- Cisco Community
- Technology and Support
- Security
- Network Security
- I have another piece to the
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-23-2017 06:29 AM - edited 03-12-2019 02:24 AM
I am having a very strange issue. Initially I thought this was a simple fix...5 hours later i am still in the same predicament. I am simply trying to use an ASA 5505 as a router. Why not use a router you ask, unfortunately I do not have that option. The ASA is running 9.2(4) code. We have another ASA on the remote end (5512 running the same code) and it works as expected routing traffic from the outside interface to the inside and vice versa. I have created ACL's allowing any any still to no avail. Attached is a drawing of the connectivity and the config file from the ASA in question. Any assistance would be greatly appreciated.
xlate per-session deny tcp any4 any4
xlate per-session deny tcp any4 any6
xlate per-session deny tcp any6 any4
xlate per-session deny tcp any6 any6
xlate per-session deny udp any4 any4 eq domain
xlate per-session deny udp any4 any6 eq domain
xlate per-session deny udp any6 any4 eq domain
xlate per-session deny udp any6 any6 eq domain
passwd 2KFQnbNIdI.2KYOU encrypted
names
name 10.1.1.0 House-1
name 10.2.1.0 House-2
!
interface Ethernet0/0
switchport access vlan 2
!
interface Ethernet0/1
!
interface Ethernet0/2
!
interface Ethernet0/3
!
interface Ethernet0/4
!
interface Ethernet0/5
!
interface Ethernet0/6
!
interface Ethernet0/7
!
interface Vlan1
nameif private
security-level 100
ip address 192.168.1.250 255.255.255.0
!
interface Vlan2
nameif engineering
security-level 100
ip address 10.3.200.31 255.255.255.0
!
boot system disk0:/asa924-k8.bin
ftp mode passive
clock timezone CST -6
clock summer-time EDT recurring
same-security-traffic permit inter-interface
same-security-traffic permit intra-interface
object network House-1
subnet 10.1.1.0 255.255.255.0
description Created during name migration
object network House-2
subnet 10.2.1.0 255.255.255.0
description Created during name migration
object-group network DM_INLINE_NETWORK_1
network-object object House-1
network-object object House-2
object-group service DM_INLINE_TCP_1 tcp
port-object eq 2626
port-object eq 2627
object-group service DM_INLINE_TCP_2 tcp
port-object eq 2626
port-object eq 2627
object-group network DM_INLINE_NETWORK_2
network-object host 10.3.201.165
network-object host 10.3.201.37
network-object host 10.3.201.38
object-group network DM_INLINE_NETWORK_3
network-object host 10.3.201.164
network-object host 10.3.201.37
network-object host 10.3.201.38
access-list cap extended permit icmp 10.0.0.0 255.0.0.0 any
access-list private_access_in remark Automation Timecode
access-list private_access_in extended permit ip 192.168.1.0 255.255.255.0 any4
access-list private_access_in extended permit ip any any
access-list in_engineering extended permit ip any any
pager lines 24
logging enable
logging timestamp
logging buffer-size 40960
logging buffered warnings
logging asdm informational
mtu private 1500
mtu engineering 1500
no failover
icmp unreachable rate-limit 1 burst-size 1
icmp permit any private
icmp permit any engineering
no asdm history enable
arp timeout 14400
no arp permit-nonconnected
access-group private_access_in in interface private
access-group in_engineering in interface engineering
route engineering 0.0.0.0 0.0.0.0 10.3.200.1 1
route engineering 192.168.9.0 255.255.255.0 10.3.200.1 1
timeout xlate 3:00:00
timeout pat-xlate 0:00:30
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
dynamic-access-policy-record DfltAccessPolicy
user-identity default-domain LOCAL
no threat-detection basic-threat
no threat-detection statistics access-list
no threat-detection statistics tcp-intercept
ntp server 10.1.1.17 source engineering prefer
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum 2048
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect sqlnet
inspect skinny
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
inspect icmp
inspect icmp error
inspect esmtp
inspect ip-options
!
service-policy global_policy global
prompt hostname context
no call-home reporting anonymous
Cryptochecksum:c16a8714e9850302ee5a66536bac6edc
: end
ASA# sh activation-key
Running Permanent Activation Key: 0xc318c05a 0x58dc1d04 0x445265dc 0x83c83870 0x0b0822b4
Licensed features for this platform:
Maximum Physical Interfaces : 8 perpetual
VLANs : 20 DMZ Unrestricted
Dual ISPs : Enabled perpetual
VLAN Trunk Ports : 8 perpetual
Inside Hosts : Unlimited perpetual
Failover : Active/Standby perpetual
Encryption-DES : Enabled perpetual
Encryption-3DES-AES : Enabled perpetual
AnyConnect Premium Peers : 2 perpetual
AnyConnect Essentials : Disabled perpetual
Other VPN Peers : 25 perpetual
Total VPN Peers : 25 perpetual
Shared License : Disabled perpetual
AnyConnect for Mobile : Disabled perpetual
AnyConnect for Cisco VPN Phone : Disabled perpetual
Advanced Endpoint Assessment : Disabled perpetual
UC Phone Proxy Sessions : 2 perpetual
Total UC Proxy Sessions : 2 perpetual
Botnet Traffic Filter : Disabled perpetual
Intercompany Media Engine : Disabled perpetual
Cluster : Disabled perpetual
This platform has an ASA 5505 Security Plus license.
The flash permanent activation key is the SAME as the running permanent key.
Solved! Go to Solution.
- Labels:
-
NGFW Firewalls
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-23-2017 01:52 PM
Yeah I have asked them 3 times to verify that..they ensure me that is all correct. Guess I will need to validate myself. The capture shows inbound but no outbound.
access-list cap line 1 extended permit ip any4 any4 (hitcnt=23914)
capture capin type raw-data access-list cap interface engineering
5505# sh cap capin | inc 10.1.4.41
3: 15:46:33.275040 802.1Q vlan#2 P0 10.1.4.41 > 192.168.1.101: icmp: echo request
73: 15:46:35.274994 802.1Q vlan#2 P0 10.1.4.41 > 192.168.1.101: icmp: echo request
145: 15:46:37.274994 802.1Q vlan#2 P0 10.1.4.41 > 192.168.1.101: icmp: echo request
208: 15:46:39.274949 802.1Q vlan#2 P0 10.1.4.41 > 192.168.1.101: icmp: echo request
258: 15:46:41.275010 802.1Q vlan#2 P0 10.1.4.41 > 192.168.1.101: icmp: echo request
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-23-2017 02:04 PM
It is a bit of a puzzle this one :)
Can't think of anything else at the moment. If the ASA can ping 192.168.1.x clients then it looks like the internal switch connectivity is fine.
If anything else comes to mind I'll post back.
Jon
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-23-2017 02:07 PM
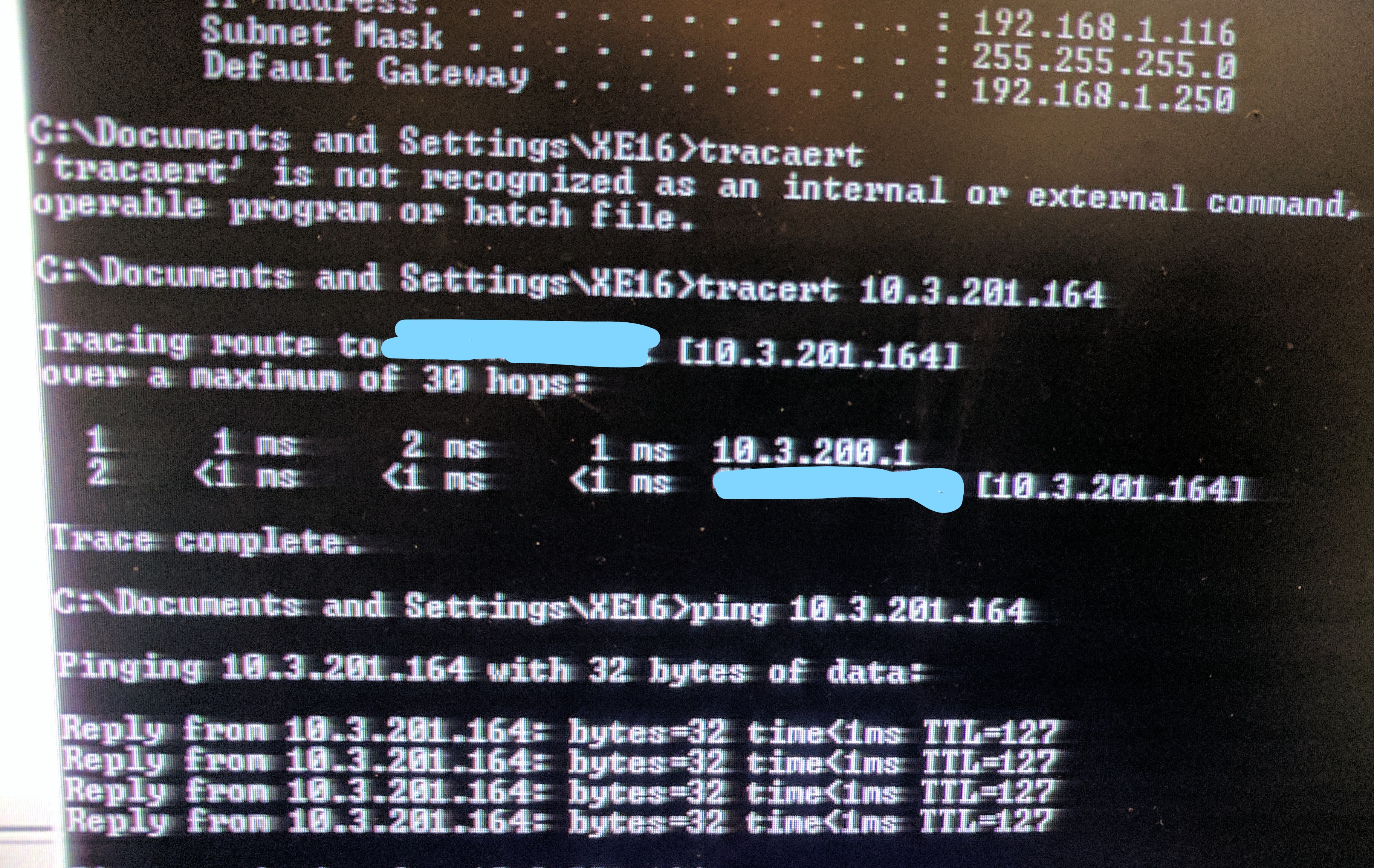
I have another piece to the puzzle that only makes things even more confusing...
There is a subnet (who's SVI is on the same core switch) that can reach the 192.168.1.x network both ways. 10.3.201.x. I attached a couple screenshots they took.

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-23-2017 02:29 PM
This is as you say even more confusing now.
So the ASA can route traffic assuming it is simply not showing in the traceoute which it won't do by default as I understand it.
And looking at the screenshot the default gateway for that 192.168.1.x client is set correctly.
You said in an earlier post you could not ping the inside devices from the 10.3.200.1 IP on the core switch so can you try that ping to this specific client ie. 192.168.1.116 and see what happens ?
Jon
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-24-2017 08:25 AM
Ok, so it looks like, of the IP'd devices on the "inside" of the 5505 (192.168.1.x) may in fact have a mis-configuration though I was assured that all was well...
That address (1.116) is reachable through the whole path..it is the only one of mess..seen by the ASA..
Thanks for all the tips!!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-24-2017 08:32 AM
No problem, thanks for letting me know.
Jon
- « Previous
-
- 1
- 2
- Next »
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide
