- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: ASA 5520 - Cannot Ping LAN
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-31-2020 09:13 AM
Greetings,
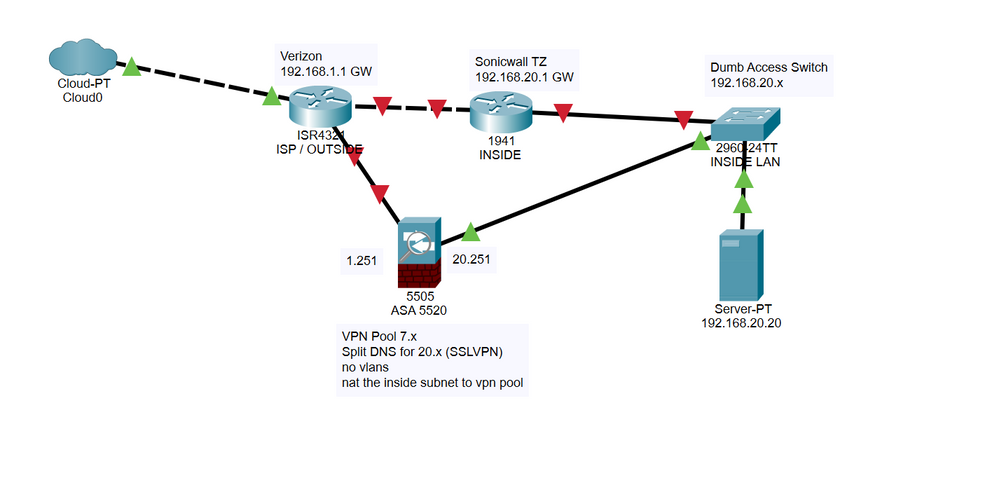
I recently acquired a 5520 ASA. I'm trying to integrate it into my environment but I am having a few issues.
When I connect with my Anyconnect Client, I can ping my inside LAN GW (even pull up the web interface), but nothing else. I have a pi sitting at 20.20 that I can ping from the ASA, the inside GW and another machine on the same switch. I included a drawling. Eventually the Sonicwall is going away, but I want to make sure this works before I remove it.
# show run int
interface GigabitEthernet0/0
description *** OUTSIDE TO VERIZON ***
nameif outside
security-level 0
ip address 192.168.1.251 255.255.255.0
!
interface GigabitEthernet0/2
description *** INSIDE TO CORP ***
nameif inside
security-level 100
ip address 192.168.20.251 255.255.255.0
!
show nat
Manual NAT Policies (Section 1)
1 (inside) to (outside) source static CORP-NETWORK CORP-NETWORK destination static VPN_SUBNET VPN_SUBNET no-proxy-arp route-lookup
translate_hits = 22, untranslate_hits = 22
show access-list
access-list cached ACL log flows: total 0, denied 0 (deny-flow-max 4096) alert-interval 300 e (hitcnt=0) (inactive) 0xf81403c3
access-list PINGIN; 1 elements; name hash: 0xa8b99bba
access-list PINGIN line 1 extended permit ip interface outside any (hitcnt=0) 0x b6e7e1e5
access-list VPN-ACL; 1 elements; name hash: 0xb17dd697
access-list VPN-ACL line 1 standard permit 192.168.20.0 255.255.255.0 (hitcnt=0) 0xa3eb35ff
access-list AnyConnect_Client_Local_Print; 8 elements; name hash: 0xe76ce9d1
access-list AnyConnect_Client_Local_Print line 1 extended permit tcp any4 any4 e q lpd (hitcnt=0) 0xf431783b
access-list AnyConnect_Client_Local_Print line 2 remark IPP: Internet Printing P rotocol
access-list AnyConnect_Client_Local_Print line 3 extended permit tcp any4 any4 e q 631 (hitcnt=0) 0x0a055e45
access-list AnyConnect_Client_Local_Print line 4 extended deny ip any4 any4 inac tive (hitcnt=0) (inactive) 0x1431053a
access-list AnyConnect_Client_Local_Print line 5 remark Windows' printing port
access-list AnyConnect_Client_Local_Print line 6 extended permit tcp any4 any4 e q 9100 (hitcnt=0) 0x077d9659
access-list AnyConnect_Client_Local_Print line 7 remark mDNS: multicast DNS prot ocol
access-list AnyConnect_Client_Local_Print line 8 extended permit udp any4 host 2 24.0.0.251 eq 5353 (hitcnt=0) 0xaad2a11b
access-list AnyConnect_Client_Local_Print line 9 remark LLMNR: Link Local Multic ast Name Resolution protocol
access-list AnyConnect_Client_Local_Print line 10 extended permit udp any4 host 224.0.0.252 eq 5355 (hitcnt=0) 0xbf7a7137
access-list AnyConnect_Client_Local_Print line 11 remark TCP/NetBIOS protocol
access-list AnyConnect_Client_Local_Print line 12 extended permit tcp any4 any4 eq 137 (hitcnt=0) 0xe657df61
access-list AnyConnect_Client_Local_Print line 13 extended permit udp any4 any4 eq netbios-ns (hitcnt=0) 0x3094a846
access-list NONAT; 1 elements; name hash: 0xf0d9f49a
access-list NONAT line 1 extended permit ip 192.168.20.0 255.255.255.0 192.168.7 .0 255.255.255.0 (hitcnt=0) 0x627e57f0
access-list global_access; 1 elements; name hash: 0xbd6c87a7
access-list global_access line 1 extended permit ip any any (hitcnt=1) 0x7b3c791 8
access-list inside_access_in; 5 elements; name hash: 0x433a1af1
access-list inside_access_in line 1 extended permit object-group DM_INLINE_SERVI CE_2 any any log debugging interval 300 (hitcnt=3) 0x2f1c4c5a
access-list inside_access_in line 1 extended permit ip any any log debugging i nterval 300 (hitcnt=3) 0xa925365e
access-list inside_access_in line 1 extended permit icmp any any echo log debu gging interval 300 (hitcnt=0) 0x925f140d
access-list inside_access_in line 1 extended permit icmp any any echo-reply lo g debugging interval 300 (hitcnt=0) 0xb2f4960f
access-list inside_access_in line 1 extended permit udp any any log debugging interval 300 (hitcnt=0) 0xbe4631fd
access-list inside_access_in line 1 extended permit tcp any any log debugging interval 300 (hitcnt=0) 0x60587b1a
access-list outside_access_in_1; 5 elements; name hash: 0x202ecf4e
access-list outside_access_in_1 line 1 extended permit object-group DM_INLINE_SERVICE_4 any any log debugging interval 300 (hitcnt=5) 0x94aad450
access-list outside_access_in_1 line 1 extended permit ip any any log debugging interval 300 (hitcnt=5) 0xee5759b0
access-list outside_access_in_1 line 1 extended permit tcp any any log debugging interval 300 (hitcnt=0) 0x7c6c5f5c
access-list outside_access_in_1 line 1 extended permit icmp any any echo log debugging interval 300 (hitcnt=0) 0x9f941417
access-list outside_access_in_1 line 1 extended permit icmp any any echo-reply log debugging interval 300 (hitcnt=0) 0xff3aebe8
access-list outside_access_in_1 line 1 extended permit udp any any log debugging interval 300 (hitcnt=0) 0xec3f24d5
access-list outside_access_out_1; 5 elements; name hash: 0x1e937888
access-list outside_access_out_1 line 1 extended permit object-group DM_INLINE_SERVICE_3 any any log debugging interval 300 (hitcnt=1) 0xc39fcf26
access-list outside_access_out_1 line 1 extended permit ip any any log debugging interval 300 (hitcnt=1) 0x1ae2e01f
access-list outside_access_out_1 line 1 extended permit icmp any any echo log debugging interval 300 (hitcnt=0) 0x6b2e6d15
access-list outside_access_out_1 line 1 extended permit icmp any any echo-reply log debugging interval 300 (hitcnt=0) 0x7b0b0fbd
access-list outside_access_out_1 line 1 extended permit tcp any any log debugging interval 300 (hitcnt=0) 0xfad1344e
access-list outside_access_out_1 line 1 extended permit udp any any log debugging interval 300 (hitcnt=0) 0x79076482
show run access-group
access-group outside_access_in_1 in interface outside
access-group outside_access_out_1 out interface outside
access-group inside_access_in in interface inside
access-group global_access global
show route ***7.2 is myself anyconnect client
Gateway of last resort is 192.168.1.1 to network 0.0.0.0
C 192.168.20.0 255.255.255.0 is directly connected, inside
S 192.168.7.2 255.255.255.255 [1/0] via 192.168.1.1, outside
C 192.168.1.0 255.255.255.0 is directly connected, outside
S* 0.0.0.0 0.0.0.0 [1/0] via 192.168.1.1, outside
***ping 20.20 (server inside)
packet-tracer input outside icmp 192.168.7.1 8 0 192.168.20.20
Phase: 4
Type: UN-NAT
Subtype: static
Result: ALLOW
Config:
nat (inside,outside) source static CORP-NETWORK CORP-NETWORK destination static VPN_SUBNET VPN_SUBNET no-proxy-arp route-lookup
Additional Information:
NAT divert to egress interface inside
Untranslate 192.168.20.20/0 to 192.168.20.20/0
Phase: 5
Type: ACCESS-LIST
Subtype: log
Result: ALLOW
Config:
access-group outside_access_in_1 in interface outside
access-list outside_access_in_1 extended permit object-group DM_INLINE_SERVICE_4 any any log debugging
object-group service DM_INLINE_SERVICE_4
service-object ip
service-object tcp
service-object icmp echo
service-object icmp echo-reply
service-object udp
Additional Information:
Forward Flow based lookup yields rule:
in id=0x74560398, priority=13, domain=permit, deny=false
hits=5, user_data=0x70ff2a80, cs_id=0x0, use_real_addr, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=0
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=0, dscp=0x0
input_ifc=outside, output_ifc=any
Phase: 9
Type: INSPECT
Subtype: np-inspect
Result: ALLOW
Config:
class-map inspection_default
match default-inspection-traffic
policy-map global_policy
class inspection_default
inspect icmp
service-policy global_policy global
Additional Information:
Forward Flow based lookup yields rule:
in id=0x748de9a8, priority=70, domain=inspect-icmp, deny=false
hits=370, user_data=0x757088d8, cs_id=0x0, use_real_addr, flags=0x0, protocol=1
src ip/id=0.0.0.0, mask=0.0.0.0, icmp-type=0, tag=0
dst ip/id=0.0.0.0, mask=0.0.0.0, icmp-code=0, tag=0, dscp=0x0
input_ifc=outside, output_ifc=any
Result:
input-interface: outside
input-status: up
input-line-status: up
output-interface: inside
output-status: up
output-line-status: up
Action: allow
icmp debugging
When I ping (3x) from AnyConnect Pool to Inside Host 20.20
ICMP echo request from outside:192.168.7.2 to inside:192.168.20.20 ID=556 seq=1 len=56
ICMP echo request from outside:192.168.7.2 to inside:192.168.20.20 ID=558 seq=1 len=56
ICMP echo request from outside:192.168.7.2 to inside:192.168.20.20 ID=559 seq=1 len=56
sho log
%ASA-7-609001: Built local-host outside:192.168.1.18
%ASA-6-302013: Built inbound TCP connection 40825 for outside:192.168.1.18/45230 (192.168.1.18/45230) to inside:192.168.20.20/853 (192.168.20.20/853)
%ASA-6-302020: Built inbound ICMP connection for faddr 192.168.7.2/561(LOCAL\TestUser) gaddr 192.168.20.20/0 laddr 192.168.20.20/0 (TestUser)
%ASA-6-302021: Teardown ICMP connection for faddr 192.168.7.2/561(LOCAL\TestUser) gaddr 192.168.20.20/0 laddr 192.168.20.20/0 (TestUser)
%ASA-6-302020: Built inbound ICMP connection for faddr 192.168.7.2/562(LOCAL\TestUser) gaddr 192.168.20.20/0 laddr 192.168.20.20/0 (TestUser)
%ASA-6-302021: Teardown ICMP connection for faddr 192.168.7.2/562(LOCAL\TestUser) gaddr 192.168.20.20/0 laddr 192.168.20.20/0 (TestUser)
%ASA-6-302020: Built inbound ICMP connection for faddr 192.168.7.2/563(LOCAL\TestUser) gaddr 192.168.20.20/0 laddr 192.168.20.20/0 (TestUser)
%ASA-6-302021: Teardown ICMP connection for faddr 192.168.7.2/563(LOCAL\TestUser) gaddr 192.168.20.20/0 laddr 192.168.20.20/0 (TestUser)
%ASA-6-302016: Teardown UDP connection 40819 for outside:192.168.7.2/34593(LOCAL\TestUser) to inside:192.168.20.20/53 duration 0:02:01 bytes 40 (TestUser)
ping 20.1 (Inside Sonicwall GW from AnyConnect Client)
icmp-debuging
When I ping (3x) from AnyConnect Pool to Inside GW 20.1
ICMP echo request from outside:192.168.7.2 to inside:192.168.20.1 ID=579 seq=1 len=56
ICMP echo reply from inside:192.168.20.1 to outside:192.168.7.2 ID=579 seq=1 len=56
ICMP echo request from outside:192.168.7.2 to inside:192.168.20.1 ID=580 seq=1 len=56
ICMP echo reply from inside:192.168.20.1 to outside:192.168.7.2 ID=580 seq=1 len=56
ICMP echo request from outside:192.168.7.2 to inside:192.168.20.1 ID=581 seq=1 len=56
ICMP echo reply from inside:192.168.20.1 to outside:192.168.7.2 ID=581 seq=1 len=56
sho log
%ASA-7-609001: Built local-host inside:192.168.20.1
%ASA-6-302020: Built inbound ICMP connection for faddr 192.168.7.2/579(LOCAL\TestUser) gaddr 192.168.20.1/0 laddr 192.168.20.1/0 (TestUser)
%ASA-6-302021: Teardown ICMP connection for faddr 192.168.7.2/579(LOCAL\TestUser) gaddr 192.168.20.1/0 laddr 192.168.20.1/0 (TestUser)
%ASA-7-609002: Teardown local-host inside:192.168.20.1 duration 0:00:00
%ASA-7-609001: Built local-host inside:192.168.20.1
%ASA-6-302020: Built inbound ICMP connection for faddr 192.168.7.2/580(LOCAL\TestUser) gaddr 192.168.20.1/0 laddr 192.168.20.1/0 (TestUser)
%ASA-6-302021: Teardown ICMP connection for faddr 192.168.7.2/580(LOCAL\TestUser) gaddr 192.168.20.1/0 laddr 192.168.20.1/0 (TestUser)
%ASA-7-609002: Teardown local-host inside:192.168.20.1 duration 0:00:00
%ASA-7-609001: Built local-host inside:192.168.20.1
%ASA-6-302020: Built inbound ICMP connection for faddr 192.168.7.2/581(LOCAL\TestUser) gaddr 192.168.20.1/0 laddr 192.168.20.1/0 (TestUser)
%ASA-6-302021: Teardown ICMP connection for faddr 192.168.7.2/581(LOCAL\TestUser) gaddr 192.168.20.1/0 laddr 192.168.20.1/0 (TestUser)
%ASA-7-609002: Teardown local-host inside:192.168.20.1 duration 0:00:00
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-31-2020 12:48 PM
IN sonic wall you need to enter static route that for 7.x what will be next hop 20.251
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-31-2020 09:53 AM
Maybe I need to set a route on the Sonicwall?
The default gateway to the 20.20 (pi/server) is the 20.1 Sonicwall gateway. Do I need to tell the Sonicwall where to reach 7.x (anyconnect client pool) which is through 20.251 (inside int on ASA)? Or does the packet get told that the client is 20.252 (the asa) when it leaves and goes to the internal network?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-31-2020 10:41 AM
You need a static route also pointing back to FW.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-31-2020 10:47 AM - edited 12-31-2020 10:48 AM
Do you mean, a static route on the Sonicwall FW router? Or the ASA FW? pointing from what to what? the vpn 7.x to 20.251 (the asa inside ip)? or inside 20.x to 20.251 (the asa) Do I need to deal with the Verizon router as well, telling it where the 7.x network is 1.251)? Can you explain or give examples?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-31-2020 12:48 PM
IN sonic wall you need to enter static route that for 7.x what will be next hop 20.251
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-31-2020 01:03 PM
That did it. I added a route policy for source any, dest ASAVPNPOOL (range), service any, gateway ASAInsideIntIP, interface x0(lan), Metric 1
Per here
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide