- Cisco Community
- Technology and Support
- Security
- Network Security
- ASA failover with N7k and vPC
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
ASA failover with N7k and vPC
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-20-2014 02:27 PM - edited 03-11-2019 09:13 PM
Hi guys,
I'm connecting an ASAs as Active/standby failover to nexus 7000.
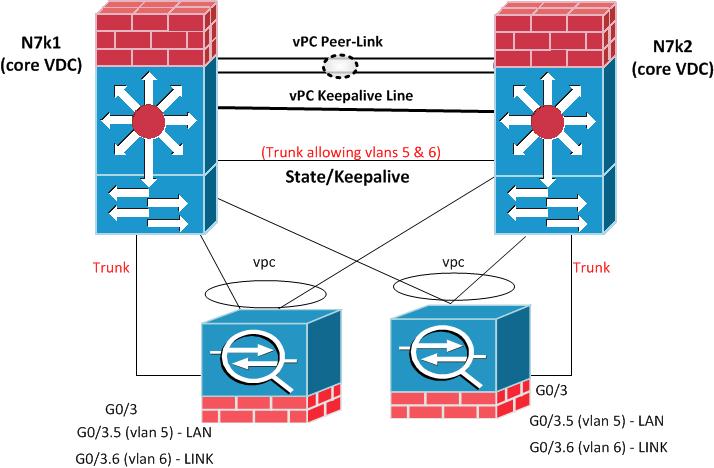
Please find the attached network diagram to understand the setup.
- No direct cable between the two ASAs.
- Failover link is done by connecting g0/3 to N7k1 and N7K2 (as the diagram).
- vPC peer-link is there between the two N7k.
- Using this setup, Failover is working fine. (Failover vlans are passing through vPC peer-link)
- As the recommendation, i understood that it is not recommended to use the vPC peer-link to pass the failover vlans (in our case vlan 5 and 6).
Is it true?
+ And based on this recommendation:
- I removed vlans 5 and 6 from the vPC peer-link.
- I created new link between the two N7ks "trunk" and allowed only vlans 5 & 6.
After doing this step, failover keep failing and both ASAs are not detecting each others.
Any idea how to solve this issue?
Regards
- Labels:
-
NGFW Firewalls
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-20-2014 02:56 PM
Can you share the running-config and status for the Nexus trunk interfaces (to each other and to the ASAs)?
i.e.,
show run int Eth__/__
show int Eth __/__
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-20-2014 03:12 PM
Hi Marvin,
I will collect show interface and send it, but now i have the following "show-run interfaces":
N7K-1:
interface Ethernet3/19
description ### ASA Failover , connected to N7k-2 ###
switchport
switchport mode trunk
switchport trunk allowed vlan 5,6
speed 1000
no shutdown
N7K-2:
interface Ethernet3/19
description ### ASA Failover , connected to N7k-1 ###
switchport
switchport mode trunk
switchport trunk allowed vlan 5,6
speed 1000
no shutdown
ASAs:
interface Ethernet3/5
description ### Connected to ASA-1 ###
switchport
switchport mode trunk
switchport trunk allowed vlan 5,6
speed 1000
interface Ethernet3/5
description ### Connected to ASA-2 ###
switchport
switchport mode trunk
switchport trunk allowed vlan 5,6
speed 1000
no shutdown
Regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-20-2014 03:16 PM
Those are pretty straightforward and one would expect them to work. Perhaps the information from the interfaces showing their current status will shed some light.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-20-2014 03:25 PM
Thanks for your reply.
As i remember all ports were up, anyhow, i will collect and share them.
Regards.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-21-2014 12:27 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-21-2014 06:05 AM
Hmm those look OK.
Can you "show spanning-tree vlan 5" ( and 6)? on the Nexus's?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-21-2014 07:41 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-21-2014 09:54 AM
For some reason both N7k-1 and N7k-2 are reporting they are root - as i f they still thought those VLANs were connected via vPC. Did you clear VLANs 5 and 6 from the the peer link?
If you look at N7k-2 it is blocking on Eth3/19 (the connection to N7k-1). That will keep the ASAs from seeing each other via that connection.
You might want to refer to this troubleshooting spanning-tree document for NX-OS.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-21-2014 10:14 AM
Hi Marvin,
Yes i removed those two vlans from the vPC peer link by removing them from the allowed vlans.
Regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-21-2014 10:34 AM
I'd engage the TAC to have a look at your spanning-tree setup in real time. It would probably resolve your issue more quickly to open a Service Request from CSC. There should be a link in the top right of your view with instruction on doing that.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-21-2014 12:17 PM
Hi Marvin,
Thanks for your reply.
- If i have an issue with spanning tree, why do you think it is working fine over vPV peer link?
- Both switches are active because we configured peer switch under vPC, and in this case both spanning tree priority should be same.
Regards,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-21-2014 04:31 PM
I suspected you had setup peer switch. When you have a VPC, the NX-OS uses a virtual bridge-ID designed to work with VPC and spanning tree isn't an issue. When you are running hybrid mode (see this link) Cisco recommends you set "spanning-tree pseudo information".
I've not done that myself which is why I defer to to and recommend engaging the TAC as I'd not want you to have unforeseen consequences with your 7k core as a result of something I had recommended.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide


