- Cisco Community
- Technology and Support
- Security
- Network Security
- ASA 5525 ICMP Bypass not working
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-17-2018 06:01 AM - edited 02-21-2020 08:34 AM
Hello everyone. I have a problem that has to be solved immediately. I took photo from cisco webpage that is identical to my design on particular interface. just the ip addresses are different but i will ask using ip addresses in the photo.
So requirement is this way:
192.168.1.10 <---> 192.168.2.10 ICMP
192.168.1.10 <---> 192.168.2.10 80
192.168.1.10 <---> 192.168.2.10 443
But as you already understood initial traffic goes from router into server directly and answer comes through ASA and it creates problem. I permitted all possible reply traffic for all 3 protocol. And bypassed each of them through service policy. HTTP and HTTPS worked properly but 192.168.1.10 cannot ping 192.168.2.10. I tried different access-lists but no result. Finally i even permitted traffic from 192.168.2.10 into 192.168.1.10 with IP services and bypassed all IP services but ping still not working.
In my case 192.168.2.10 is 10.124.49.5 and 192.168.1.10 is 10.124.41.104. As you see from ss that even acl hits are recorded. But ping is not working.
What can be a problem?
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-17-2018 09:41 PM
Soo, I can solve the problem by disabling inspection from global policy. Creating new class unders global policy map which no matching interesting traffic and matching any any and inspect. This way i eleminated by reply traffic from inspection and all other stuff still inspected
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-17-2018 06:11 AM
Hi Orkhan,
enable ICMP inspection in service policy.
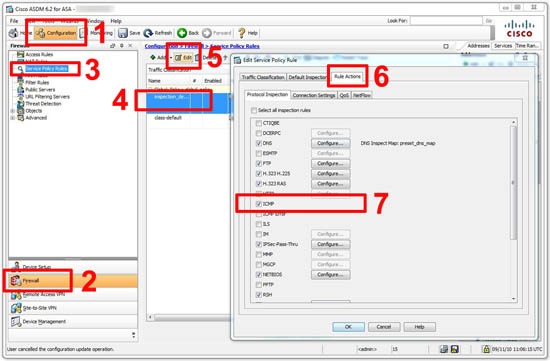
ref - https://www.petenetlive.com/KB/Article/0000351
*** Pls rate all useful responses ***
Good Luck
Good luck
KB
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-17-2018 06:21 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-17-2018 06:25 AM
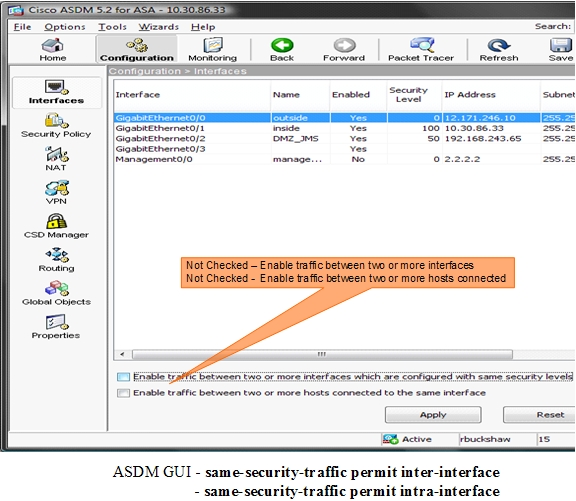
2 - allow intra and inter same security level traffic
Good luck
KB
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-17-2018 07:49 AM
As @Kasun Bandara suggested enter the command - same-security-traffic permit intra-interface this is because you are routing to/from the same inside interface.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-17-2018 08:08 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-17-2018 08:24 AM
Good luck
KB
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-17-2018 08:58 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-17-2018 07:27 PM
Hi,
you can enable them as below capture. you can tick them and apply. also disable Host firewall in server.
Good luck
KB
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-17-2018 09:10 PM
I do not think that problem with OS of the server. Host Firewalls are disabled. When i disable ICMP inspection from global policy ping works. I mean my problem is that when inspection is enabled bypass settings not working for icmp traffic but works for tcp. All inter,intra, acl confs are done beforehand
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-17-2018 09:41 PM
Soo, I can solve the problem by disabling inspection from global policy. Creating new class unders global policy map which no matching interesting traffic and matching any any and inspect. This way i eleminated by reply traffic from inspection and all other stuff still inspected
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide


