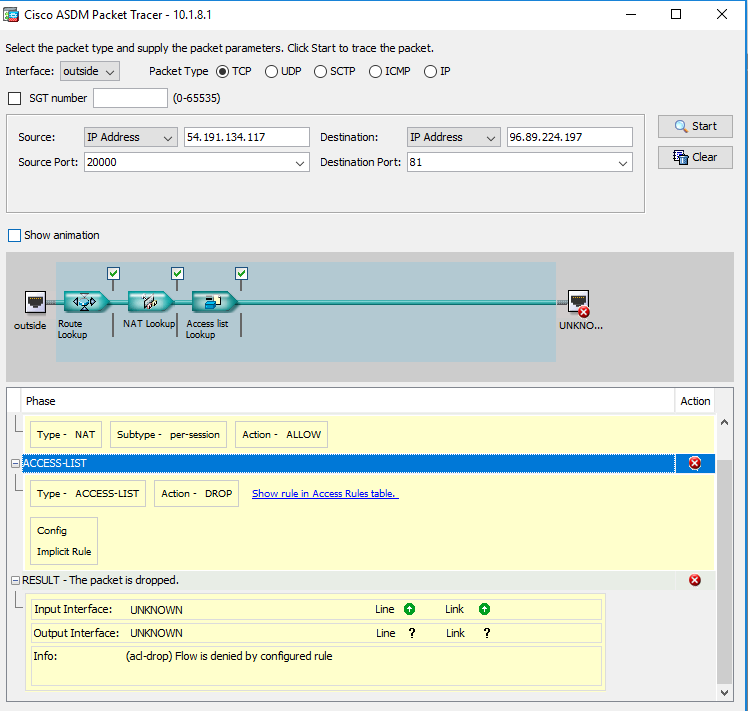
ciscoasa# packet-tracer input outside tcp 8.8.8.8 1234 10.1.1.79 81
Phase: 1
Type: ROUTE-LOOKUP
Subtype: Resolve Egress Interface
Result: ALLOW
Config:
Additional Information:
found next-hop 10.1.1.79 using egress ifc inside
Phase: 2
Type: ACCESS-LIST
Subtype:
Result: DROP
Config:
Implicit Rule
Additional Information:
Result:
input-interface: outside
input-status: up
input-line-status: up
output-interface: inside
output-status: up
output-line-status: up
Action: drop
Drop-reason: (acl-drop) Flow is denied by configured rule
ciscoasa#
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-18-2019 12:01 PM
It's probably being natted on this rule:-
Manual NAT Policies (Section 1)
1 (inside) to (outside) source static any any destination static NETWORK_OBJ_10.1.2.0_26 NETWORK_OBJ_10.1.2.0_26 no-proxy-arp route-lookup
translate_hits = 818, untranslate_hits = 881
2 (inside) to (outside) source dynamic obj_any interface
translate_hits = 292844, untranslate_hits = 14867
which would be processed before the new nat rule
Auto NAT Policies (Section 2)
1 (inside) to (outside) source static Utility1 interface service tcp www 81
translate_hits = 0, untranslate_hits = 0
Try removing the Manual NAT rule #2, and configure a global nat rule that would be processed after the Auto NAT rules, this would move the rule to Section 3. e.g:-
nat (INSIDE,OUTSIDE) after-auto source dynamic obj_any interface interface
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-18-2019 12:03 PM
corret if you apply these it will work and fix your issue
object network SERVER
host 10.1.1.79
!
nat (inside,outside) 1 source static SERVER interface service Port80 Port81
!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-18-2019 12:04 PM
@Rob Ingramwhy you putting the rule in section 3. it should be in section 1.
object network SERVER
host 10.1.1.79
!
nat (inside,outside) 1 source static SERVER interface service Port80 Port81
!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-18-2019 01:40 PM
Unfortunately, neither of the new NAT rules worked using the after-auto or "1" command to specify the order. I still get the same results of a dropped packet via an implicit rule. I also don't see any hits on the NAT rule or ACL. It's my understanding that the ACL is processed before the NAT rule so I'm wondering if that's where the issue resides...there has to be something I'm missing though...
Updated NAT table and packet-tracer below:
ciscoasa# show nat
Manual NAT Policies (Section 1)
1 (inside) to (outside) source static any any destination static NETWORK_OBJ_10.1.2.0_26 NETWORK_OBJ_10.1.2.0_26 no-proxy-arp route-lookup
translate_hits = 818, untranslate_hits = 881
2 (wlan) to (outside) source dynamic obj_any interface
translate_hits = 4103849, untranslate_hits = 314450
Auto NAT Policies (Section 2)
1 (inside) to (outside) source static Utility1 interface service tcp www 81
translate_hits = 0, untranslate_hits = 0
2 (any) to (outside) source dynamic obj_any interface
translate_hits = 15919, untranslate_hits = 4
Manual NAT Policies (Section 3)
1 (inside) to (outside) source dynamic obj_any interface
translate_hits = 0, untranslate_hits = 0
ciscoasa# packet-tracer input outside tcp 8.8.8.8 1234 10.1.1.79 81
Phase: 1
Type: ROUTE-LOOKUP
Subtype: Resolve Egress Interface
Result: ALLOW
Config:
Additional Information:
found next-hop 10.1.1.79 using egress ifc inside
Phase: 2
Type: ACCESS-LIST
Subtype:
Result: DROP
Config:
Implicit Rule
Additional Information:
Result:
input-interface: outside
input-status: up
input-line-status: up
output-interface: inside
output-status: up
output-line-status: up
Action: drop
Drop-reason: (acl-drop) Flow is denied by configured rule
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-18-2019 02:04 PM
Did you actually test accessing the server over the internet?
Can you provide the updated configuration acl, nat, objects etc.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide