- Cisco Community
- Technology and Support
- Security
- Network Security
- In the HTTP preprocessor
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
ASA FirePOWER and PROXY
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-27-2015 07:38 AM - edited 03-12-2019 05:36 AM
I wonder if there are any clues that helps to extract as much information about users behind proxy as possible? We're migrating ASA 5520 to new ASA with firepower module, but there's a proxy on inside network, talking to ASA with WCCP. So source IP will be always single PROXY address, and domain username is also lost.
The only possibility I can see is extracting original client ip from X-Forwarded-For header. It can be a solution, but: On intrusion event tab I can add "Original Client IP" column ( this feature is not working by the way on my 5.3.1.1 (build 37) - field is always empty, even if I can see X-Forwarded-For in packet details ). Additionaly, on AMP submenu I can't see any place where "Original Client IP" could be viewed?
Placing Proxy behind any other interface than inside would be a nicer solution, but WCCP on ASA doesn't support it.
Would be grateful for any help
Lukas
- Labels:
-
NGIPS
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-03-2016 11:05 AM
Internet<--> IPS <-->Proxy <-->Client
if the proxy send client ip address with "X-Forwarded-Fo"r how can i read this information with sourcefire and when packet leaves from Sourcefire i want remove "X-Forwarded-For".
is that possible?
zafer
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-04-2016 10:24 AM
Hi,
Yes, we can disable this XFF information under Policy->Acces control->Network Analysis policy ->tcp preprocessor.
Rate if that helps.
Thanks,
Ankita
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-14-2020 07:47 AM
Hi @ankojha,
I know this is an old post but I was wondering if you could tell me where you found the option to remove the XFF from the header? Everything I see online seems to suggest it's not possible. I've gone into Policy > Access Control > Network Analysis Policy but I can't find "TCP preprocessor". Maybe it's changed over the years.
Were you able to remove the XFF field in recent versions of Firepower?
Many thanks in advance.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-04-2016 05:13 PM
Sourcefire (aka Firepower), at this time, does not have a way to strip the XFF header off the packet.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-27-2016 11:14 PM
I would recommend that you verify that "extract XFF" is enabled in the HTTP preprocessor.
~ Cheers
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-02-2016 05:45 AM
In the HTTP preprocessor turned on "Extract Original Client IP Address", but still see only Proxy's ip address in Analysis->Connections ->Events.
How to obtain original ip, not proxy's ???
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-27-2016 01:56 AM
Did you manage to solve this?
I have the same problem, "Extract Original Client IP Address" is enabled, but in event logs I still see only proxy IP as Initiator IP
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-04-2016 05:11 PM
The default headers that can be extracted from a packet are X-Forwarded-For and True-Client-IP. If you have a proxy using "Original Client IP Address" (confirm in the packet) then you can add this to the HTTP preprocessor.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-03-2017 08:45 AM
The Initiator IP will always be the proxy IP.
You can only filter now for the Original Client IP.
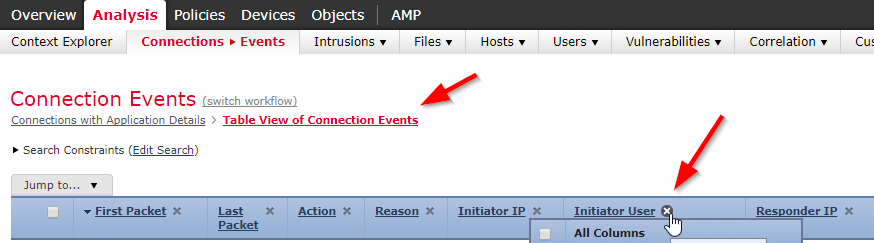
Analysis -> Connections -> Events -> Table View of Connection Events
Select the Original Client IP from the list.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-03-2017 11:44 PM
It depends of the size of GET request forwarded to source fire, if the size of GET request is larger than that default value then you might not able to see the original client IP though you have enabled "x-forwarded for" option under the HTTP preprocessor.
Take packet capture on the device and verify the size of GET request and then increase the client depth value under HTTP processor settings.
Let me know if it helps you.
Best
Jawed
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-27-2016 11:23 AM
I had this issue also. There are a couple of settings in the HTTP preprocessor.
Firepower 6.0
Go to Policies -> Access Control -> Network Analysis Policy (Top right of browers window).
Edit existing policy, or create new policy.
Policy information -> Settings -> HTTP Configuration
Under Targets click + to add a server and enter the IP address, CIDR, or comma-seperated list. Click OK.
Then check boxes "Detect HTTP Proxy Servers", "Allow HTTP Proxy use", and "Extract Original Client IP Address".
For mine I have "XFF Header Priority" with #1 "X-Forward-For"
Hope this helps.
-Bill
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-26-2016 10:56 AM
Hello Guys,
How can i enable "extract XFF" on FMC 6.1? I cannot find Network Analysis Policy section.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-06-2016 02:36 PM
It's been moved from the intrusion policy (<= 5.4.x) to the advanced tab in the access control policy.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide