- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: Allowing External Traffic on Cisco ASA
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-17-2019 08:06 AM - edited 02-21-2020 08:40 AM
Hi - I have a Cisco ASA and I'm really struggling with something very simple. I have an outside interface and I would like to allow traffic to hit the outside interface on TCP Port 81 and get NAT'd to a private IP on a webserver. I believe I have the NAT piece of the equation solved but the ACL is processed first and I can't figure out the ACL for the life of me. Here's what I have:
On the outside interface, I created an incoming rule with any source, any destination and a service of TCP Port 81. However, when I run a Packet Tracer from any public IP to the IP of the outside interface on Port 81 the packet is dropped via an implicit rule.
I'm running ASA 9.9, thoughts?
Solved! Go to Solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-17-2019 11:30 AM - edited 01-17-2019 11:46 AM
can you test this.
object network SERVER
host 10.1.1.79
!
nat (inside,outside) 1 source static SERVER interface service Port80 Port81
!
no access-list outside_access_in extended permit tcp any host 10.1.1.79 range 81 81
no nat (inside,outside) source static any interface service Port80 Port81
!
access-list outside_access_in extended permit tcp any object SERVER eq 80
access-group outside_access_in in interface outside
!
(OR)
as i stated in my earlier post
object network SERVER
host 10.1.1.79
nat (inside,outside) static interface service tcp 80 81
!
access-list outside_in permit tcp any host 10.1.1.79 eq 80
access-group outside_in in interface outside
!
no access-list outside_access_in extended permit tcp any host 10.1.1.79 range 81 81
no nat (inside,outside) source static any interface service Port80 Port81
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-18-2019 11:58 AM - edited 01-18-2019 12:00 PM
object network SERVER
host 10.1.1.79
!
nat (inside,outside) 1 source static SERVER interface service Port80 Port81
!
no access-list outside_access_in extended permit tcp any host 10.1.1.79 range 81 81
no nat (inside,outside) source static any interface service Port80 Port81
Apply these config as mentioned above it will work
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-18-2019 03:13 PM - edited 01-19-2019 03:53 AM
I have lab this up. your configuration were wrong. here is the right configuration.
object network SERVER
host 10.1.1.79
!
object service CUSTOM80
service tcp source eq 80
!
object service CUSTOM81
service tcp source eq 81
!
nat (inside,outside) source static SERVER interface service CUSTOM80 CUSTOM81
!
access-list outside_access_in extended permit tcp any object SERVER eq 80
access-group outside_access_in in interface outside
!
packet-tracer input outside tcp 8.8.8.8 1234 96.89.224.197 81
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-21-2019 04:47 AM
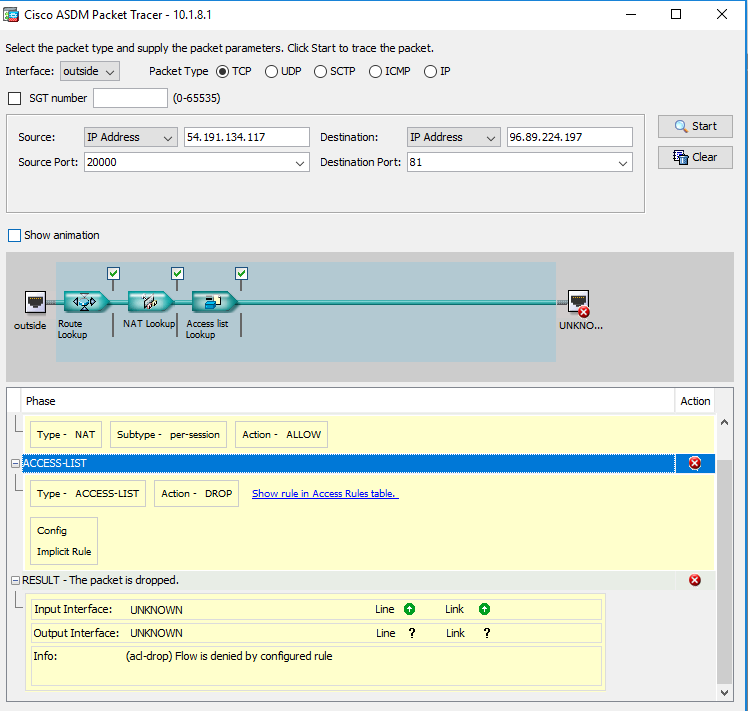
Hi - I appreciate the help. Unfortunately, this didn't seem to work either. Although, this time the packet-tracer hits the NAT and gets through it but is stopped by the ACL. I've also re-attached the config.
ciscoasa# packet-tracer input outside tcp 8.8.8.8 1234 96.89.224.197 81
Phase: 1
Type: ROUTE-LOOKUP
Subtype: Resolve Egress Interface
Result: ALLOW
Config:
Additional Information:
found next-hop 96.89.224.197 using egress ifc identity
Phase: 2
Type: NAT
Subtype: per-session
Result: ALLOW
Config:
Additional Information:
Phase: 3
Type: ACCESS-LIST
Subtype:
Result: DROP
Config:
Implicit Rule
Additional Information:
Result:
input-interface: outside
input-status: up
input-line-status: up
output-interface: NP Identity Ifc
Action: drop
Drop-reason: (acl-drop) Flow is denied by configured rule
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-21-2019 05:04 AM - edited 01-21-2019 05:05 AM
can you try this and give us the output. the reason i said in our access-list we allow www (80) not 81
ciscoasa# packet-tracer input outside tcp 8.8.8.8 1234 96.89.224.197 80
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-21-2019 05:06 AM
See below:
ciscoasa(config)# packet-tracer input outside tcp 8.8.8.8 1234 96.89.224.197 80
Phase: 1
Type: ROUTE-LOOKUP
Subtype: Resolve Egress Interface
Result: ALLOW
Config:
Additional Information:
found next-hop 96.89.224.197 using egress ifc identity
Phase: 2
Type: NAT
Subtype: per-session
Result: ALLOW
Config:
Additional Information:
Phase: 3
Type: ACCESS-LIST
Subtype:
Result: DROP
Config:
Implicit Rule
Additional Information:
Result:
input-interface: outside
input-status: up
input-line-status: up
output-interface: NP Identity Ifc
Action: drop
Drop-reason: (acl-drop) Flow is denied by configured rule
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-21-2019 05:13 AM
I can reach you on your public ip address 96.89.224.197 80
!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-21-2019 05:19 AM
Hey - Yea, but I think that is https, not http. If I'm in a browser and go to https I'm able to login to AnyConnect. However, if I go on http port 80 I don't get AnyConnect or the website I'm expecting. I also don't get anything when I browse on http port 81.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-21-2019 06:12 AM
can you take these rules off and test it. by taking these rule off will not impact/discount your session.
!
no access-list inside_access_in_1 extended permit object-group DM_INLINE_PROTOCOL_2 any
no access-list inside_access_out_1 extended permit object-group DM_INLINE_PROTOCOL_3 any any
no access-group outside_access_out out interface outside
no access-group inside_access_in_1 in interface inside
!
packet tracert 8.8.8.8 12345 x.x.x.x.x 80 det
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-21-2019 06:33 AM
Looks like it's still dropped by the ACL:
ciscoasa# packet-tracer input outside tcp 8.8.8.8 1234 96.89.224.197 80
Phase: 1
Type: ROUTE-LOOKUP
Subtype: Resolve Egress Interface
Result: ALLOW
Config:
Additional Information:
found next-hop 96.89.224.197 using egress ifc identity
Phase: 2
Type: NAT
Subtype: per-session
Result: ALLOW
Config:
Additional Information:
Phase: 3
Type: ACCESS-LIST
Subtype:
Result: DROP
Config:
Implicit Rule
Additional Information:
Result:
input-interface: outside
input-status: up
input-line-status: up
output-interface: NP Identity Ifc
Action: drop
Drop-reason: (acl-drop) Flow is denied by configured rule
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-21-2019 04:38 PM
sorry for get back late. I did look into this and test this. take the old rules off and apply theses one
!
object network SERVER
host 10.1.1.79
!
object service CUSTOM80
service tcp source eq 80
!
object service CUSTOM81
service tcp source eq 81
!
no nat (inside,outside) source static SERVER interface service CUSTOM80 CUSTOM81
nat (inside,outside) source static SERVER interface service CUSTOM81 CUSTOM80
!
no access-list outside_access_in extended permit tcp any object SERVER eq 80
access-list outside_access_in extended permit tcp any object SERVER eq 81
access-group outside_access_in in interface outside
!
packet-tracer input outside tcp 8.8.8.8 81 96.89.224.197 80
!
please let me know if any issue. I have tested these rule and they working.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-22-2019 05:55 AM
Hi - Unfortunately it still doesn't work. I've attached the latest packet tracer below. I also tried flipping the NAT policies like we talk about yesterday but no luck.
ciscoasa(config)# packet-tracer input outside tcp 8.8.8.8 81 96.89.224.197 80
Phase: 1
Type: ROUTE-LOOKUP
Subtype: Resolve Egress Interface
Result: ALLOW
Config:
Additional Information:
found next-hop 96.89.224.197 using egress ifc identity
Phase: 2
Type: NAT
Subtype: per-session
Result: ALLOW
Config:
Additional Information:
Phase: 3
Type: ACCESS-LIST
Subtype:
Result: DROP
Config:
Implicit Rule
Additional Information:
Result:
input-interface: outside
ciscoasa(config)# show nat
Manual NAT Policies (Section 1)
1 (inside) to (outside) source static Utility1 interface service CUSTOM80 CUSTOM81
translate_hits = 0, untranslate_hits = 0
2 (wlan) to (outside) source dynamic obj_any interface
translate_hits = 4143583, untranslate_hits = 365981
3 (inside) to (outside) source static any any destination static NETWORK_OBJ_10.1.2.0_26 NETWORK_OBJ_10.1.2.0_26 no-proxy-arp route-lookup
translate_hits = 0, untranslate_hits = 0
Auto NAT Policies (Section 2)
1 (any) to (outside) source dynamic obj_any interface
translate_hits = 48275, untranslate_hits = 3822
Manual NAT Policies (Section 3)
1 (inside) to (outside) source dynamic obj_any interface
translate_hits = 0, untranslate_hits = 0
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-22-2019 06:17 AM
you have not change the nat rules put in this order
no nat (inside,outside) source static SERVER interface service CUSTOM80 CUSTOM81
nat (inside,outside) source static SERVER interface service CUSTOM81 CUSTOM80
!
no access-list outside_access_in extended permit tcp any object SERVER eq 80
access-list outside_access_in extended permit tcp any object SERVER eq 81
access-group outside_access_in in interface outside
!
packet-tracer input outside tcp 8.8.8.8 81 96.89.224.197 80
====================================================================
This is the config you just put them earlier change them as describe above. I test them in lab enviroment you should be ok now.
Manual NAT Policies (Section 1)
1 (inside) to (outside) source static Utility1 interface service CUSTOM80 CUSTOM81
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-22-2019 06:31 AM
Looks like we got it!
I had to modify your latest changes a little bit:
From:
nat (inside,outside) source static SERVER interface service CUSTOM81 CUSTOM80
To:
nat (inside,outside) 1 source static SERVER interface service CUSTOM81 CUSTOM80
That combined with the ACLs worked! So to put it all in one place:
object network Utility1
host 10.1.1.79
!
access-list outside_access_in extended permit tcp any object Utility1 eq 81
!
nat (inside,outside) 1 source static Utility1 interface service CUSTOM81 CUSTOM80
!
access-group outside_access_in in interface outside
Thank you so much for your help!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-22-2019 06:43 AM
Thank you.
- « Previous
-
- 1
- 2
- Next »
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide